Criminology > QUESTIONS & ANSWERS > Southern New Hampshire University; CJ 305/ CJ305/ CJ 305 Criminal Justice 330; All module quizzes, a (All)
Southern New Hampshire University; CJ 305/ CJ305/ CJ 305 Criminal Justice 330; All module quizzes, already graded_ Latest Fall 2021/2022.
Document Content and Description Below
CJ - 305 1-3 Quiz Module One Quiz Question 1 2.5 / 2.5 points Which of the following are top priorities for law enforcement technology research and development? Select all that apply. Technology t... o reduce fear of crime Technology for limiting inter-agency cooperation Technology to reduce interaction with the community Technology for preventing crime Technology to guarantee safety in public spaces Question 2 2.5 / 2.5 points Social media monitoring focuses on which of the following? Select one. Obtaining direct messages, metadata, and subscriber information without a warrant Tracking lawful protests with the intent to influence individuals to stop or self-censorUsing an informant or undercover account to obtain information from a private account Tracking an individual, group, or affiliation via privately available information Question 3 0 / 2.5 points What is the biggest barrier in implementing new technology in law enforcement? Select one. Finances Training Public perception Vendors Question 4 2.5 / 2.5 points Innovations in less-lethal suspect control include which of the following? Select all that apply. Electronic Control DevicePepper Spray Revolver Semiautomatic handgun Baton Question 5 2.5 / 2.5 points True or false: Despite advances in technology, the effectiveness of police agencies relies on the interactions of police officers with the public. True False Question 6 2.5 / 2.5 points Which of the following is a privacy concern for gunshot detection systems? Select one. Vendor employees attempting to identify whether a sound is a gunshot Recording of ambient background noises for voice recognitionTransmission of information from the vendor to police clients about potential shootings False positives that confuse ordinary background sound as gunshots Question 7 2.5 / 2.5 points Facial recognition raises concerns over which of the following? Select all that apply. Race Sexual orientation Age Socioeconomic status Gender Question 8 2.5 / 2.5 points True or false: Place-based predictive policing uses algorithms to generate a list of individuals likely to commit a crime.True False Question 9 2.5 / 2.5 points According to the module resources, which of the following have been the focus of physical evidence technology advancements in criminal investigations? Select all that apply. Confessions Eyewitness Statements Lasers Advanced Fingerprints DNA Question 10 2.5 / 2.5 points What major advancements in technology are related to traffic control and enforcement? Select all that apply. Manned traffic stopsBlood draws for DUIs Radar Cameras at intersections License plate recognition Attempt Score: 22.5 / 25 - AA precinct’s next 4-hour shift CJ 305 2-3 Quiz attempts 1 and 2 2.5 / 2.5 points In predictive policing, computer programs create a forecast estimating the risk of a crime occurring during what time frame? Select one. Question options: A precinct’s next 8-hour shift A precinct’s next 3-hour shift A precinct’s next 6-hour shift View Feedback 0 / 2.5 points According to the module resources, what should an agency have to attract millennial recruits? Select one. Question options: Employee cell phones An up-to-date website PowerPoint presentations View Feedback 0 / 2.5 points According to the module resources, the minimum quantities of routine stops allocated to patrol officers are called which of the following? Select one. Question options: Targeted stops Quotas A schedule with five eight-hour shiftsFalse Metrics View Feedback 2.5 / 2.5 points True or false: Forensic services are now expected to be provided by a crime scene investigator when a case goes to court. Question options: False View Feedback 2.5 / 2.5 points True or false: As pertains to the future of crime scene investigations, law enforcement agencies will no longer need to contract with private DNA labs. Question options: True View Feedback 2.5 / 2.5 points According to the module resources, which of the following statements regarding the recruitment and retention of millennial officers is true? Select one. Question options: Departments should prioritize investment in new technology over mentorship programs. Stop & frisk True Departments should establish mentorship programs to draw in millennial recruits.Hotspot Departments should keep the status quo related to traditional recruitment structures. Agencies should establish strict and traditional training programs. View Feedback 0 / 2.5 points Which meetings enabled discussion on the allocation of resources based on analysis of problems and the presentation of strategies to resolve them? Select one. Question options: Predictive policing CompStat Phicam View Feedback 2.5 / 2.5 points A place that is experiencing a disproportionate amount of police activity is known as which of the following? Select one. Question options: Forecast spot Riskspot Gridspot View Feedback 2.5 / 2.5 points Crime AnalystAccording to the module resources, which generation is the now the largest living in the United States? Select one. Question options: Baby boomers Generation Y Gen Xers View Feedback 2.5 / 2.5 points True or false: Before analytical platforms hit the market, police departments did not use crime mapping. Question options: What purposes does crime prediction software serve? Select all that apply. Question options: Shape the moral behavior of police Direct, supervise and regulate police work Predict who may commit a crime Millennials Predict where and when a crime may occur Predict what crimes may occurThis study source was downloaded by 100000840858457 from CourseHero.com on 05-02-2022 10:01:03 GMT -05:00 https://www.coursehero.com/file/105286070/CJ-305-2-3-Quiz-attempts-1-and-2docx/ Baby boomers False View Feedback 2.5 / 2.5 points According to the module resources, which generation currently makes up the upper management positions in law enforcement? Select one. Question options: Millennials Generation Y Gen Xers View Feedback 2.5 / 2.5 points True or false: There have been no lawsuits pertaining to a law enforcement agency’s use of predictive policing programs. Question options: True View Feedback 2.5 / 2.5 points True or false: According to the module resources, as baby boomers retire, agencies are left understaffed due to the difficulties of recruiting and retaining a younger generation of officers. Question options: True FalseThis study source was downloaded by 100000840858457 from CourseHero.com on 05-02-2022 10:01:03 GMT -05:00 https://www.coursehero.com/file/105286070/CJ-305-2-3-Quiz-attempts-1-and-2docx/ Millennials A precinct’s next 4-hour shift View Feedback 2.5 / 2.5 points According to the module resources, which generation is the now the largest living in the United States? Select one. Question options: Baby boomers Generation Y Gen Xers View Feedback 2.5 / 2.5 points In predictive policing, computer programs create a forecast estimating the risk of a crime occurring during what time frame? Select one. Question options: A precinct’s next 3-hour shift A precinct’s next 6-hour shift A precinct’s next 8-hour shift View Feedback 2.5 / 2.5 points A place that is experiencing a disproportionate amount of police activity is known as which of the following? Select one. Question options:This study source was downloaded by 100000840858457 from CourseHero.com on 05-02-2022 10:01:03 GMT -05:00 https://www.coursehero.com/file/105286070/CJ-305-2-3-Quiz-attempts-1-and-2docx/ Hotspot Gridspot Riskspot Forecast spot View Feedback 2.5 / 2.5 points True or false: Forensic services are now expected to be provided by a crime scene investigator when a case goes to court. Question options: False View Feedback 2.5 / 2.5 points According to the module resources, what should an agency have to attract millennial recruits? Select one. Question options: PowerPoint presentations Employee cell phones A schedule with five eight-hour shifts View Feedback 2.5 / 2.5 points True An up-to-date websiteThis study source was downloaded by 100000840858457 from CourseHero.com on 05-02-2022 10:01:03 GMT -05:00 https://www.coursehero.com/file/105286070/CJ-305-2-3-Quiz-attempts-1-and-2docx/ False True or false: As pertains to the future of crime scene investigations, law enforcement agencies will no longer need to contract with private DNA labs. Question options: True View Feedback Attempt Score: 23.5 / 25 - A Overall Grade (highest attempt): 23.5 / 25 - AThe principles of right and wrong CJ 230 3-3 Quiz 2 / 2 points According to the Utilitarianism theory, actions are morally permissible if and only if they do which of the following? Select one. Question options: They produce some happiness. They have no effect on the individual’s morality. They produce some sadness. View Feedback 0 / 2 points Which of the following best defines the term ethics? Select one. Question options: The discipline that investigates the meaning of ethical systems The study and analysis of what constitutes good or bad conduct The application of ethical principles to specific issues View Feedback 2 / 2 points True or false: Discretion is important for relationships between They produce at least as much net happiness as any other available action.the police and the public.Question options: Psychological False View Feedback 0 / 2 points Which of the following spheres of influence includes such factors as ethical fading and motivated blindness? Select one. Question options: Sociological Individual Work group View Feedback 2 / 2 points True or false: Without discretion, a police department loses its professionalism. Question options: False View Feedback 2 / 2 points Studies conducted by the Pew Research Center show that civil rights complaints against police are positively correlated to which of the following? Select one. True TrueQuestion options: Engaging in conduct that is prejudicial to the administration of justice The overall population of an area The number of crimes in a population The number of police officers employed in an area View Feedback 2 / 2 points Which of the following actions are considered professional misconduct for lawyers? Select all that apply. Question options: Disclosing information obtained through a judge while participating in an approved lawyer activity Disclosing evidence through the discovery process Honoring the Rules of Professional Conduct, knowingly assisting or inducing another to do so, or doing so View Feedback 2 / 2 points True or false: The mission of the National Registry of Exonerations is to provide comprehensive information on exonerations of innocent criminal defendants in order to prevent future false convictions by learning from past errors. Question options: The percentage of minorities in the population Committing a criminal act that reflects adversely on their profession as a lawyerAttorneys should not take cases beyond their expertise. Framing False View Feedback 2 / 2 points Which of the following are requirements for attorneys based on the Model Rules? Select all that apply. Question options: Attorneys may disregard a client’s interest while maintaining a professional and civil demeanor. Attorneys should place professional considerations above client interests. View Feedback 2 / 2 points Which of the following refers to the manner in which a question is created to be answered? Select one. Question options: Coming to conclusions Gathering intelligence Creating a structure filled with checks and balances True Attorneys should maintain confidentiality regarding information obtained through their client. Attorneys should not have two clients with competing interests.View Feedback 16 / 20 - B- 16 / 20 - BDoneCJ 305 4-0 Check Your Knowledge 1. Phenotyping can pretty accurately predict which of the following? Select all that apply. 0.5 / 0.5 points Birthmarks Fitness level Eye and hair color Likelihood of tattoos and piercings Tendency to freckle 2. True or false: Consent for warrantless searches can be withdrawn at any time. 0.5/0.5 points True False 3. Which of the following are methods for law enforcement to obtain passwords and decrypt data? Select all that apply. 0.5 / 0.5 points Compelling the owner to give access Crime scene searches Interviews Guessing of common passwords Working with the manufacturers 4. Arrest reports are one of the main types of reports written by police officers. 0.5 / 0.5 points True This study source was downloaded by 100000840858457 from CourseHero.com on 05-02-2022 10:34:45 GMT -05:00 https://www.coursehero.com/file/101040277/CJ-305-4-0CYKdocx/False 5. How do criminals use cameras, including audio and video, against law enforcement? Select one. 0.5 / 0.5 points Tracking Wire Surveillance Consensual monitoring 6. Which of the following is a crime that touch DNA can help solve? Select one. 0.5 / 0.5 points Phishing scam Ransomware Burglary Cyberbullying 7. What is the main reason that more businesses and individuals are installing and using security cameras now than in the past? Select one. 0.5 / 0.5 points The use of security cameras is not increasing for businesses or individuals. Only recently has security camera footage become admissible in court. The benefit outweighs the extreme cost. Security cameras are more affordable. This study source was downloaded by 100000840858457 from CourseHero.com on 05-02-2022 10:34:45 GMT -05:00 https://www.coursehero.com/file/101040277/CJ-305-4-0CYKdocx/8. True or false: During an investigation, it is important to distinguish between the location of a device and the location of the data. 0.5 / 0.5 points True False 9. True or false: Over the past decade or so, it has become apparent that many forensic methodologies offer far less certainty than TV dramas suggest. 0.5 / 0.5 points True False 10. Using DNA to identify the genetic ancestry of a suspect employs which of the following? Select one. 0.5 / 0.5 points DNA generation DNA phototyping DNA phenotyping DNA portrait This study source was downloaded by 100000840858457 from CourseHero.com on 05-02-2022 10:34:45 GMT -05:00 https://www.coursehero.com/file/101040277/CJ-305-4-0CYKdocx/ Powered by TCPDF (www.tcpdf.org)CJ 305 Module 4 Quiz Submission View Your quiz has been submitted successfully. n 1 2.5 / 2.5 points According to the module resources, why are security cameras becoming more valuable in criminal investigations? Select all that apply. Question options: Security cameras are more affordable. Many security cameras are small and able to be hidden. Security cameras are not available for indoor and outdoor use. Security cameras are not valuable in criminal investigations. Security cameras are now available for indoor and outdoor use. View Feedback n 2 2.5 / 2.5 points According to the module resources, which of the following is the equivalent of a letter or memo that may include attachments or enclosures? Select one. Question options: Email Internet service provider Picture message Wireless hotspot This study source was downloaded by 100000840858457 from CourseHero.com on 05-02-2022 10:35:33 GMT -05:00 https://www.coursehero.com/file/113119991/CJ-305-Module-4-quiz-attempt-2docx/View Feedback n 3 2.5 / 2.5 points True or false: Consent for a warrantless search cannot be withdrawn at any time. Question options: True False View Feedback n 4 2.5 / 2.5 points Which of the following is a forensic method used to analyze a very small amount of DNA left at a crime scene? Select one. Question options: Network DNA Feel DNA Manipulation DNA Touch DNA View Feedback n 5 2.5 / 2.5 points Which of the following cannot be tracked? Select one. Question options: Electronic toll device This study source was downloaded by 100000840858457 from CourseHero.com on 05-02-2022 10:35:33 GMT -05:00 https://www.coursehero.com/file/113119991/CJ-305-Module-4-quiz-attempt-2docx/Cash transaction GPS device Credit or membership card transaction View Feedback n 6 1.5 / 2.5 points According to the module resources, how can smartphones and smartphone apps assist crime scene investigators on the job? Select all that apply. Question options: Accurate weather information As a level Social media Work-life balance Up-to-date news View Feedback n 7 2.5 / 2.5 points True or false: It is not important to determine the victim’s, suspect’s, or witness’s skill level as it relates to technology. Question options: True False This study source was downloaded by 100000840858457 from CourseHero.com on 05-02-2022 10:35:33 GMT -05:00 https://www.coursehero.com/file/113119991/CJ-305-Module-4-quiz-attempt-2docx/View Feedback n 8 2.5 / 2.5 points What is available to law enforcement that may provide information regarding the specific location of a phone owned by a particular subscriber who is being investigated? Select one. Question options: Cell billing cycle Portable communication device Cell tower data Public telephone network View Feedback n 9 2.5 / 2.5 points According to the module resources, what are the two main types of reports written by police officers? Select two. Question options: Bond reports Crime incident reports Charging reports Arrest reports Bail reports This study source was downloaded by 100000840858457 from CourseHero.com on 05-02-2022 10:35:33 GMT -05:00 https://www.coursehero.com/file/113119991/CJ-305-Module-4-quiz-attempt-2docx/View Feedback n 10 2.5 / 2.5 points Which of the following techniques conjures up a physical likeness of a person? Select one. Question options: DNA phenotyping DNA generation DNA portrait DNA phototyping View Feedback 24 / 25 - A Overall Gra 24 / 25 - A This study source was downloaded by 100000840858457 from CourseHero.com on 05-02-2022 10:35:33 GMT -05:00 https://www.coursehero.com/file/113119991/CJ-305-Module-4-quiz-attempt-2docx/ Powered by TCPDF (www.tcpdf.org)Email CJ 305 4-3 quiz. 2.5 / 2.5 points According to the module resources, why are security cameras becoming more valuable in criminal investigations? Select all that apply. Question options: Security cameras are not valuable in criminal investigations. Security cameras are not available for indoor and outdoor use. View Feedback 2.5 / 2.5 points According to the module resources, which of the following is the equivalent of a letter or memo that may include attachments or enclosures? Select one. Question options: Wireless hotspot Picture message Internet service provider View Feedback 2.5 / 2.5 points True or false: Consent for a warrantless search cannot be withdrawn at any time. Question options: True Security cameras are more affordable. Many security cameras are small and able to be hidden. Security cameras are now available for indoor and outdoor use.DNA phenotyping View Feedback 2.5 / 2.5 points According to the module resources, what technological innovation in fingerprinting do some crime scene investigators think is likely coming in the future? Select one. Question options: Searchable fingerprints of all citizens Faster means to take fingerprints at a crime scene Computer-assisted fingerprint identification View Feedback 2.5 / 2.5 points Which of the following techniques conjures up a physical likeness of a person? Select one. Question options: DNA portrait DNA phototyping DNA generation View Feedback 2.5 / 2.5 points Which of the following sources provide publicly available information? Select all that apply. Question options: False Immediate fingerprint results on screenFalse Sealed government records Confidential law enforcement databases Confidential healthcare databases View Feedback 2.5 / 2.5 points True or false: It is not important to determine the victim’s, suspect’s, or witness’s skill level as it relates to technology. Question options: True View Feedback 2.5 / 2.5 points What is the term for the monitoring of wire, oral, or electronic communication with the knowledge and consent of at least one involved party? Select one. Question options: Surveillance Tracking Countersurveillance View Feedback Internet searches Commercially available databases Consensual monitoringCrime incident reports 1 / 2.5 points According to the module resources, how can smartphones and smartphone apps assist crime scene investigators on the job? Select all that apply. Question options: Work-life balance As a level View Feedback 2.5 / 2.5 points According to the module resources, what are the two main types of reports written by police officers? Select two. Question options: Bail reports Charging reports Bond reports View Feedback Accurate weather information Social media Up-to-date news Arrest reportsmpt): 2.5 / 2.5 points What is available to law enforcement that may provide information regarding the specific location of a phone owned by a particular subscriber who is being investigated? Select one. Question options: Public telephone network Cell billing cycle Portable communication device View Feedback 2.5 / 2.5 points Which of the following cannot be tracked? Select one. Question options: GPS device Credit or membership card transaction Electronic toll device View Feedback 2.5 / 2.5 points Which of the following is a forensic method used to analyze a very small amount of DNA left at a crime scene? Select one. Question options: Cell tower data Cash transactionFeel DNA Manipulation DNA Network DNA View Feedback 1.5 / 2.5 points According to the module resources, how can smartphones and smartphone apps assist crime scene investigators on the job? Select all that apply. Question options: As a level Up-to-date news Work-life balance View Feedback 2.5 / 2.5 points True or false: Consent for a warrantless search cannot be withdrawn at any time. Question options: True View Feedback Touch DNA Social media Accurate weather information FalseInternet searches Immediate fingerprint results on screen 2.5 / 2.5 points Which of the following sources provide publicly available information? Select all that apply. Question options: Confidential healthcare databases Sealed government records Confidential law enforcement databases View Feedback 2.5 / 2.5 points According to the module resources, what technological innovation in fingerprinting do some crime scene investigators think is likely coming in the future? Select one. Question options: Faster means to take fingerprints at a crime scene Computer-assisted fingerprint identification Searchable fingerprints of all citizens View Feedback 2.5 / 2.5 points Which of the following techniques conjures up a physical likeness of a person? Select one. Question options: DNA phototyping Commercially available databases DNA phenotypingCrime incident reports DNA generation DNA portrait View Feedback 2.5 / 2.5 points According to the module resources, why are security cameras becoming more valuable in criminal investigations? Select all that apply. Question options: Security cameras are not available for indoor and outdoor use. Security cameras are not valuable in criminal investigations. View Feedback 2.5 / 2.5 points According to the module resources, what are the two main types of reports written by police officers? Select two. Question options: Bail reports Bond reports Charging reports Security cameras are more affordable. Many security cameras are small and able to be hidden. Security cameras are now available for indoor and outdoor use. Arrest reportsView Feedback Attempt Score: 24 / 25 - A Overall Grade (highest attempt): 24 / 25 - A DoneCJ230 5-0 Check Your Knowledge Question 1 0.5 / 0.5 points Which of the following are associated with an objective tone? Select all that apply. Subject to interpretation Unbiased Influenced by emotions Used for summaries or news articles Question 2 0.5 / 0.5 points Which of the following is true regarding process analysis? Select one. Directive process analysis is typically written in second-person point of view. Both forms of process analysis are written in chronological order. Informative process analysis is typically written in third-person point of view.Both forms of process analysis are written in order of importance. Question 3 0.5 / 0.5 points Rephrasing a source’s information to create a reworded passage of similar length describes which of the following? Select one. Quoting Paraphrasing Summarizing Documenting Question 4 0.5 / 0.5 points The six tips for using an objective tone include which of the following? Select all that apply. Show opposing viewpoints Be subjective Include all main pointsUse someone else’s words Question 5 0.5 / 0.5 points What steps should be taken to revise your summary draft? Select all that apply. Focus on evidence and examples provided Write down the main points Scan piece briefly Reread and take notes Question 6 0.5 / 0.5 points Which of the following is important in order to write a successful summary? Select all that apply. Be subjective Be concise and clearUse someone else’s words Include all main points Question 7 0.125 / 0.5 points Which of the following are elements of an instructional process essay? Select all that apply. Describes a process in order to better understand it Explains how to do something Focuses on the process itself and not the person performing it Explains how to make something Question 8 0.5 / 0.5 points Which of the following is an important element of a summary? Select one. Extensive use of detailsA length of at least 500 words A focus on facts A descriptive introduction Question 9 0.5 / 0.5 points Which of the following are among the steps taken when analyzing an ethical dilemma? Select all that apply. Identify relevant values and concepts. Determine which moral dilemma can be addressed last. Identify the facts. Allow the dilemma to remain unresolved. Question 10 0.5 / 0.5 points True or false: Informative process analysis is typically written in second-person point of view.True False Attempt Score: 4.63 / 5 - ACJ305 5-3 Module Five Quiz 2 / 2 points Taking a long passage and rewording it into a shorter form describes which of the following? Select one. Question options: Transcribing Paraphrasing Documenting View Feedback 1.6 / 2 points Which of the following are tips for how to write an effective summary? Select all that apply. Question options: Make the summary extensive. Elaborate on your favorite sections. View Feedback 2 / 2 points Summarizing Don’t go beyond the main points. Be specific with details such as numbers, statistics, dates, and figures. Follow the order of information as it is presented in the original material.Which of the following is associated with a subjective tone? Select one. Question options: Unbiased Used for summaries or news articles Not influenced by emotions View Feedback 2 / 2 points Which of the following are forms of process analysis? Select all that apply. Question options: Influential Cognitive Indirective View Feedback 2 / 2 points Rules for avoiding plagiarism include which of the following? Select all that apply. Question options: Subject to interpretation Informative Directive/instructionalFocus on facts and figures Be impersonal Emphasize irrelevant facts. Avoid using data. View Feedback 2 / 2 points Which of the following should you do if you want to write in an objective tone? Select all that apply. Question options: Use language that shows which viewpoint you agree with Include small amounts of information about the writer Include opinions View Feedback 2 / 2 points According to the text, which of the following is the first step to take when clarifying any dilemma? Select one. Question options: Identify all possible moral dilemmas Fully transform the source into your own language. Emphasize the facts that are relevant to your thesis. Always cite your source.Review all the facts Identify potential values involved Interview all those involved View Feedback 2 / 2 points Which of the following are important elements of a summary? Select all that apply. Question options: An extensive introduction A focus on small details A length of 500 words or more View Feedback 2 / 2 points True or false: Informative process analysis is typically written in third person point of view. Question options: False Key points that are highlighted A focus on facts TrueView Feedback 2 / 2 points According to the text, which of the following is the last step to take when clarifying any dilemma? Select one. Question options: Identify all possible moral dilemmas Identify potential values involved Review all the facts View Feedback 19.6 / 20 - A 19.6 / 20 - A Done Use some means of decision making to address the dilemmaThis study source was downloaded by 100000840858457 from CourseHero.com on 05-02-2022 10:45:28 GMT -05:00 https://www.coursehero.com/file/108330687/Cj305-5-3-quizdocx/ Cost of security upgrades It can cost much more than the original loss of funds to recover. Cj305 5-3 quiz Attempt 1 Attempt 1 Written: Sep 28, 2021 10:42 PM - Sep 28, 2021 10:52 PM Submission View Your quiz has been submitted successfully. 2.5 / 2.5 points According to the module resources, what factor contributes to continued business loss due to large scale data breaches? Select one. Question options: Lack of technology to prevent these crimes Customers’ lack of secure purchasing habits Lack of specialized personnel View Feedback 2.5 / 2.5 points According to the module resources, which of the following describe the realities of prosecuting cybercrime? Select all that apply. Question options: Recovery of funds is never possible. Recovery of funds is always possible. Prosecutors don't challenge cybercrime evidence in court. Recovery of funds is sometimes possible.This study source was downloaded by 100000840858457 from CourseHero.com on 05-02-2022 10:45:28 GMT -05:00 https://www.coursehero.com/file/108330687/Cj305-5-3-quizdocx/ It’s a peer-to-peer operation, comprised of just sellers and buyers. View Feedback 0 / 2.5 points According to the module resources, which of the following is the number-one barrier to prosecuting cybercrime? Select one. Question options: Most cybercrimes originate within the United States and our laws make them difficult to prosecute. The offender and the victim reside in the same jurisdiction. The offender and the victim reside in different legal jurisdictions. View Feedback 2.5 / 2.5 points According to the module resources, marketplaces like OpenBazaar pose which of the following challenges to law enforcement agencies? Select one. Question options: Police are unable to infiltrate them for sting operations. The fight against these marketplaces is going well and has good velocity. The kingpin behind them is powerful and anonymous. View Feedback 2.5 / 2.5 points According to the module resources, which of the following is a component of advance fee schemes? Select one. Question options: Most cybercrimes originate outside of the United States, which makes it impossible to collect good legal eThis study source was downloaded by 100000840858457 from CourseHero.com on 05-02-2022 10:45:28 GMT -05:00 https://www.coursehero.com/file/108330687/Cj305-5-3-quizdocx/ Insignificant global losses by individuals The FBI’s inability to find the origin of these crimes Demand for assistance View Feedback 2.5 / 2.5 points Which of the following types of criminal opportunities can be so lucrative that criminals may not need to pursue legitimate employment? Select one. Question options: Cyberterrorism Money laundering Embezzlement View Feedback 2.5 / 2.5 points True or false: Smartphones can now automatically protect data by encoding it, and certain devices can erase themselves if anyone tries to break in. These features protect consumers but also protect criminals. Question options: False View Feedback Initial contact via email Internet fraud schemes TrueThis study source was downloaded by 100000840858457 from CourseHero.com on 05-02-2022 10:45:28 GMT -05:00 https://www.coursehero.com/file/108330687/Cj305-5-3-quizdocx/ Juries 2.5 / 2.5 points According to the module resources, what is one of the criminal services provided by the darknet? Select one. Question options: Cryptocurrency and digital wallets Access behind firewalls Communication between journalists View Feedback 2 / 2.5 points According to the module resources, who needs to be trained in cybercrime to aid in positive outcomes for cybercrime cases? Select all that apply. Question options: Internet service providers (ISPs) Offenders Judges View Feedback 2.5 / 2.5 points True or false: Internet fraud schemes committed globally have estimated losses in the billions every year. Question options: Obtaining of weapons Law enforcementThis study source was downloaded by 100000840858457 from CourseHero.com on 05-02-2022 10:45:28 GMT -05:00 https://www.coursehero.com/file/108330687/Cj305-5-3-quizdocx/ False View Feedback Attempt Score: 22 / 25 - B+ Overall Grade (highest attempt): 22 / 25 - B+ TrueThieves now target GPS mapping devices. CJ 305 6-3 quiz 2.5 / 2.5 points What is the term for the method of protecting digital information as it is stored on a device or transmitted across the internet or other computer networks? Select one. Question options: Extraction Extortion Going dark View Feedback 0 / 2.5 points According to the module resources, how is technology changing what criminals seek when breaking into vehicles? Select one. Question options: Thieves now target items of high cash value. Thieves now target sound systems. Thieves now target vehicle registration and insurance cards. View Feedback 2.5 / 2.5 points True or false: In addition to committing new types of computer-related crimes, offenders are using technology to commit offenses that have been unlawful for decades. Question options: False Encryption TrueView Feedback 2.5 / 2.5 points Which of the following statements is true regarding the dark web? Select one. Question options: The dark web has no legitimate purpose. Federal authorities rarely target darknet markets. The dark web does not allow for users to remain anonymous. View Feedback 2.5 / 2.5 points According to the module resources, which of the following statements is true regarding the reason computer-related crime is attractive to criminals? Select one. Question options: There is potential for increased risk and financial gain. Investigations and prosecution are not as difficult. The internet provides a low degree of anonymity. View Feedback 2.5 / 2.5 points Which of the following is a type of online attack that blocks a user from his or her computer system? Select one. Question options: The dark web is a major platform for trafficking drugs and weapons. Criminal penalties are often low.Ransomware Sextortion Identity theft Social engineering View Feedback 2.5 / 2.5 points According to the module resources, which of the following are defining characteristics of digital evidence? Select all that apply. Question options: Digital evidence can not be altered. Digital evidence can not be damaged. Digital evidence is never time sensitive. View Feedback 0 / 2.5 points Which of the following is a portion of the internet that includes private networks of organizations that may not be public? Select one. Question options: Deep web Surface web Darknet market Digital evidence crosses jurisdictional boundaries. Digital evidence is latent or hidden.False Internet of things Dark web View Feedback 2.5 / 2.5 points True or false: Police must always seek warrants for access to information on social media, even if a person does not utilize their privacy controls and their posts are public. Question options: True View Feedback 2.5 / 2.5 points Which of the following refers to the network of digital objects that transmit data using embedded sensors? Select one. Question options: Internet of equipment Internet of objects Internet of devices View Feedback Which of the following is defined as all websites and web pages that are indexed and searchable? Select one. Question options:Deep web Darknet market Dark web View Feedback 2.5 / 2.5 points According to the module resources, which of the following are ways that investigators use social media during criminal investigations? Select all that apply. Question options: Conduct interviews Process evidence View Feedback 2.5 / 2.5 points According to the module resources, which of the following types of technology are commonly used by both law enforcement and offenders? Select all that apply. Question options: Surface web Collect evidence Connect people involved in a case Identify potential suspects Identify criminal networks Cell phone apps DronesDNA Gunshot detection systems View Feedback 2.5 / 2.5 points Which of the following is a type of online attack that blocks a user from his or her computer system? Select one. Question options: Social engineering Identity theft Sextortion View Feedback 2.5 / 2.5 points Which of the following statements is true regarding the dark web? Select one. Question options: The dark web does not allow for users to remain anonymous. Federal authorities rarely target darknet markets. The dark web has no legitimate purpose. Social media Cryptocurrency Ransomware The dark web is a major platform for trafficking drugs and weapons.View Feedback 2.5 / 2.5 points According to the module resources, how is technology changing what criminals seek when breaking into vehicles? Select one. Question options: Thieves now target items of high cash value. Thieves now target GPS mapping devices. Thieves now target sound systems. Thieves now target vehicle registration and insurance cards. View Feedback 2.5 / 2.5 points True or false: In addition to committing new types of computer-related crimes, offenders are using technology to commit offenses that have been unlawful for decades. Question options: False View Feedback 2.5 / 2.5 points According to the module resources, which of the following statements is true regarding the reason computer-related crime is attractive to criminals? Select one. Question options: There is potential for increased risk and financial gain. True Criminal penalties are often low.The internet provides a low degree of anonymity. Investigations and prosecution are not as difficult. View Feedback 2.5 / 2.5 points True or false: Police must always seek warrants for access to information on social media, even if a person does not utilize their privacy controls and their posts are public. Question options: True False View Feedback 2.5 / 2.5 points Which of the following is a portion of the internet that includes private networks of organizations that may not be public? Select one. Question options: Darknet market Surface web Dark web View Feedback Deep webCJ 305 7-2 Quiz: Module 7 Your quiz has been submitted successfully. 2 / 2.5 points Which of the following are examples of cybercrime? Select all that apply. Question options: Home invasion Battery View Feedback 2.5 / 2.5 points What can a hacker gain access to through security flaws? Select all that apply. Question options: Email but not networks Commercial websites but not government systems Phishing Dark net Ransomware Government systems Email and networks Commercial websitesView Feedback 0 / 2.5 points Structured Query Language (SQL) injections can accomplish which of the following? Select one. Question options: Overwhelm your system’s resources so that it cannot respond to service requests Hijack a session between a trusted client and a network server Provide unauthorized access to sensitive information in a database View Feedback 2.5 / 2.5 points True or false: There is a lack of options for free or reduced-cost training that state and local police agencies can pursue. Question options: True False View Feedback 2.5 / 2.5 points Which of the following is a technique that improves security and hardens potential targets of cybercrime? Select one. Question options: Hashing Ten-factor authentication Never storing Personal Identifiable Information (PII) Intercept network traffic to obtain sensitive informationEight-factor authentication View Feedback 2.5 / 2.5 points True or false: Internet service providers can store overseas data on multiple servers in multiple countries, making the Mutual Assistance Treaty process difficult and time consuming. Question options: True False View Feedback 2.5 / 2.5 points According to the module resources, which of the following strategies could help agencies take advantage of the latest in technology and training, resulting in lower personnel costs? Select one. Question options: Creating a dedicated digital forensics unit Using research universities Creating a process for hiring, training, and retention Using private digital forensics labs View Feedback 0 / 2.5 pointsAccording to the module resources, state and local agencies are increasingly turning to what to assist them with digital forensic examinations? Select one. Question options: Rehabilitated hackers Fusion centers Fission centers View Feedback 2.5 / 2.5 points True or false: One of the best defenses against password cracking is the use of strong passwords. Question options: True False View Feedback 2.5 / 2.5 points Which of the following is a challenge of the 1986 Stored Communications Act? Select one. Question options: It was drafted before storing data on foreign servers became the norm. The act has always resulted in a frustrating, tedious, and time-consuming process. You cannot get access to the data stored overseas even with approval from the foreign country’s governme It applies to data stored overseas. Darknet vigilante communitiesView Feedback 19.5 / 25 - C+ 19.5 / 25 - C+CJ305 7-0 Check Your Knowledge Your quiz has been submitted successfully. 0.5 / 0.5 points True or false: There are several options for free or reducedcost training in digital forensics that state and local police agencies can pursue. Question options: True False View Feedback 0.5 / 0.5 points Which of the following is a technology that could reshape investigations in the future? Select one. Question options: Robotics Law reform Machine learning Google lenses View Feedback 0.5 / 0.5 points Which of the following describes a common goal of phishing schemes? Select one Question options: To bring a website down by flooding it with fake trafficTo get access to personal information for the purpose of committing fraud To get access to a personal computer to watch the victim through their webcam To restrict access to a computer until a ransom is paid View Feedback 0.5 / 0.5 points True or false: Technology companies are often the gatekeepers of all electronic data. Question options: True False View Feedback 0.5 / 0.5 points Why is hiring civilian staff to support criminal investigations a challenge? Select one. Question options: The job receives a flood of resumes and interest because it is a job protected from traditional layoffs or hir It can be hard to justify spending resources on non-sworn personnel and ensure consistent funding for the Despite consistent funding, the interest from potential employees is extremely low because of civilian feeli It is hard to trust non-sworn personnel assisting in investigations. View Feedback 0.5 / 0.5 points Why can it be hard for police agencies to retain specialized civilian staff and sworn investigators? Select one.Question options: There is a toxic work environment in law enforcement agencies. There is a lack of advancement opportunities in law enforcement agencies. Employees will accept lower salaries in the private sector for improved work-life balance. View Feedback 0.5 / 0.5 points True or false: The internet introduced an opportunity to commit crime at a distance. Question options: True False View Feedback 0.5 / 0.5 points Which of the following is an implication for law enforcement of our increasingly interconnected digital world? Select one. Question options: Digital data that is easy to access despite being saved on multiple servers in multiple countries Judges are issuing search warrants with extraterritorial authority to access data stored overseas Loss of evidence, because obtaining data stored overseas can be slow, and that data could be lost or deleted All foreign stored data being subject to U.S. jurisdiction if the user is a U.S. citizen View Feedback 0 / 0.5 points There is higher pay in the private sector.Which of the following describes how law enforcement used the 1986 Stored Communications Act before internet service providers started storing their data on foreign servers? Select one. Question options: Law enforcement would receive the data after a lawfully issued warrant. Law enforcement could access the data from the service provider’s servers themselves with a warrant to m Law enforcement could receive the data with a verbal request without a warrant. View Feedback 0.5 / 0.5 points What are some agencies doing to keep pace with changes in computer-based crime? Select one. Question options: Keeping organized crime and detective bureaus separate Silo expertise Maintain existing organizational structure so as not to disrupt police officers View Feedback 4.5 / 5 - ALaw enforcement would rarely receive the data even with a lawfully issued warrant. Spreading expertise around4.5 / 5 - ADoneCJ 305 7-2 Quiz: Module 7 Your quiz has been submitted successfully. 2 / 2.5 points Which of the following are examples of cybercrime? Select all that apply. Question options: Home invasion Battery View Feedback 2.5 / 2.5 points What can a hacker gain access to through security flaws? Select all that apply. Question options: Email but not networks Commercial websites but not government systems Phishing Dark net Ransomware Government systems Email and networks Commercial websitesView Feedback 0 / 2.5 points Structured Query Language (SQL) injections can accomplish which of the following? Select one. Question options: Overwhelm your system’s resources so that it cannot respond to service requests Hijack a session between a trusted client and a network server Provide unauthorized access to sensitive information in a database View Feedback 2.5 / 2.5 points True or false: There is a lack of options for free or reduced-cost training that state and local police agencies can pursue. Question options: True False View Feedback 2.5 / 2.5 points Which of the following is a technique that improves security and hardens potential targets of cybercrime? Select one. Question options: Hashing Ten-factor authentication Never storing Personal Identifiable Information (PII) Intercept network traffic to obtain sensitive informationEight-factor authentication View Feedback 2.5 / 2.5 points True or false: Internet service providers can store overseas data on multiple servers in multiple countries, making the Mutual Assistance Treaty process difficult and time consuming. Question options: True False View Feedback 2.5 / 2.5 points According to the module resources, which of the following strategies could help agencies take advantage of the latest in technology and training, resulting in lower personnel costs? Select one. Question options: Creating a dedicated digital forensics unit Using research universities Creating a process for hiring, training, and retention Using private digital forensics labs View Feedback 0 / 2.5 pointsAccording to the module resources, state and local agencies are increasingly turning to what to assist them with digital forensic examinations? Select one. Question options: Rehabilitated hackers Fusion centers Fission centers View Feedback 2.5 / 2.5 points True or false: One of the best defenses against password cracking is the use of strong passwords. Question options: True False View Feedback 2.5 / 2.5 points Which of the following is a challenge of the 1986 Stored Communications Act? Select one. Question options: It was drafted before storing data on foreign servers became the norm. The act has always resulted in a frustrating, tedious, and time-consuming process. You cannot get access to the data stored overseas even with approval from the foreign country’s governme It applies to data stored overseas. Darknet vigilante communitiesView Feedback 19.5 / 25 - C+ 19.5 / 25 - C+ [Show More]
Last updated: 1 year ago
Preview 1 out of 76 pages

Reviews( 0 )
Recommended For You
*NURSING> QUESTIONS & ANSWERS > NCSBN TEST BANK for the NCLEX-RN & NCLEX-PN. Contains More than 2000 Q&A Plus Review and Rationale in 517 PAGES. (All)
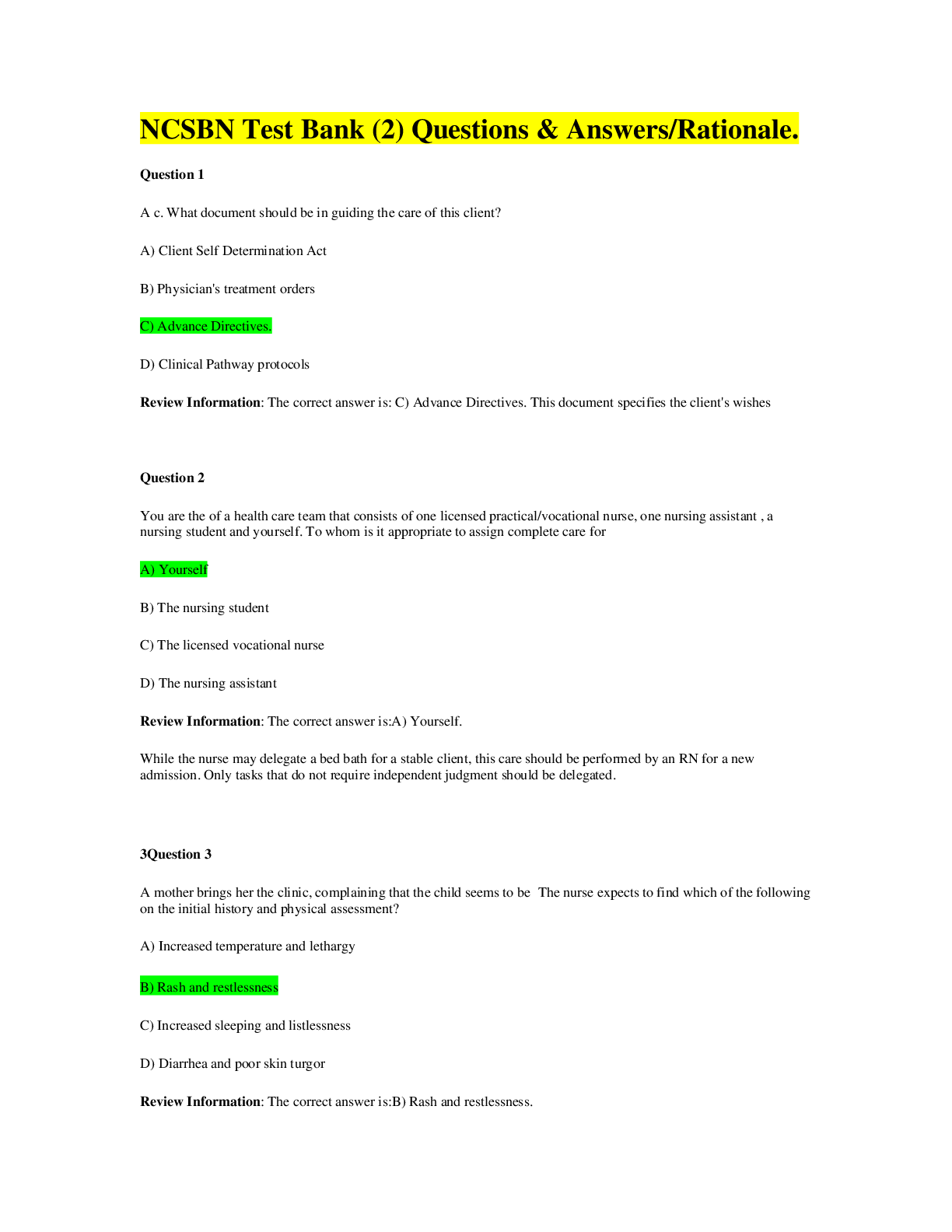
NCSBN TEST BANK for the NCLEX-RN & NCLEX-PN. Contains More than 2000 Q&A Plus Review and Rationale in 517 PAGES.
NCSBN TEST BANK -for the NCLEX-RN & NCLEX-PN. Updated 2022/2023. Contains More than 2000 Q&A Plus Review and Rationale in 517 PAGES. (All Testable Questions for NCLEX-RN & NCLEX-PN)
By Expert1 , Uploaded: Jul 28, 2020
$20
Business> QUESTIONS & ANSWERS > CLM 031 EXAM (All)

CLM 031 EXAM
CLM 031 = 100% Question 1: 5b Select the statement that is correct concerning performance work statement (PWS) requirements: - All answers are correct. - PWS should describe requirements necessary...
By Book Worm, Certified , Uploaded: Nov 03, 2022
$5
*NURSING> QUESTIONS & ANSWERS > PHIL 347 Week 6 Checkpoint Quiz. Score 100/100 (All)
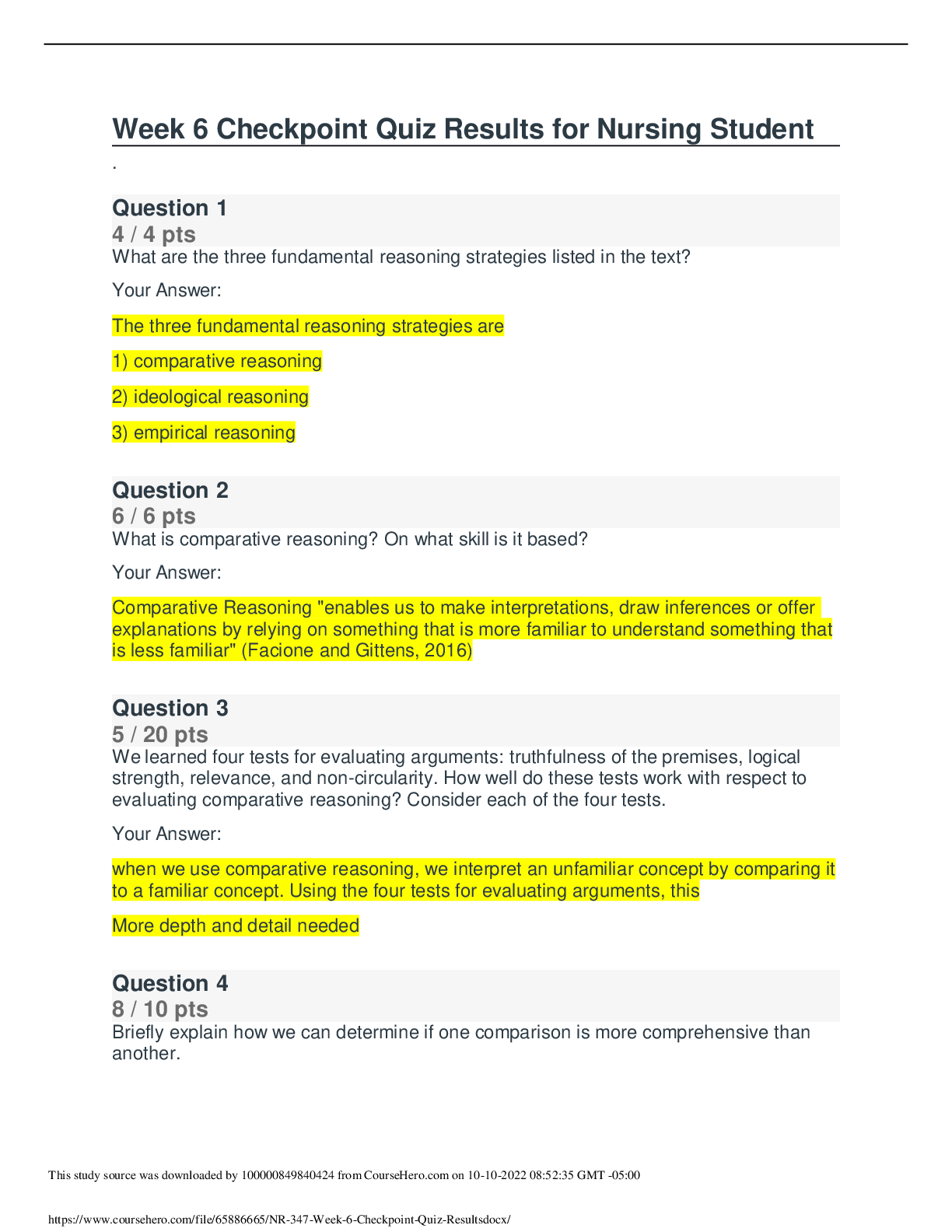
PHIL 347 Week 6 Checkpoint Quiz. Score 100/100
Question: What are the three fundamental reasoning strategies listed in the text? Question: What is comparative reasoning? On what skill is it based? Question: We learned four tests for evaluating...
By Amanda Rosales , Uploaded: Mar 24, 2021
$7
Business> QUESTIONS & ANSWERS > BUSINESS 1007 (All)
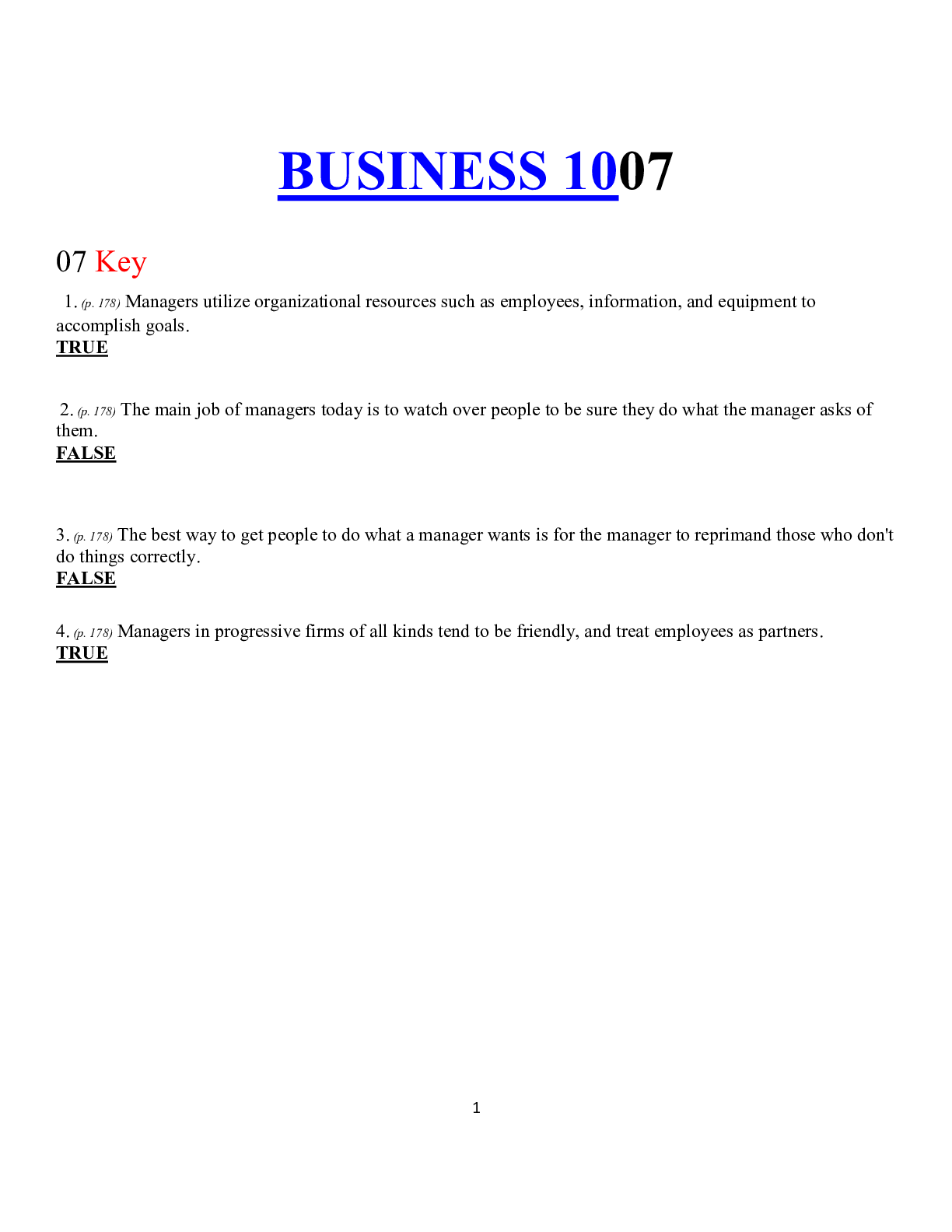
BUSINESS 1007
BUSINESS 1007 07 Key 1. (p. 178) Managers utilize organizational resources such as employees, information, and equipment to accomplish goals. 2. (p. 178) The main job of managers today is to w...
By Kirsch , Uploaded: Oct 19, 2019
$6
Anthropology> QUESTIONS & ANSWERS > KOR 352 FA19 101 week 8 Quiz. Already Graded A (All)

KOR 352 FA19 101 week 8 Quiz. Already Graded A
KOR 352 FA19 101: Week 8 Quiz Question 1 (0.25 points) Which of the following is not true of Kim and Finch’s observations during their field research in South Korea from 1997 to 2000? Question 1 o...
By Kirsch , Uploaded: Oct 17, 2019
$9
E-Commerce> QUESTIONS & ANSWERS > ESOC 316 Digital Commerce - University Of Arizona. Midterm Quiz. 20 Q&A. 100% Score (All)
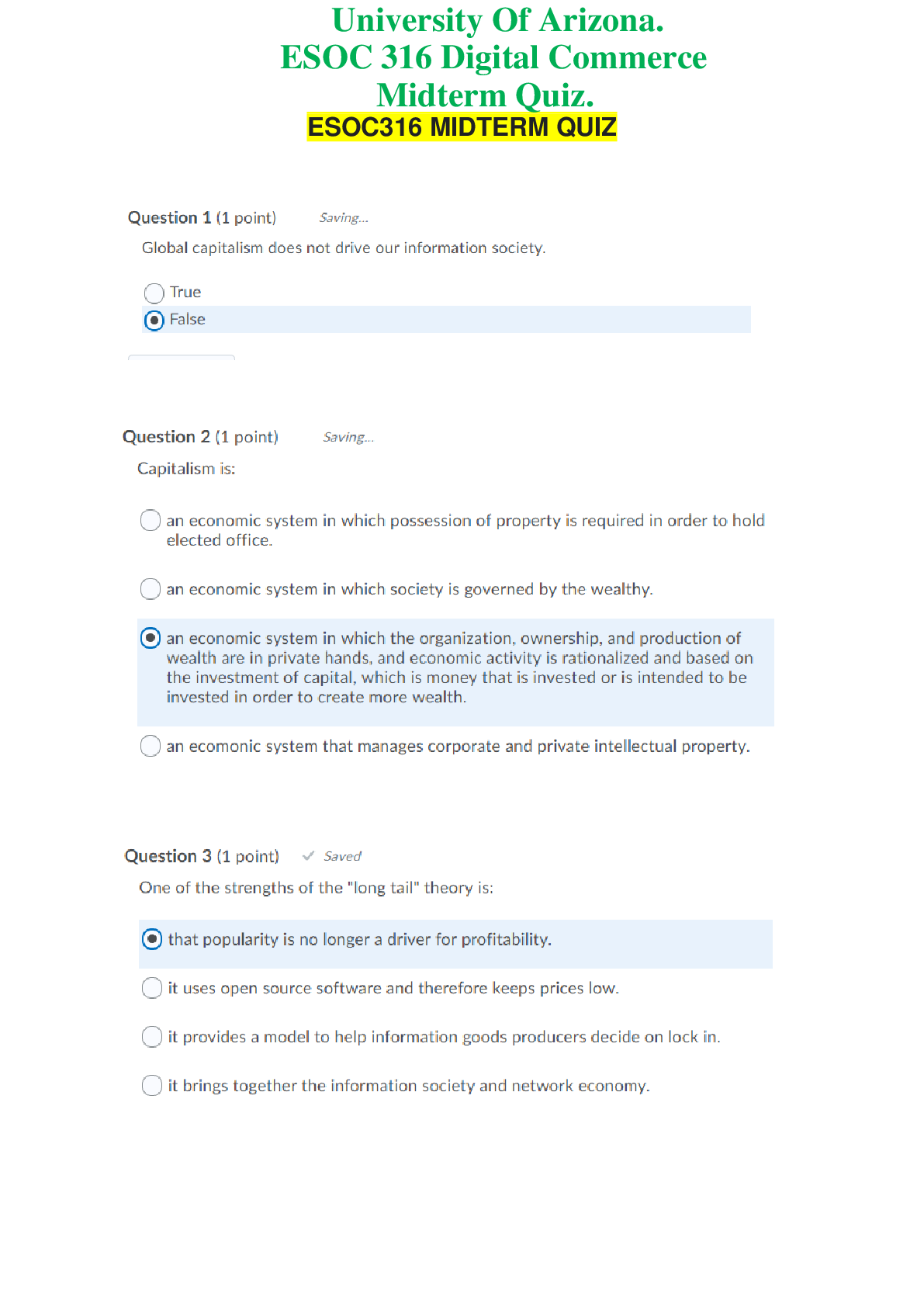
ESOC 316 Digital Commerce - University Of Arizona. Midterm Quiz. 20 Q&A. 100% Score
ESOC 316 Digital Commerce - University Of Arizona. Midterm Quiz. 20 Q&A. 100% Score ESOC316 MIDTERM QUIZQuestion 6 (1 point) Saved Information has several properties that make information goods...
By Kirsch , Uploaded: Oct 15, 2019
$9.5
Marketing> QUESTIONS & ANSWERS > Marketing Management Chapter 2 to Chapter 10 Q&A (All)

Marketing Management Chapter 2 to Chapter 10 Q&A
Chapter 2 to Chapter 10 Chapter 2: Developing Marketing Strategies and Plans GENERAL CONCEPT QUESTIONS Multiple Choice 66 Chapter 1: Marketing: Managing Profitable Customer Relationships...
By Kirsch , Uploaded: Oct 14, 2019
$10
Marketing> QUESTIONS & ANSWERS > MKT 530 Customer Relationship Management. 155 Questions and Answers (All)

MKT 530 Customer Relationship Management. 155 Questions and Answers
MKT 530 All Questions and Answers MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question. 1) As the manager of an organization that is att...
By Kirsch , Uploaded: Oct 14, 2019
$10
Art> QUESTIONS & ANSWERS > MAS 337 Exam 1. Graded A (All)

MAS 337 Exam 1. Graded A
MAS 337 Exam 1 Match the son with its corresponding region. 1.Oaxaca 2.Veracruz 3.Michoacan 4.Jalisco 5.Hidalgo 1. Son istemeno 2. Son Jarocho 3. Son Abajeno 4. Son Jalisciense 5. Son Huast...
By Kirsch , Uploaded: Oct 14, 2019
$6
Art> QUESTIONS & ANSWERS > MUS 337 Final Exam Graded 100%. (All)

MUS 337 Final Exam Graded 100%.
MUS 337 Final Daisy Moreno-Cota Fri Dec 11 12:59:42 PST 2015 Tone or aural color Volume and articulation of sounds Frequency of the tone Phonic structure or relationships between the sounds Dura...
By Kirsch , Uploaded: Oct 12, 2019
$9
Document information
Connected school, study & course
About the document
Uploaded On
May 02, 2022
Number of pages
76
Written in
Additional information
This document has been written for:
Uploaded
May 02, 2022
Downloads
0
Views
281






