Telecommunication and Information Technology > QUESTIONS & ANSWERS > University of the Cumberlands EMISS ISOL532 Telecommunications and network security. Chapters 11 & 1 (All)
University of the Cumberlands EMISS ISOL532 Telecommunications and network security. Chapters 11 & 12 Exam. 20 Q&A
Document Content and Description Below
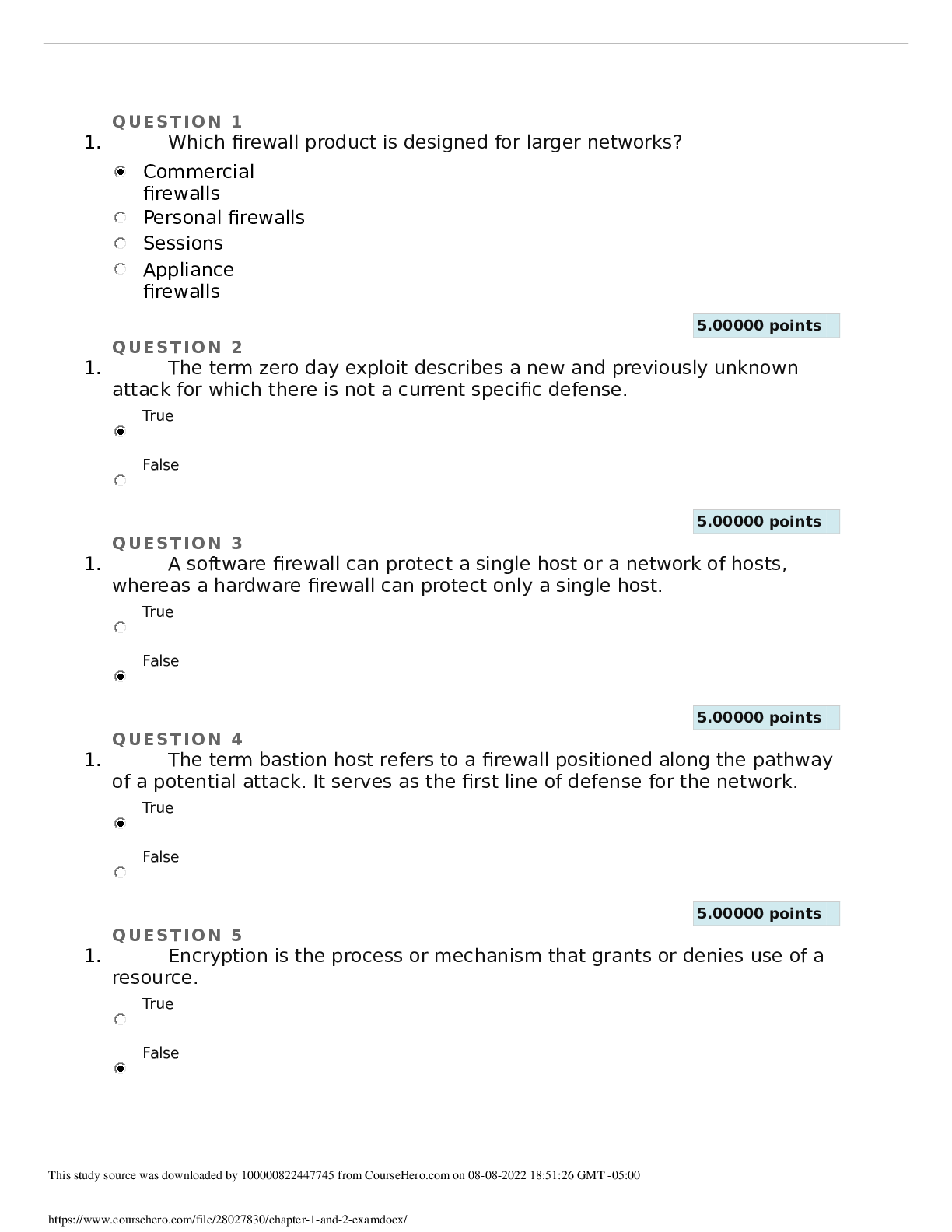
1. Which of the following describes Layer 2 Tunneling Protocol (L2TP)? The standards body for Internet-related engineering specifications An older protocol largely replaced by IPSec and SSL/ TLS-bas... ed VPNs in production environments, but still in use in some older environments The second core IPSec security protocol; it can perform authentication to provide integrity protection, although not for the outermost IP header An early proprietary protocol from Microsoft 5.00000 points QUESTION 2 1. Which section of the VPN policy describes the systems, networks, or people covered by the policy? Introducti on Policy Scope Purpose 5.00000 points QUESTION 3 1. “Privacy” is considered keeping information about a network or system user from being disclosed to unauthorized people. True False 5.00000 points QUESTION 4 1. One of the drawbacks of HTTP is that it does not include the ability to encrypt or otherwise protect the data stream between the client and server. True False 5.00000 points QUESTION 5 1. What name is given to a method that proves identity using two different authentication factors? Service level agreement (SLA) Two-factor authentication Hairpinning Anonymity 5.00000 points QUESTION 6 1. When employees have multiple concurrent connections, what might be happening to the VPN system? There may be a software failure. Employees may be trying to access the system from remote locations. There may be a security issue. There may be a hardware failure. 5.00000 points QUESTION 7 1. Which of the following refers to a network protocol that is a method for secure remote logon and other secure network services over a public network? Point-to-Point Protocol (PPP) Secure Shell (SSH) Authentication Header (AH) Encapsulating Security Payload (ESP) 5.00000 points QUESTION 8 1. Which type of architecture deploys the VPN so that traffic to and from the VPN is not firewalled? Internally connected architecture Bypass architecture DMZ architecture Two-factor architecture 5.00000 points QUESTION 9 1. Determining who the target audience for training is takes place in the planning stage. True False 5.00000 points QUESTION 10 1. The IPv6 IPSec is a set of national standards that use cryptographic security services to provide confidentiality, data origin authentication and data integrity. True False 5.00000 points QUESTION 11 1. Which type of architecture places a firewall in front of the VPN to protect it from Internet-based attacks as well as behind a firewall to protect the internal network? Bi-lateral architecture Two-prong approach Two-factor architecture DMZ architecture 5.00000 points QUESTION 12 1. When determining the number of users affected by a VPN problem, which troubleshooting step is being performed? Determining scope Identifying the symptoms Looking for changes Calling the vendor 5.00000 points QUESTION 13 1. Which of the following key VPN protocols used today is the main alternative for a VPN solution that does not leverage an IPSec solution? Internet Engineering Task Force (IETF) Authentication Header (AH) Secure Sockets Layer (SSL)/Transport Layer Security (TLS) Layer 2 Forwarding (L2F) Protocol 5.00000 points QUESTION 14 1. Which of the following is most likely to occur in the VPN? Denial of service attack VPN server attack Client attack Remote access attack 5.00000 points QUESTION 15 1. Which of the following is one of the most common and easily exploited vulnerabilities on any hardware network device? Insecure default configuration Misconfiguration by the installer Undistributed authentication credentials Default password 5.00000 points QUESTION 16 1. To mitigate the risk of security threats and breaches, all installers should be trained before installing the VPN. True False 5.00000 points QUESTION 17 1. IPSec is a mandatory component for IPv6, and is used to natively protect IPv6 data as it is sent over the network. True False 5.00000 points QUESTION 18 1. Instability is not considered a potential threat associated with software VPNs. True False 5.00000 points QUESTION 19 1. In typical end user/browser usage, SSL/TLS authentication is two-way. True False 5.00000 points QUESTION 20 1. Which of the following describes a service level agreement (SLA)? A contractual commitment by a service provider or support organization to its customers or users The ability for a network or system user to remain unknown An industry term referring to any product that appears in a vendor’s PowerPoint slide deck, but is not yet available in one of its products A process by which malicious code can enter from a non-secure network, and make a hairpin, or sharp turn and enter a secure network with little or no trouble because it is entering from a secure and verified endpoint [Show More]
Last updated: 1 year ago
Preview 1 out of 5 pages
Instant download

Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Aug 09, 2022
Number of pages
5
Written in
Additional information
This document has been written for:
Uploaded
Aug 09, 2022
Downloads
0
Views
88