Computer Science > Research Paper > University of Maryland, University College CYB 670 CYBERSECURITY POLICY AND BASELINE ANALYSIS REPO (All)
University of Maryland, University College CYB 670 CYBERSECURITY POLICY AND BASELINE ANALYSIS REPORT
Document Content and Description Below
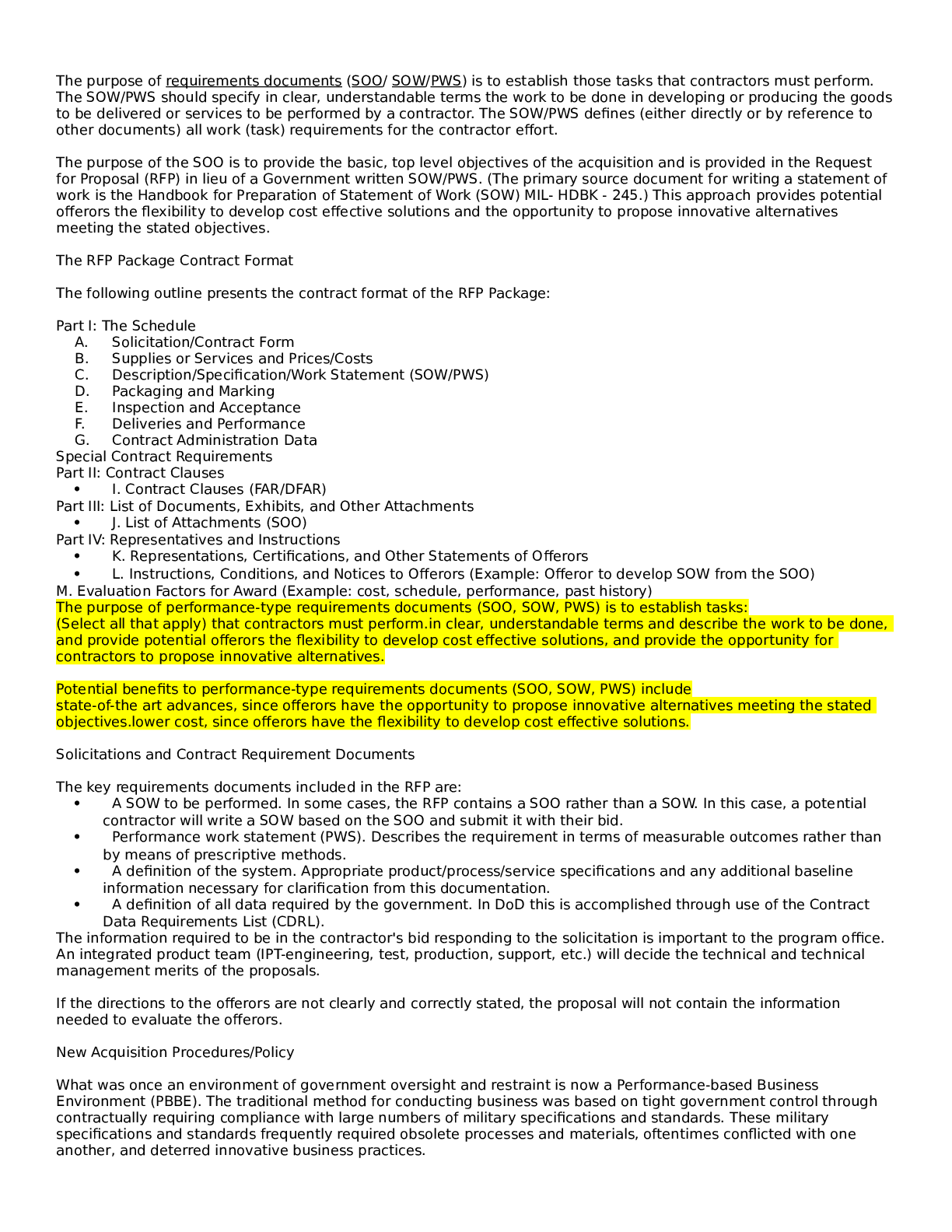
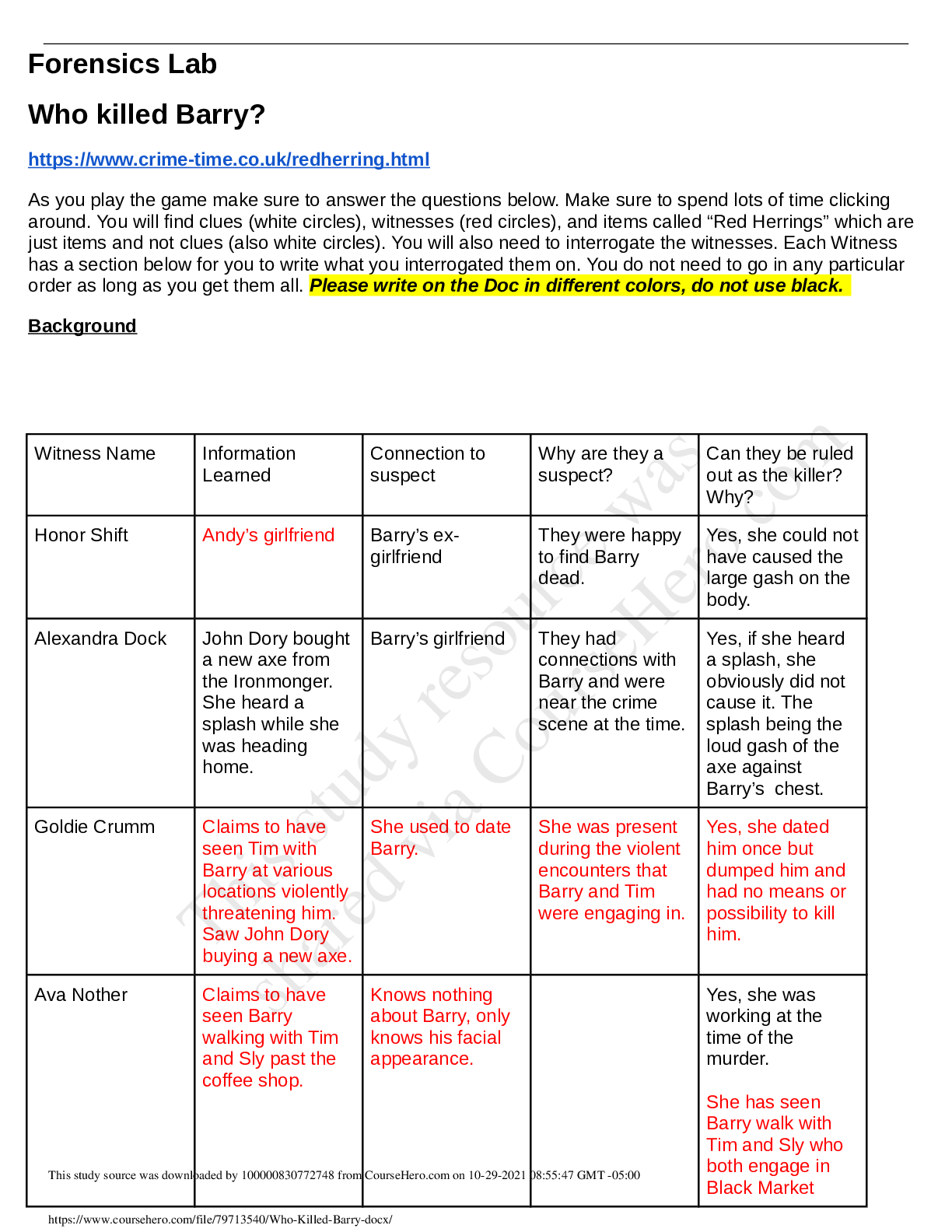
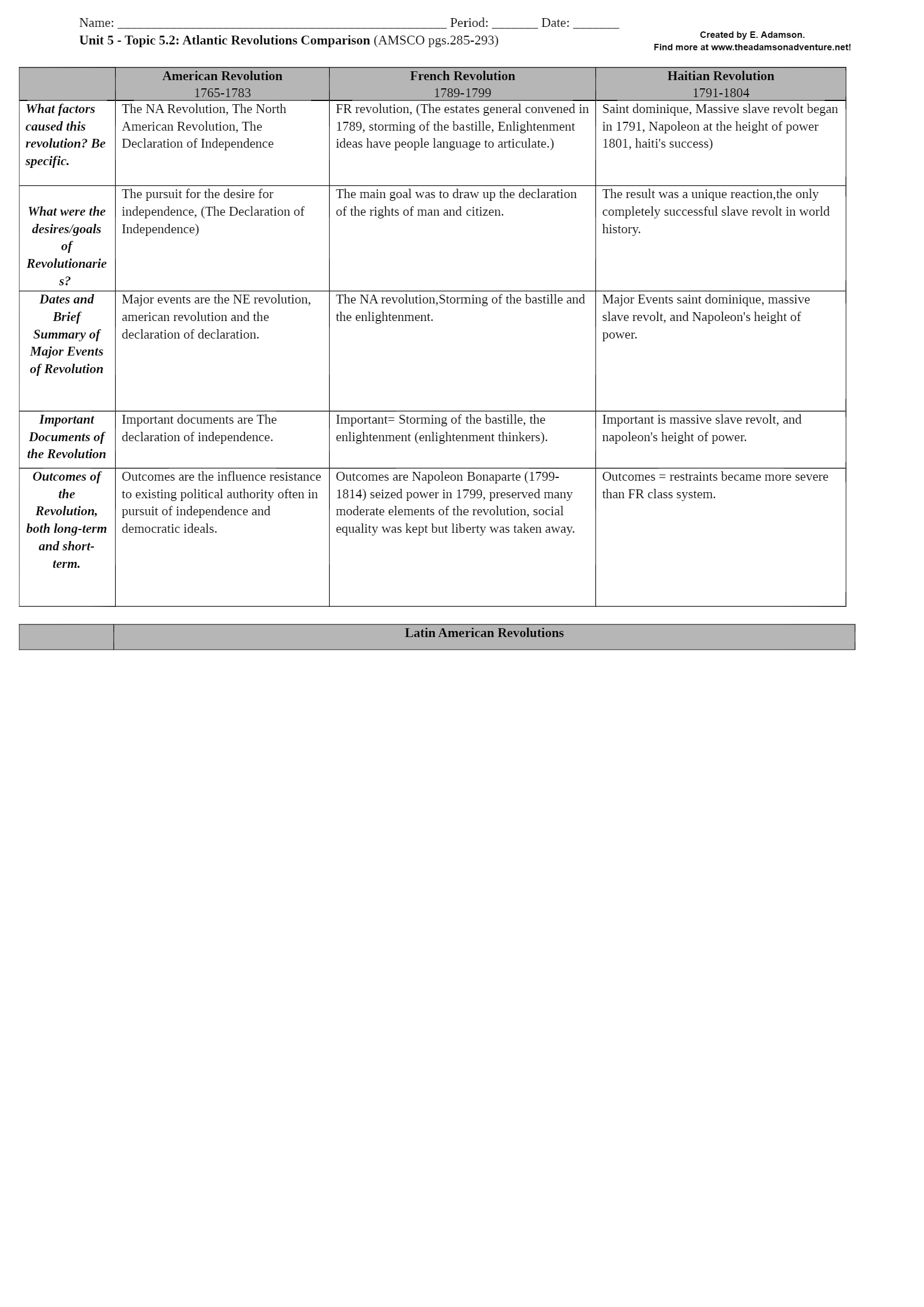
University of Maryland, University College CYB 670 CYBERSECURITY POLICY AND BASELINE ANALYSIS REPORT Cybersecurity Policy and Baseline Analysis Report CYB 670 University of Maryland Global Ca... mpus Team 2: Bob Peterson, Venice Richards, Ashley Wiggins, Dave Jones & Ohene Boadi 25 October 2020 Abstract The Chief Information Security Officer (CISO), tasked the team with the responsibility of conducting a baseline analysis for establishing a secure communications network for the forthcoming Five Eyes (FVEY), Global Economic Summit to be hosted in the United Kingdom. The FVEY are international partners that include the United States, United Kingdom, Canada, New Zealand, and Australia. As the team from Australia, the analysis required that the team conduct a multidisciplinary examination of the internal and external cyber environment of the country club hosting the summit. As a result of occasional spying, hacking and other security concerns, the team is tasked with ensuring a secured communication network is established and it must also interface between our head office’s networks in Australia. In addition, the secured communication network must allow access to Australia’s authorized users when using cellular phones, laptops, desktops, and tablets. For Australia’s participation in the summit, this analysis report examined the following that will be provided to the CISO: Cyber Policies instituted to address cybersecurity management and technology, an Attribution Report to the host of the summit, determining the bad actors, Chain of Custody form in order to legally track any digital evidence obtained, and International Security Policies comparison of the FVEY countries. The report also includes a Network Security Check List, a Security System Risk and Vulnerability Assessment, that provides information on equipment and assets used and any potential risks or vulnerabilities. The report concludes with a Digital Forensic Environment Review and Analysis, Transnational Legal Compliance Report as part of the International Standard Report demonstrating the legal and environmental position of each country involved. Table of Contents Overview4 Cyber Policy/Cyber Policy Matrix...4 Attribution Report9 Chain of Custody......13 International Security Policies Comparison.16 Network Security Methodology and Checklist...17 Security System Risk and Vulnerability Assessment.26 Security Baseline Report..31 Digital Forensic Environment Review and Analysis 39 Transnational Legal Compliance Report.....42 International Standard Report.43 Conclusion..46 References...47 CYBERSECURITY POLICY AND BASELINE ANALYSIS REPORT 4 Overview In preparation for the forthcoming Five Eyes (FVEY) Global Economic Summit in London, United Kingdom, the team from Australia has been given the responsibility for conducting a baseline analysis to ensure a secured communications network is established for this organization at the summit. Australia, the United States, the United Kingdom, Canada and New Zealand agreed to share the responsibility for surveillance, information collection and analysis under the FVEY agreement. Recent spying and hacking allegations require that the team set up a secured communication network for a variety of assets that can be accessed by authorized users. To achieve this, the team examined its country’s cybersecurity policies, as well as those from the other FVEY nations. The team also developed a security checklist to aid in identifying and mitigating system risks and vulnerabilities. Additionally, a chain of custody was developed to assist in the collection of any digital or forensic evidence. Finally, transnational compliance and international standard were reviewed to gain understanding of all the compliance requirements that overlap or are similar among all the FYEY nations. Cybersecurity Policy Matrix This policy cybersecurity matrix attempts to incorporate and provides a wide range of security measures measure than are in place to safeguard the security posture of Australia. The table provide an understanding and the applicability of such policies, standards and laws for the for Team. The tables also provide the other teams participating in the summit and understanding of these security policies. [Show More]
Last updated: 1 year ago
Preview 1 out of 55 pages

Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Nov 16, 2022
Number of pages
55
Written in
Additional information
This document has been written for:
Uploaded
Nov 16, 2022
Downloads
0
Views
91