Computer Science > Research Paper > University of Maryland, University College • CYB 670 Project 1: Preparatory Lab Exercises CYB 670 (All)
University of Maryland, University College • CYB 670 Project 1: Preparatory Lab Exercises CYB 670 9040 Capstone in Cybersecurity
Document Content and Description Below
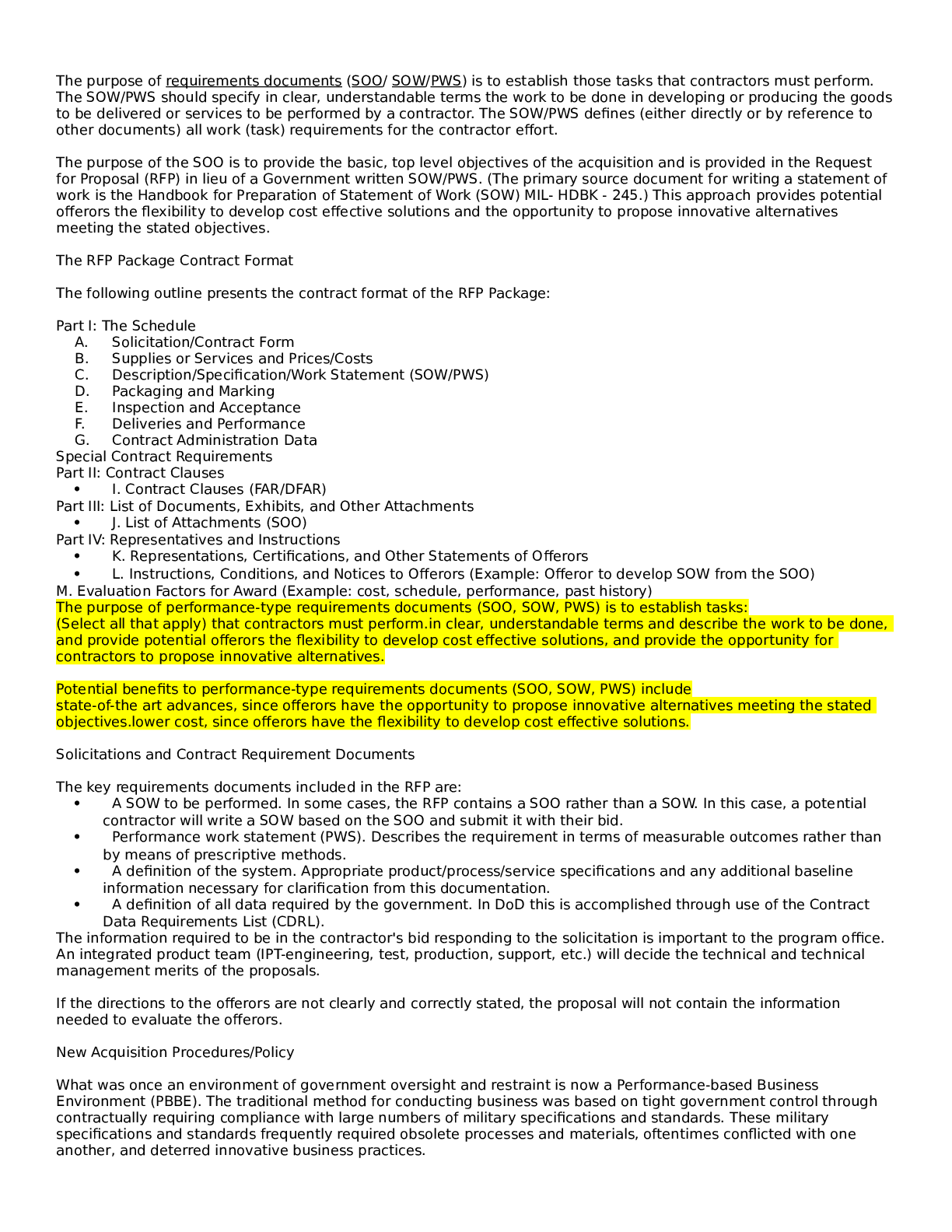
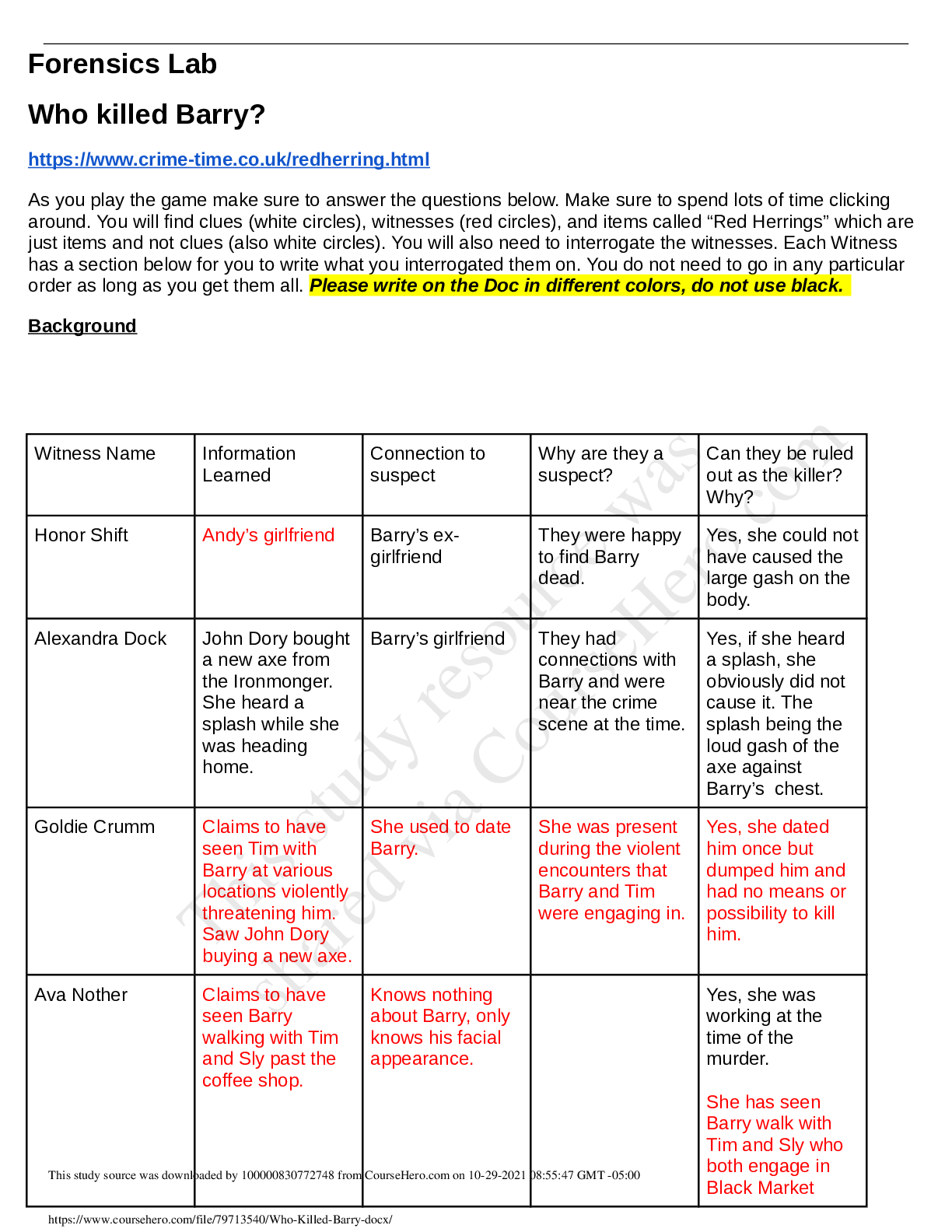
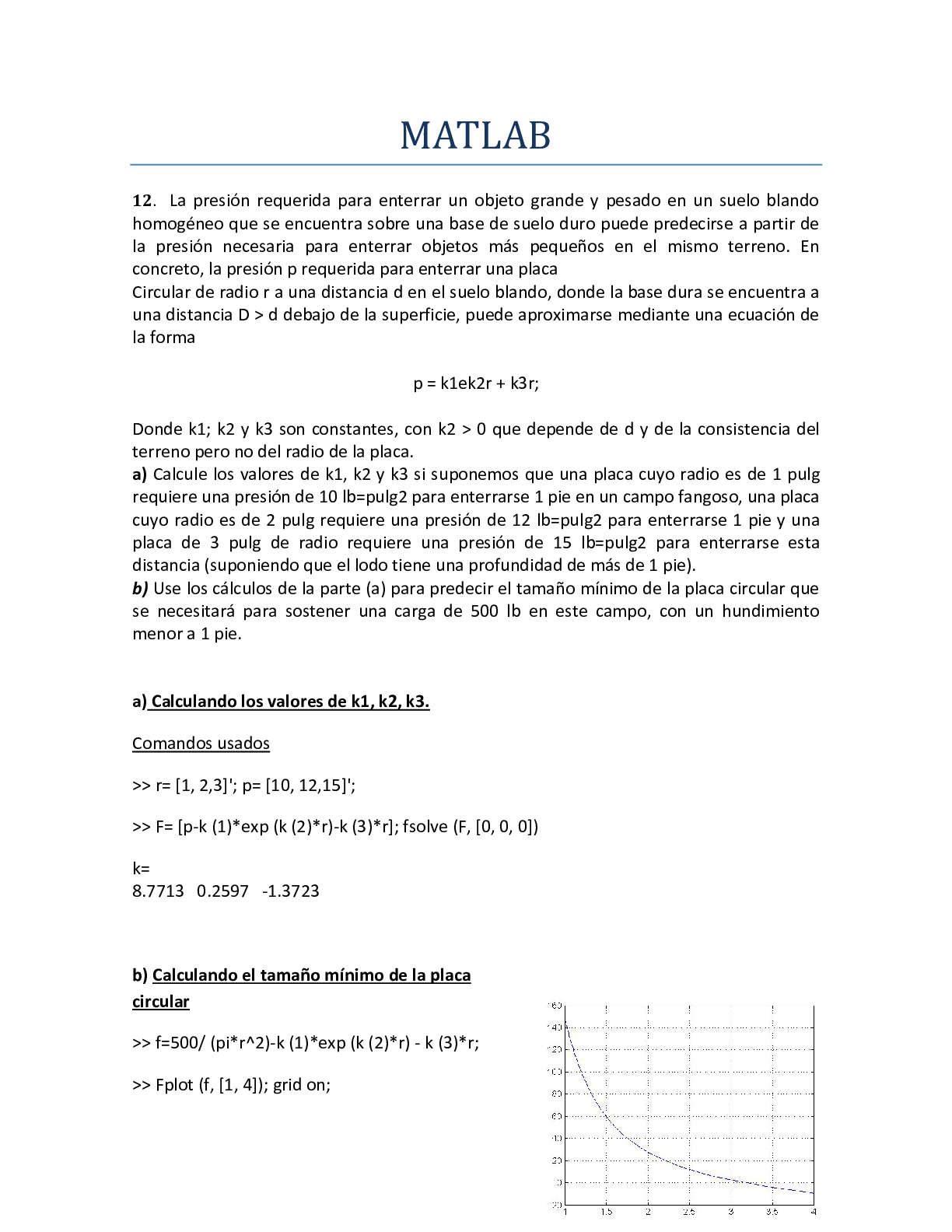
• University of Maryland, University College • CYB 670 Project 1: Preparatory Lab Exercises CYB 670 9040 Capstone in Cybersecurity University of Maryland University College Table of C... ontents PROJECT 1: PREPARATORY LAB EXERCISES 2 Executive Summary..3 Lab 1: Security Baseline - Preparatory Exercises.......3 Nessus Lab Report.....3 Yara Lab Report.....10 Thunderbird Report..13 Lab 2: Defensive Monitoring - Preparatory Exercises.....16 Wireshark Lab Report.......17 Snort Lab Report......25 Lab 3: Ransomware Attack and Mitigation - Preparatory Exercises...28 OurSecret29 Cryptool 2........33 Cain and Abel / Ophcrack.35 Conclusion.39 References......40 Executive Summary Cybersecurity professionals of the Five Eyes (FVEY) nations will participate in the global economic summit being held in the United Kingdom. As a member of the Canadian Government’s information security team, we are responsible for establishing and maintaining a secure communication network. The summit is being held in a country club and resort near London. The network will be set up to allow authorized users access via cell phones, laptops, desktops, and tablets (UMUC, 2019). Additionally, the network will need to connect to primary servers located at headquarters. Joint communications with other nations of FVEY will not be necessary, due to national security concerns (UMUC, 2019). Recent incidents of anomalous network activity will require preparatory work before setting up the network. This preparatory work and status of the network is detailed in this report. PROJECT 1: PREPARATORY LAB EXERCISES 4 Lab 1: Security Baseline - Preparatory Exercises Nessus Lab Report In this lab report, an initial scan of the network is conducted by using the Nessus Web Client. Once the Nessus Web Client is open, the scan must be given a name to identify it and the Internet Protocol (IP) address of the target. The Windows Operating System (OS) is used to. Figure 1 below shows how this is done. Figure 1. Nessus Web Client window to name scan and identify target on Windows OS. Once the scan is ran (successful or not), the results gathered from targeting IP address 172.21.35.32 we be shown on the Nessus dashboard as shown in Figure 2 below. Figure 2. Nessus Web Client showing scans conducted with status. Clicking on the scan itself will show the results of the scan as shown in Figure 3 below. Figure 3. Results of Nessus scan. Figure 3 above shows no hosts or vulnerabilities were found on the network. When a vulnerability is found, it will be detailed in this area of the Nessus scan and will give information about each vulnerability. Yara Lab Report The Yara scan is used to scan files and look for signatures of malware. Yara rules are syntax containing key words or phrases that will be used as the criteria to scan files on a computer. The images below show how the Yara scan was conducted. The first thing that must be done is to open the Command Prompt window and switch to the C: drive (the drive we will be working on), as shown in the Figure 4 below. [Show More]
Last updated: 1 year ago
Preview 1 out of 24 pages

Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Nov 15, 2022
Number of pages
24
Written in
Additional information
This document has been written for:
Uploaded
Nov 15, 2022
Downloads
0
Views
60