Computer Science > EXAM > CSIS 340 Final Exam 1 QUESTIONS WITH VERIFIED ANSWERS, GRADED A+ (All)
CSIS 340 Final Exam 1 QUESTIONS WITH VERIFIED ANSWERS, GRADED A+
Document Content and Description Below
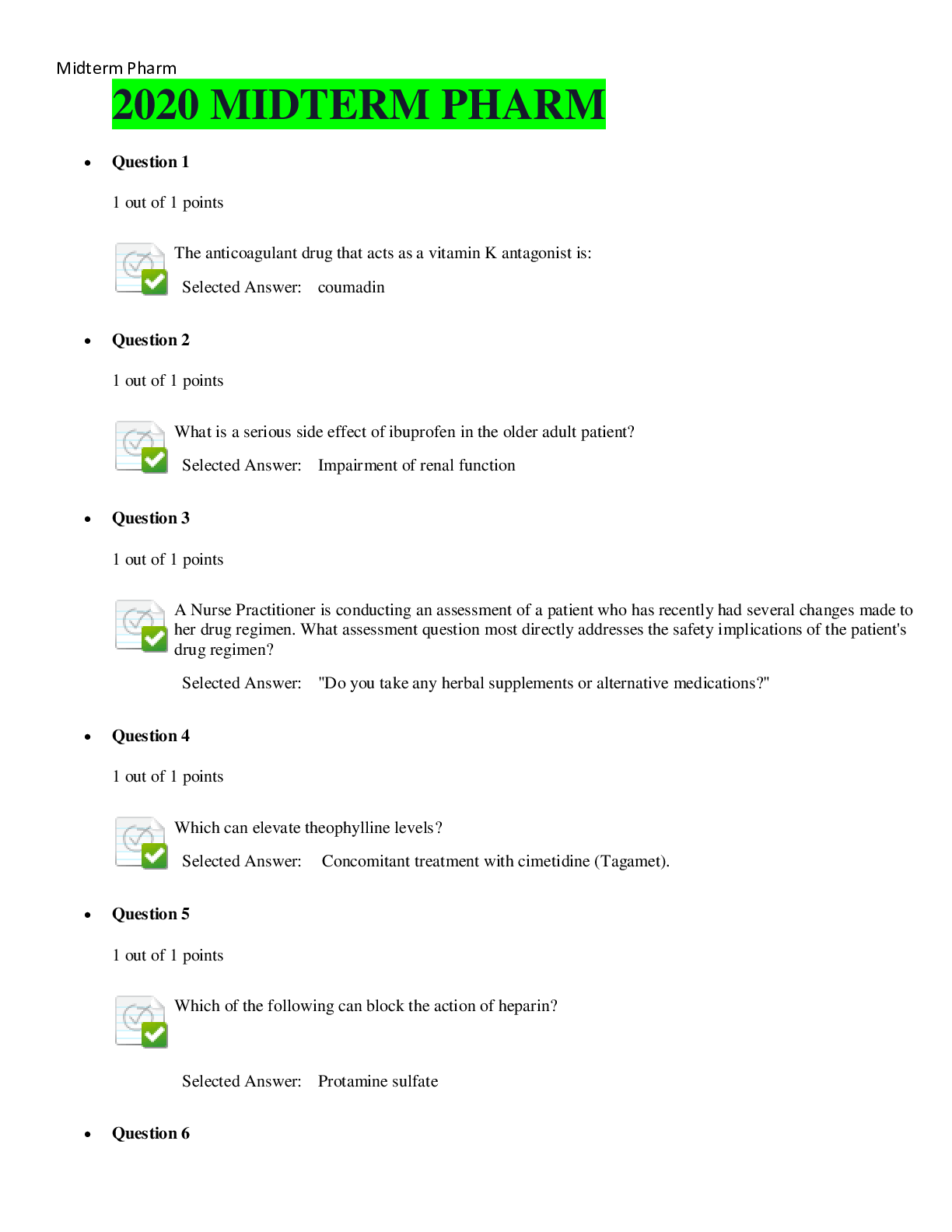
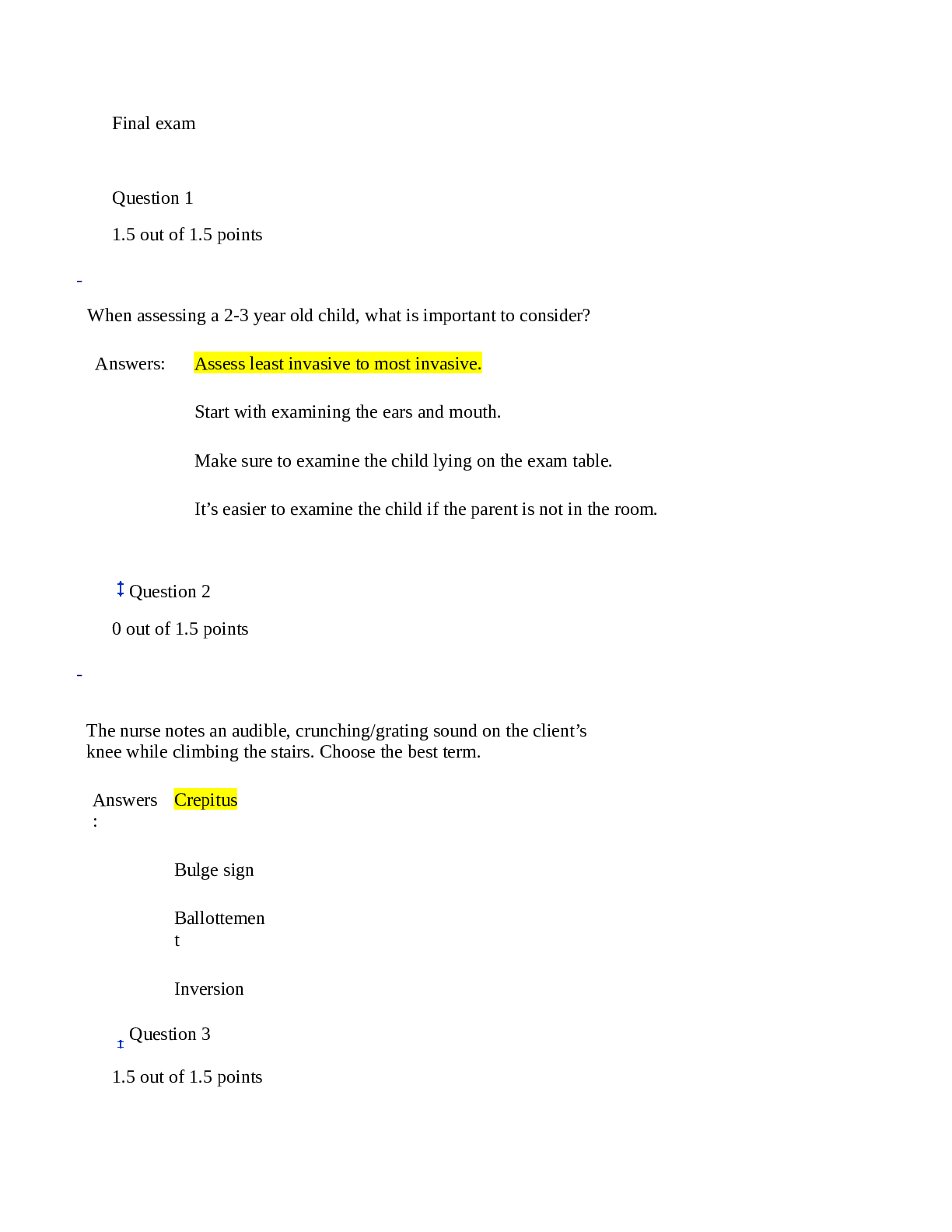
CSIS 340 Final Exam • Question 1 Web Services policies would be an example of domain. • Question 2 techniques can provide a security baseline for full operating systems and applic... ations? • Question 3 Two-factor authentication is a typical control used by employees to remotely access which of the following? • Question 4 Employer response to an employee posting company passwords on their social network site should include ? • Question 5 Simple security policy awareness requires that report suspicious activity? • Question 6 Which of the following does an acceptable use policy relate to? • Question 7 Security experts consider the weakest link in security. • Question 8 Which of the following includes guidelines under the LAN domain policies? • Question 9 Data classification for retention of information is typically for financial and tax records? • Question 10 The following documents help capture domain security control requirements? • Question 11 A can identify hosts on a network and determine services running on the hosts. • Question 12 The signs of an incident can be ? • Question 13 A business impact analysis requires an impact report, component reliance, and a . • Question 14 are especially useful for identifying unauthorized changes. • Question 15 Which of the following can you use to segment LANs? • Question 16 Why should a security policy implementation be flexible to allow for updates? • Question 17 occurs when you manipulate or trick a person into weakening the security of an organization? • Question 18 The following organization has offered reliable security policies in the past to help organizations develop proper infrastructure policies. • Question 19 The Security Compliance Committee ? • Question 20 Security policy enforcement can include ? • Question 21 It is necessary to retain data for what major reasons? • Question 22 protects data at rest from all type of breaches. • Question 23 The domain connects an organizations private network to the Internet? • Question 24 Once security policies are established, line management must ? • Question 25 Which of the following is a common cause of security breaches? • Question 26 A is the first step in building a business continuity plan (BCP) to minimize losses. • Question 27 The model was the first model developed to address the concerns of integrity. Originally published in 1977 • Question 28 Outdated application controls place a greater reliance on ? • Question 29 A is a specialized group of people whose purpose is to respond to major incidents. • Question 30 Which of the following should be in an information response team charter? • Question 31 Which is the first step in building a business continuity plan? • Question 32 Good reasons to monitor worker’s computer activities are when ? • Question 33 A(n) has an easier time bypassing security controls and hiding his or her tracks by deleting or altering logs and time stamps. • Question 34 The Risk Management Continuous Improvement Model includes ? • Question 35 To promote cultural change, the goal should be to make security policies ? • Question 36 Data in transit refers to what type of data? • Question 37 You can use a process to grant temporary elevated rights. • Question 38 software is capable of capturing usernames, passwords, and websites visited on a local workstation? • Question 39 A(n) ensures workers are conscious of security risks and how to deal with unexpected risk. • Question 40 often focuses on enterprise risk management across multiple lines of business to resolve strategic business issues. • Question 41 Which of the following is not an organizational challenge when implementing security policies? • Question 42 What is a strong indicator that awareness training is not effective? • Question 43 The model uses mandatory access control to enforce the DoD multilevel security policy. • Question 44 A standard describes the requirements for obtaining a domain name for use by external parties? • Question 45 What is an example of a manual control? • Question 46 Without a policy that leads to controls that restrict employees from installing their own software on a company workstation, a company could suffer which of the following consequences? • Question 47 Baseline standards for the LAN domain would include . • Question 48 determines how quickly a business process should be recovered. • Question 49 A privileged-level access agreement (PAA) is designed to heighten the awareness and accountability of? Question 50 Without sponsorship, users will be less likely to eagerly participate in awareness training. [Show More]
Last updated: 1 year ago
Preview 1 out of 13 pages

Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Apr 04, 2021
Number of pages
13
Written in
Additional information
This document has been written for:
Uploaded
Apr 04, 2021
Downloads
0
Views
48