Computer Science > EXAM > CSIS 340 Quiz 1 25 Questions and Answers- 100% Correct (All)
CSIS 340 Quiz 1 25 Questions and Answers- 100% Correct
Document Content and Description Below
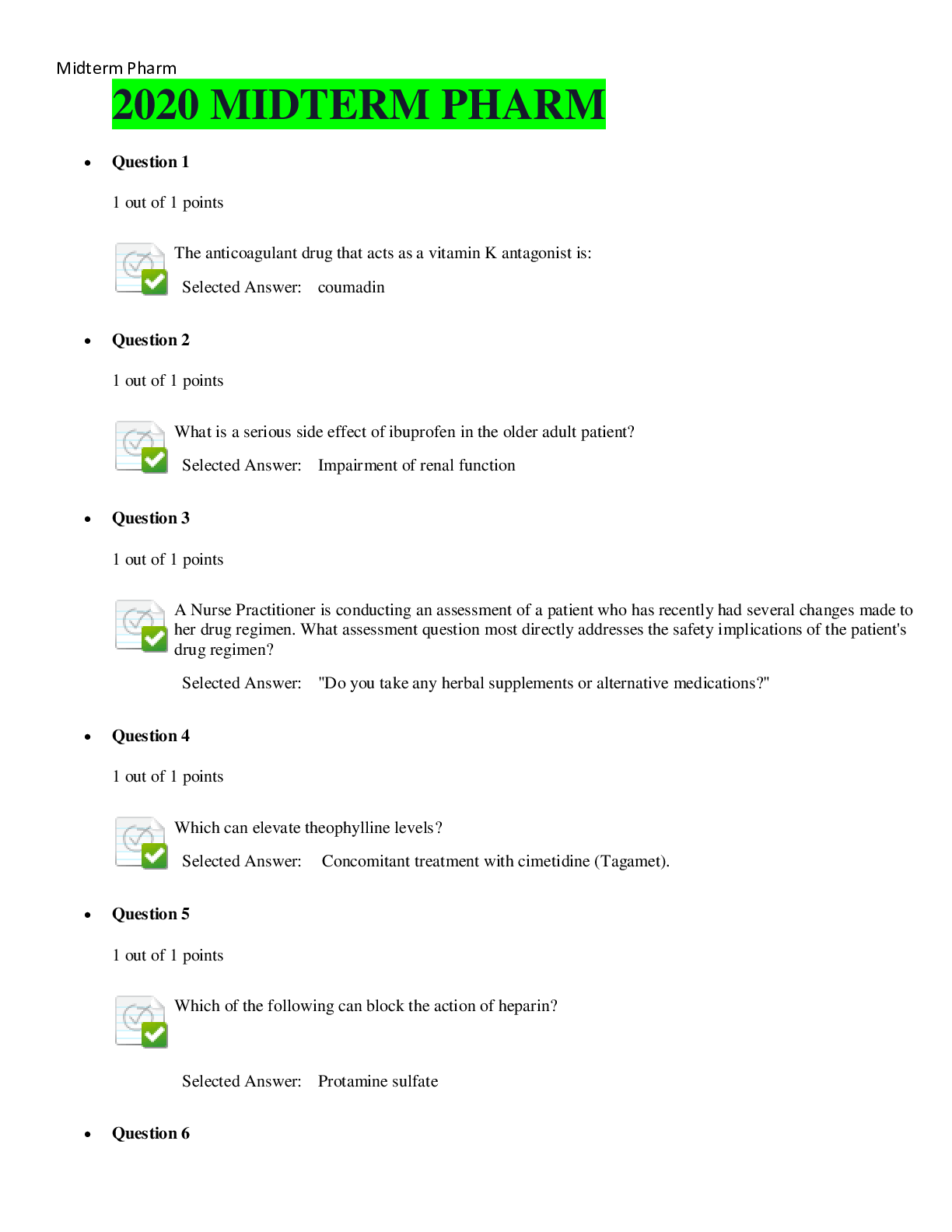
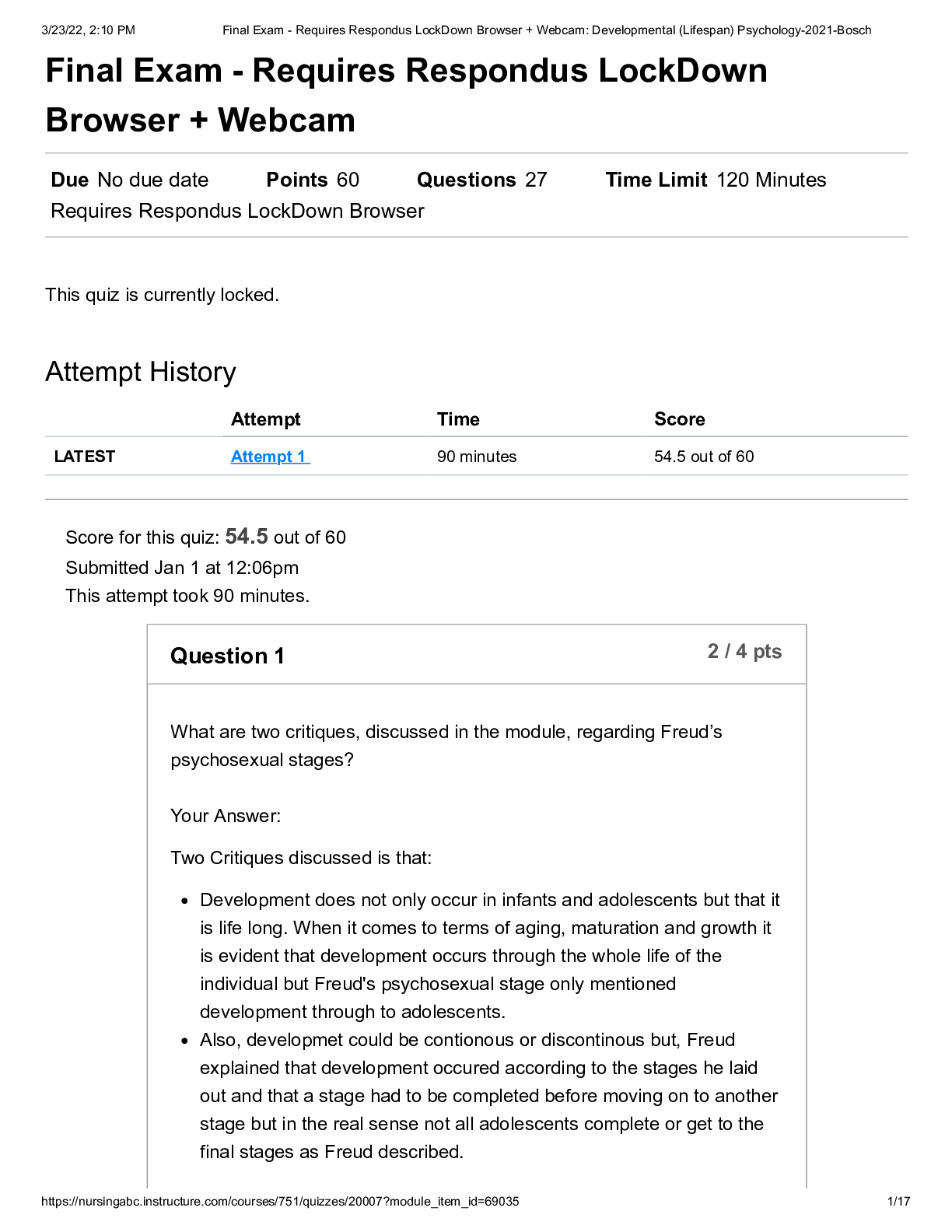
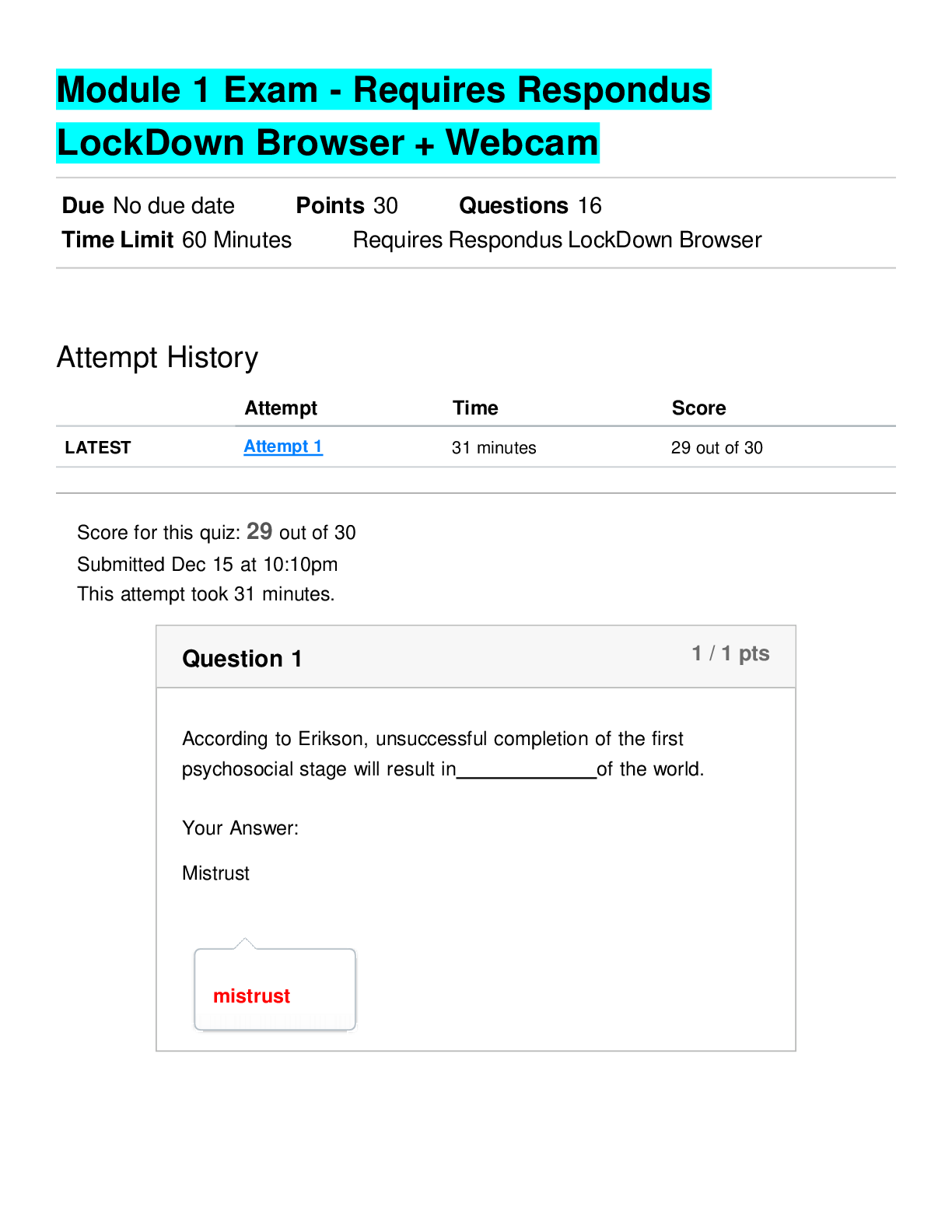
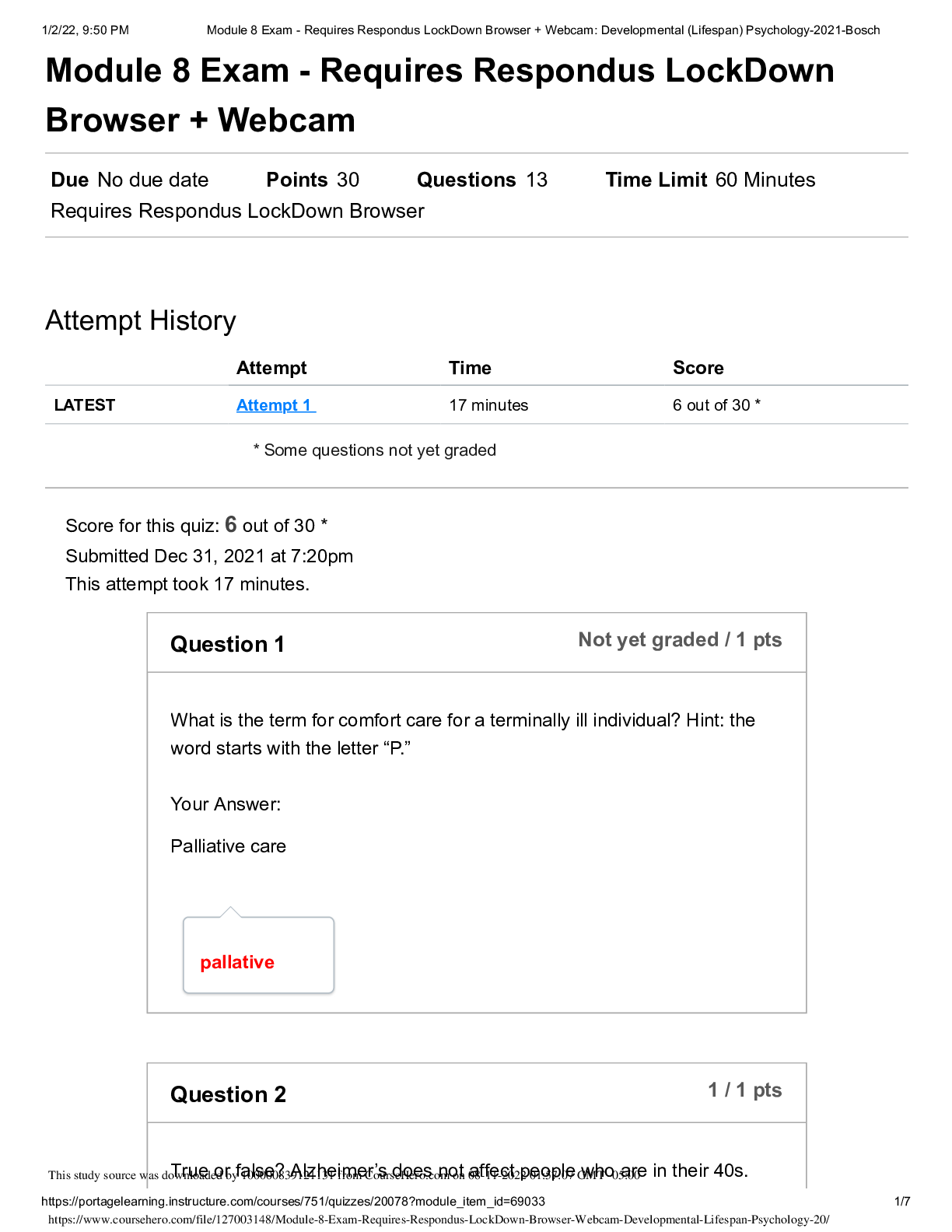
CSIS 340 QUIZ 1 • Question 1 When writing a one could state how often a supplier will provide a service or how quickly a firm will respond. For managed services, this document often cove... rs system availability and acceptable performance measures. • Question 2 As employees find new ways to improve a system or process, it is important to have a way to capture their ideas. can be understood as finding a better way or as a lesson learned. • Question 3 Which of the following security control design types does not prevent incidents or breaches immediately and relies on a human to decide what action to take? • Question 4 If human action is required, the control is considered . • Question 5 The most senior leader responsible for managing an organization’s risks is the chief privacy officer (CPO). Which of the following is not one of the responsibilities of the CPO? • Question 6 Although it is impossible to eliminate all business risks, a good policy can reduce the likelihood of risk occurring or reduce its impact. A business must find a way to balance a number of competing drivers. Which of the following is not one of these drivers? • Question 7 When trying to achieve operational consistency, which of following oversight phases performs the function of periodically assessing to ensure desired results are achieved? • Question 8 There are many distinct benefits to control measurement. Which of the following benefits is the result of determining which security controls to measure? • Question 9 Once an organization clearly defines its IP, the security policies should specify how to documents with marks or comments, and the data, which determines in what location the sensitive file should be placed. • Question 10 Privacy regulations involve two important principles. gives the consumer an understanding of what and how data is collected and used. provides a standard for handling consumer information. • Question 11 are formal written policies describing employee behavior when using company computer and network systems. • Question 12 are owned by an organization if they are created on the computer by company employees or if the assets were custom developed for and purchased by the organization. • Question 13 functions as a preventive control designed to prevent mistakes from happening. functions as a detective control intended to improve the quality over time by affording opportunities to learn from past mistakes. • Question 14 Which statement most clearly contrasts the difference between policies and procedures? Question 15 In the Build, Acquire, and Implement domain, the ability to manage change is very important. Thus, there are often set to avoid disrupting current services while new services are added. • Question 16 A communicates general rules that cut across the entire organization. • Question 17 Which of the following is not one of the four domains that collectively represent a conceptual information systems security management life cycle? • Question 18 The COBIT Align, Plan, and Organize domain includes basic details of an organization’s requirements and goals; this domain answers which of the following questions? • Question 19 4 out of 4 points Generally, regardless of threat or vulnerability, there will be a chance a threat can exploit a vulnerability. • Question 20 Which of the following statement states the difference between business liability and a business’s legal obligation? • Question 21 In the principle adopted by many organizations, you gain access only to the systems and data you need to perform your job. • Question 22 In business, intellectual property (IP) is a term applied broadly to any company information that is thought to bring an advantage. Protecting IP through security policies starts with human resources (HR). Which of the following is a challenge concerning HR policies about IP? • Question 23 ISS policies ensure the consistent protection of information flowing through the entire system. Which of the following is not one of the foundational reasons for using and enforcing security policies? • Question 24 is the act of protecting information and the systems that store and process it. • Question 25 A good security awareness program makes employees aware of the behaviors expected of them. All security awareness programs have two enforcement components, the carrot and the stick. Which of the following best captures the relationship of the two components? [Show More]
Last updated: 1 year ago
Preview 1 out of 11 pages

Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Apr 04, 2021
Number of pages
11
Written in
Additional information
This document has been written for:
Uploaded
Apr 04, 2021
Downloads
0
Views
50