Computer Science > Research Paper > University of Maryland, University College CYB 670 Project 4: Protecting the Homeland Risk Profile T (All)
University of Maryland, University College CYB 670 Project 4: Protecting the Homeland Risk Profile Team 1 – United States
Document Content and Description Below
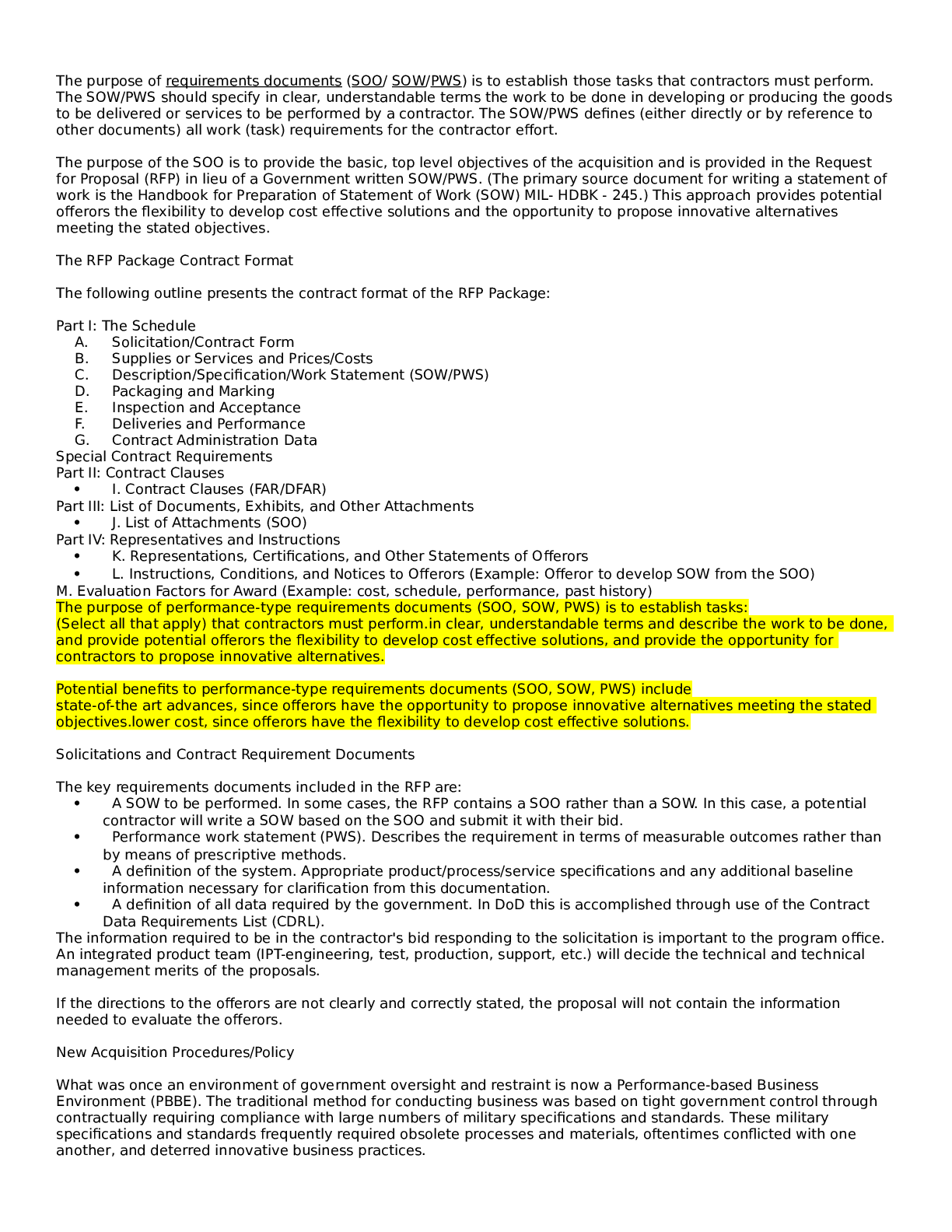
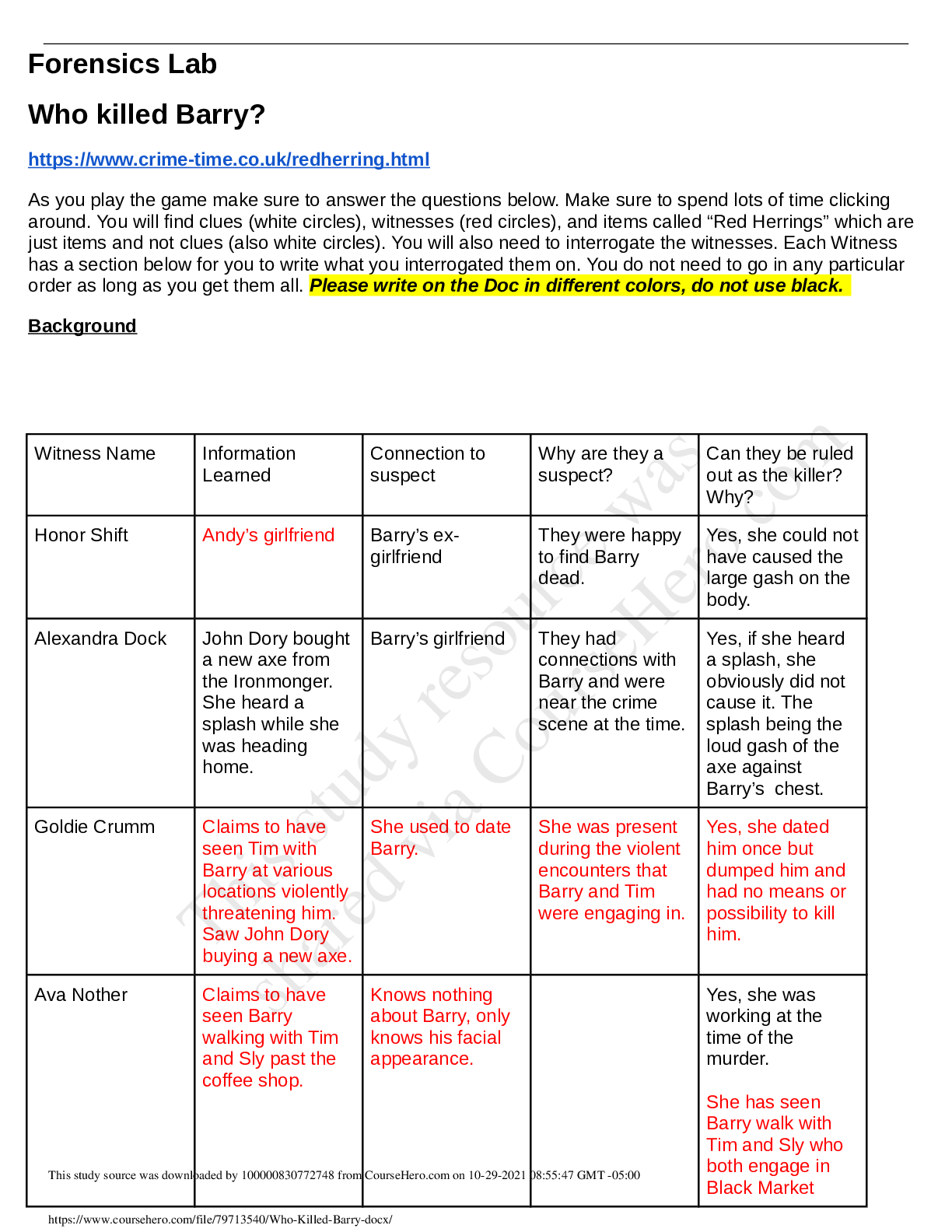
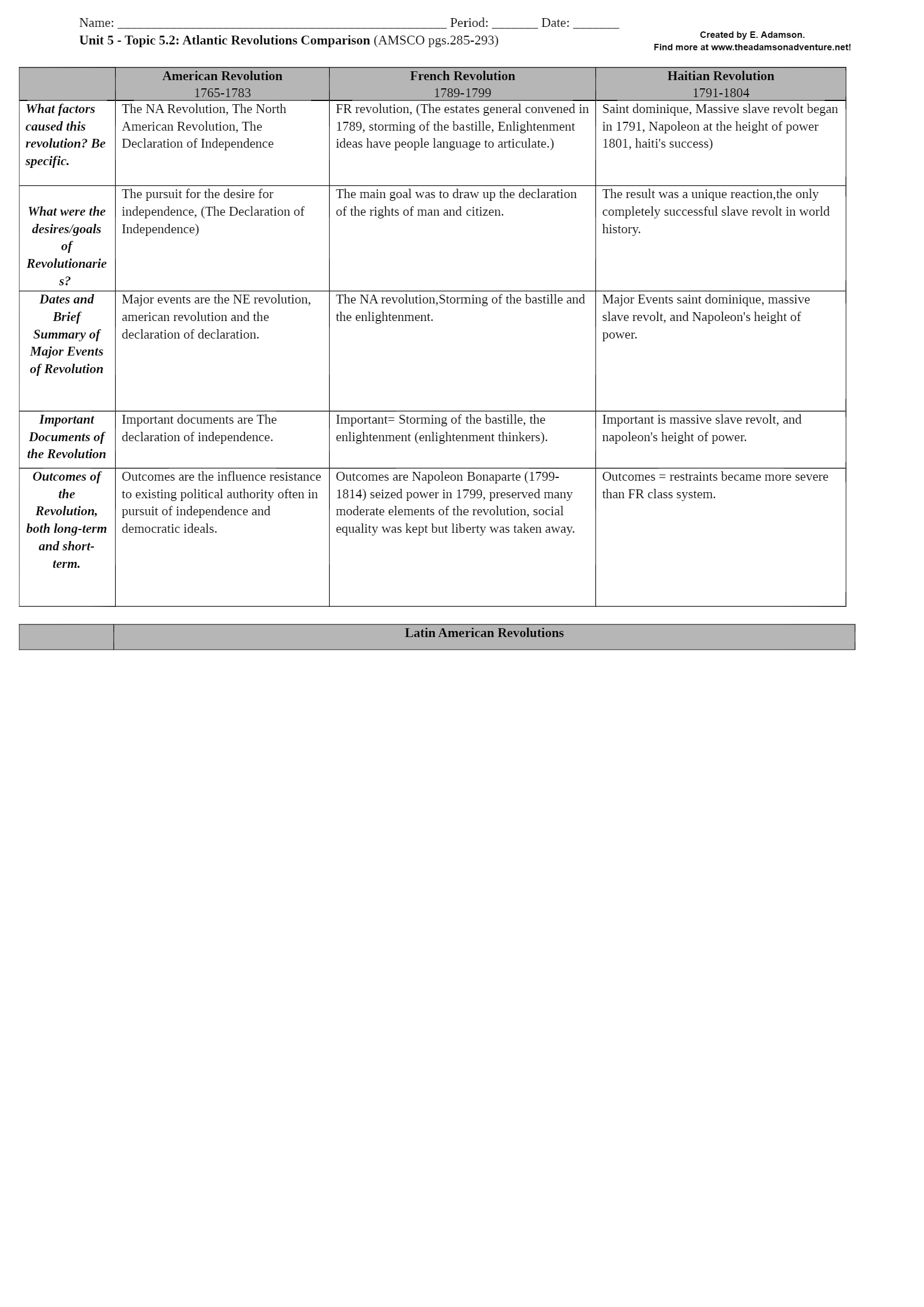
University of Maryland, University College CYB 670 Project 4: Protecting the Homeland Risk Profile Team 1 – United States CYB 670 Capstone in Cybersecurity University of Maryland University ... College RISK PROFILE Overview The United States Federal Government is continuously addressing the cyber threats from adversaries who target the Federal Government’s infrastructure on a daily basis. In order to mitigate these threats in a timely manner there needs to be a way to triage the severity of the threats. The most effective way to triage these threats is to establish a detailed Risk Profile that provides a hasty visualization of the potential cyber threat. It is important to note that the Risk Profile is not an extensive report, it is a quick snapshot of the threat. The intent is to provide a concise summarization of cyber threat in order to prioritize mitigation actions. As technology continues to advance in order to keep up with the demands of society, it is imperative that the Risk Profile is modified and updated to maintain its effectiveness. The following section provides an overview of the top three cyber threat risk profiles determined by the Federal Government. RISK PROFILE US Fed. Govt. Top 3 Cyber Threat Risk Profiles Name/Group: 1 Insider Threat Description: Technically any employee could be considered an internal threat. Key personnel that could potentially cause the most destruction would be Executives, Senior Managers, and System Administrators. Relationship: Internal Motive: Financially-based, Emotionally-based, Politically-based. Intent: Malicious, Deliberate, or Unknowingly. Capability: Too many unknown variables depending on the user’s role. Target Victim: United States Federal Government and/or associated organizations. Targeted Asset: Intellectual property and/or classified material. Action: Variable – ranging from deliberate exfiltration of data using privileged accesses to accidental exposure. Objective: Executives and Senior Managers: more often than not tend to be targets of SpearPhishing. But they are also more often than not responsible for deliberate data exfiltration when they leave an organization not on their terms. System Administrators: more often than not tend to abuse their access privileges and smuggle exfiltrated data through the use of unapproved devices. Standard Employee: more often than not are unknowingly involved in accidental data loss. [Show More]
Last updated: 1 year ago
Preview 1 out of 5 pages

Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Nov 16, 2022
Number of pages
5
Written in
Additional information
This document has been written for:
Uploaded
Nov 16, 2022
Downloads
0
Views
57