Data Systems > FINAL EXAM > SEC 360 Week 8 Final Exam - 100% Correct Answers, Download Paper To Score An A (All)
SEC 360 Week 8 Final Exam - 100% Correct Answers, Download Paper To Score An A
Document Content and Description Below
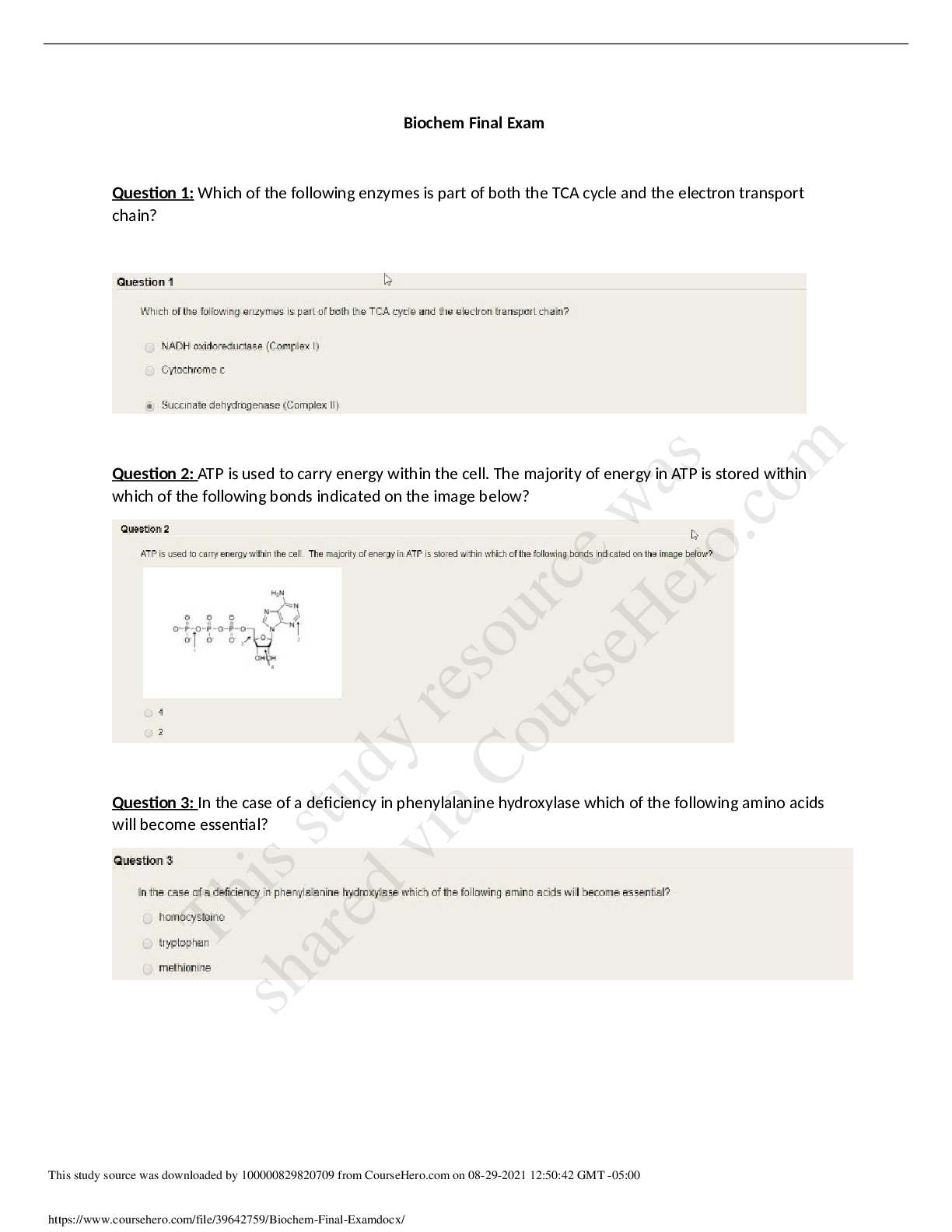
SEC 360 Week 8 Final (TCO 1) Which of the following should not be the basis for security policy? Legislation Corporate directives Corporate needs Vendor documentation Situation awareness repo... rting Lecture, pages 60-70 in the text (TCO 2) The of the 17 NIST control can be placed into the 10 IISSCC comprising the common body of knowledge for information security. technologies, domains, families controls, families, domains domains, families, technologies principles, domains, families controls, domains, principles (Lecture, Chapter 3 in the text) There are many controls that are grouped into control families that fit into the 10 domains. (TCO 2) What are the effects of security controls? Confidentiality, integrity, and availability Administrative, physical, and operational Detection, prevention, and response Management, operational, and technical Text, page 29 (TCO 3) Security management should ensure that policies established for information security distinguish the of assets, organize people by , and manage because that is the enemy of security. people, separation of duties, technology sensitivity, separation of duties, complexity technologies, importance, people taxonomy, separation of duties, complexity labels, accounts, complexity Chapters 2, 3, and 4 in the text, lecture (TCO 4) "There shall be a way for an individual to correct information in his or her records" is a clause that might be found in a . law code of ethics corporate policy fair information practices statement Any of the above (Chapter 7 in text, lecture) Similar statements are found in examples of each of these, although though for nonlegal, nonpolicy documents, many times "shall" is replaced by "will," "must be able to," or some other phrase. (TCO 5) Evaluation of ideas for security may use , which are that are not meant to be . criteria, models, solutions controls, abstractions, solutions solutions, abstractions, models models, abstractions, solutions models, controls, solutions (Chapter 5 in text, lecture) Security models are used to evaluate ideas, but they are abstractions of the real world and are not meant to be solutions. (TCO 6) Many believe that the most important physical security control is . closed-circuit television a good security plan an educated workforce certified security staff resources (Chapter 8 in text, lecture) Employee education in physical security has repeatedly been shown to pay off more than any other control. (TCO 7) The mission of the security operations center might best be described as . continuous monitoring maintaining the known good state policy enforcement reporting to management configuration management (Chapter 9 in text, lecture) The job of the SOC is to monitor the system for variations from the known good state, and to restore the known good state when variations occur. (TCO 8) A business impact analysis prioritizes systems for recovery. What are the highest priority systems called? Mission-critical systems Security Operations Center systems Mission-essential systems Backup and recovery systems Administrative systems Text, pages 128-129 (TCO 9) The basic elements of any access control model is a reference monitor that mediates access to by . files, people objects, subjects files, principals named resources, named users computer time, applications (Chapter 10 in text, lecture) The reference monitor mediates access to objects by subjects. The other answers are all examples rather than model elements. (TCO 10) Generally, are encrypted using symmetric cryptography and are encrypted using asymmetric cryptography. data, messages signatures, data channels, data messages, channels messages, information (Chapter 11 text, lecture) Generally, symmetric cryptography is used on data, and asymmetric cryptography for messages. (TCO 10) A company wants to assure customers that their online transactions are secure. Given this scenario, what should the company do? Use symmetric keys Issue smart cards Implement SSL Use IPSec Set up VPN connections (Chapter 11 in text) The customer should implement Secure Sockets Layer (SSL), which is the de facto standard for Public-Private Key cryptography. By using SSL, a customer will be able to see a lock icon and/or connect using an HTTPS address in their web browser address bar. (TCO 11) A firewall that disconnects an internal network from an external network is called a(n) . packet-filtering router circuit-level gateway application-level gateway stateful inspection firewall bridge firewall (Lecture, not covered in text) A circuit-level gateway breaks the circuit into an internal and an external part. A proxy can also do this, but this is not one of the answers in the question. (TCO 12) A good intrusion detection system will have all of the characteristics of the model and will be flexible enough to adapt to . Bell LaPadula, mandatory access control reference monitor, vulnerabilities Biba, vulnerabilities OSI, loss of availability reference monitor, loss of availability (Pages 281 & 282 in text, lecture) Intrusion detection must be always active, tamperproof, and simple enough to be thoroughly evaluated, and must be able to adapt to changes in vulnerability as well as other areas of situation awareness. (TCO 13) The SDLC Task Force was composed of four subgroups. Which one of the following subgroups recommended that IT centers and software assurance groups that are outside mainstream academia also include security components in their SDLC? Education subgroup Incentives subgroup Patching subgroup Software process subgroup IETF subgroup (Chapter 13 in text) The education subgroup recommended that security components be included as part of the SDLC for IT centers and software assurance groups that are outside mainstream academia. (TCO 1) Explain what is wrong with this policy clause, and show how you could fix it. People shall obey corporate policies. The clause is not enforceable. It leaves to the imagination the meaning of "corporate policies." At the least, it should name the corporate policies or point to them. For example, a phrase might be added to make it enforceable such as "according to the corporate policy handbook." (TCO 2) Briefly explain the relationship of the known good state to the three effects of security controls-- prevention, detection, and recovery. Security controls are used to prevent, detect, or recover from losses of the known good state and to return the system to its known good state. (TCO 3) Briefly explain how defense in depth is a management strategy for security. Defense in depth places preventive, detective, and recovery layers of security between information assets and potential users, or between subjects and objects. This method "hides" information assets behind overlapping layers of security protection. (TCO 4) Briefly explain what needs to be accomplished before your company monitors the activities of authorized users of your company systems, and then explain what should be accomplished to legally monitor the activities of a hacker (unauthorized user) of your system. Authorized users need to be notified that their activities will be monitored and must agree to that procedure. Hackers should also be notified that their activities are subject to monitoring. . (TCO 5) List the four characteristics of a reference monitor. A reference monitor mediates all access requests, is always active, is simple enough to be thoroughly evaluated, and is tamperproof. (TCO 6) Briefly explain why good physical security is critical to good information security. Access to physical devices by unauthorized people would render many, perhaps most, information security controls useless. Once a person can manipulate the hardware base upon which logical security depends, there is little that logical security can do to protect itself. (TCO 7) Explain how the information on media can be protected when the media is transported between secure spaces through a nonsecure space. The two primary methods of protection of media when being transported through unsecured space are encryption and using a courier. Encryption should render sensitive information on the media useless to anyone who happens to get hold of the media and does not have the decryption key. Sending by courier uses wrapping, accounting, and storage in a secure container to protect information during transport. (TCO 8) Explain the term cold site. A cold site is a facility that is ready for installation of computer hardware and software when needed. In some cases, the computer hardware is also installed but not operating. A cold site allows a company to switch from the main computing facility to the backup facility quickly, but not in a manner that is transparent to the users. (TCO 9) Distinguish between an access control list and a capabilities list. An access control list associates authorized subjects with objects, while a capabilities list associates accessible objects with authorized subjects. (TCO 10) Briefly explain why key management is a critical requirement for a good symmetric cryptographic solution. Symmetric cryptography uses the key as the shared secret; anyone who has the shared secret can use the cryptographic system to decrypt and encrypt data. (TCO 11) Firewalls can implement four kinds of controls: behavior, user, direction, and service controls. Briefly explain what service controls are. Service controls determine the type of Internet services that can be accessed by inbound or outbound requests for service. Generally, TCP port numbers or IP addresses are used to provide this control. (TCO 11) Analyze the types of firewalls and point out two of the most common building-block architectures. Application-level gateways and bastion hosts are two of the most common firewall building-block architectures. (TCO 12) For intrusion detection, briefly explain what Type 1 and Type 2 errors are. A Type 1 error is a false positive, which is when an event seems to be an intrusion but is not. A Type 2 error is a false negative, which is when an event seems not to be an intrusion but is an intrusion. (TCO 12) A packet-filtering router is not capable of understanding the context/data of a particular service. Evaluate the types of security devices available and conclude what would be the best choice to perform this function. This function is best performed higher up in the OSI by an application-level gateway often called firewalls. (TCO 13) Explain how a worm propagates itself. A worm is a program that propagates itself through communication protocols. Worms do not need assistance or intervention from a user. [Show More]
Last updated: 10 months ago
Preview 1 out of 8 pages

Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Jul 10, 2023
Number of pages
8
Written in
Additional information
This document has been written for:
Uploaded
Jul 10, 2023
Downloads
0
Views
31