SAPPC Exam Study Guide with Complete Solutions
Document Content and Description Below
Describe the purpose, intent, and security professional's role in each step of the Command Cyber Readiness Inspections (CCRI) process - ANSWER Defining the scope, the inspection phase, documentation o... f observations, and reporting findings. A security professional would have responsibilities in defining the scope of the inspection, overseeing the self-inspection and remediation efforts, and coordinating with the CCRI team throughout the remainder of the process List two factors that should be considered when determining position sensitivity - ANSWER (1) Level of access to classified information (2) IT level needed (3) Duties associated with position Explain the process for responding to a "spillage" - ANSWER 1. Detection (implied) 2. Notification and preliminary inquiry 3. Containment and continuity of operations 4. Formal inquiry 5. Resolution 6. Reporting Explain how the adjudication process contributes to effective risk management of DoD assets - ANSWER Determines an individual's loyalty, reliability, and trustworthiness are in the best interest of national security Explain why access control measures are contingent on Force Protection Conditions - ANSWER The Force Protection Conditions determine the amount of control measures needed to be taken in response to various levels of threats against military facilities or installations. Define the purpose and function of the militarily critical technologies list (MCTL) - ANSWER Serves as a technical reference for the development and implementation of DoD technology, security policies on international transfers of defense-related goods, services, and technologies as administered by the Director, Defense Technology Security Administration (DTSA). Describe how authorization of Limited Access Authority impacts risk to DoD assets - ANSWER Increases risk by allowing a foreign national access to classified information. Reduces risk by ensuring Foreign Nationals with a unique or unusual skills set have been properly investigated, adjudicated or vetted before being granted access to specific pieces of classified information only. List three different types of threats to classified information - ANSWER (1) Insider threat (2) Foreign Intelligence entities (3) Cybersecurity Threat What is the security professionals' role in pursuing and meeting cyber security goals? - ANSWER The role of the cyberspace workforce is to "secure, defend, and preserve data, networks, net-centric capabilities, and other designated systems by ensuring appropriate security controls and measures are in place, and taking internal defense actions" (DoDD 8140.01). Per DoDI 8500.01, Cybersecurity (March 14, 2014), personnel occupying cybersecurity positions must be assigned in writing and trained / qualified in accordance with their role. Identify specific baseline administrative and/or physical security controls applicable to each system categorization - ANSWER Controls are identified by enumerating the common controls, identifying those relevant to the categorization level as defined in NIST SP 800-53, potentially tailored by the Authorizing Official, and overlays are applied based on the nature of the system. List three (3) factors for determining whether US companies are under Foreign Ownership Control of Influence (FOCI) - ANSWER 1. Record of economic and government espionage against the US targets. 2. Record of enforcement/engagement in unauthorized technology transfer. 3. Type and sensitivity of the information that shall be accessed. 4. The source, nature and extent of FOCI. 5. Record of compliance with pertinent US laws, regulations and contracts. 6. Nature and bilateral and multilateral security and information exchange agreements. 7. Ownership or control in whole or part, by a foreign government. How does lack of attention to the concept of compilation of information introduce risks to DoD assets? - ANSWER 1. Unauthorized disclosure 2. Misclassification 3. Security Violation 4. Improper safeguarding 5. Improper dissemination 6. Improper handling 7. Improper destruction 8. Data Spill List at least three indicators of insider threats - ANSWER 1. Failure to report overseas travel or contact with foreign nationals. 2. Seeking to gain higher clearance or expand access outside the job scope. 3. Engaging in classified conversations without a need to know. 4. Working hours inconsistent with job assignment or insistence on working in private. 5. Exploitable behavior traits. 6. Repeated security violations. 7. Attempting to enter areas not granted access to. 8. Unexplained affluence/living above one's means. 9. Anomalies (adversary taking actions which indicate they are knowledgeable to information). 10. Illegal downloads of information/files. What is the difference between physical security surveys and physical security inspections? - ANSWER A physical security survey is a formal record assessment of an installation's overall security posture; whereas a physical security inspection is a formal record of compliance of physical procedures and measures implemented by a unit or activity to protect its assets Describe the security professional's possible roles in handling a security incident (*hint SSRII*) - ANSWER 1. Secure 2. Safeguard 3. Report 4. Inquire 5. Investigate List at least three individuals in the personnel security investigation (PSI) process and describe their roles - ANSWER Facility Security Officer/Security Manager/Security Officer/Security Coordinator/Security Assistant: initiates, reviews, forwards E-Qip investigation to investigation service provider (ISP) Subject: Completes forms and provides additional information if required Investigator: Conducts PSI Adjudicator: Determines security clearance eligibility What are at least three principle incidents/events required to be reported to DoD counterintelligence (CI) organizations? - ANSWER 1. Espionage 2. Sabotage 3. Terrorism 4. Cyber 5. Insider Threat List three elements that a security professional should consider when assessing and managing risks to DoD assets - ANSWER 1. Asset 2. Threat 3. Vulnerability 4. Risk 5. Countermeasures Explain how visitor identification control methods are used to effectively control access to facilities - ANSWER Ensure only authorized personnel and materials that enter and exit from an installation or facility are properly identified, verified, and authenticated Briefly define a Special Access Program - ANSWER A program established for a specific class of classified information that imposes safeguarding and access requirements that exceed those normally required for information at the same classification level Identify the three core components of the Risk Assessment process - ANSWER 1. Asset criticality 2. Threat Assessment 3. Vulnerability Assessment List at least three (3) types of security briefings that help manage risks to DoD assets - ANSWER 1. Initial orientation 2. Annual refresher 3. Threat awareness 4. Foreign Travel 5. Derivative classification 6. Debriefings 7. Termination briefing 8. Counterintelligence briefing Who determines or identifies when physical security surveys and inspections are required? - ANSWER 1. DoD Component Commanders. 2. Program Managers 3. Security Managers 4. Physical Security Specialists/Officers List three transmission and transportation requirements that help manage risks to DoD assets - ANSWER 1. Safeguarding 2. Briefings 3. Documentation 4. Personal control 5. Pre-coordination 6. Preparing for transportation (packaging) 7. Utilizing proper methods of transmission/transportation based on classification level 8. Intended recipients have proper clearance/eligibility and need to know (or access) 9. Capability to properly store classified information List three types of safeguarding procedures for classified information - ANSWER 1. Proper storage 2. Proper handling 3. Approved disposition 4. Proper transmission/transportation methods 5. Receipt use, when required 6. Dissemination 7. Physical security measures 8. Technical, administrative, and personnel control measures (deleted access control as these measures constitute access control) 9. Develop emergency plan Describe the purpose of the Foreign Visitor Program - ANSWER To track and approve access by a foreign entity to information that is classified; and to approve access by a foreign entity to information that is unclassified, related to a US Government contract, or contractor/government facility visits covered by International Traffic in Arms Regulations (ITAR) Explain how effective implementation of the continuous evaluation process contributes to management of the risks to DoD assets - ANSWER Ensures that individuals with security clearance eligibility and access are continuously assessed through utilization of accessible databases and other lawfully available information; continue to meet adjudicative standards; and that any issues that may arise are promptly reported and addressed Briefly describe the purpose of the DD Form 254 - ANSWER Convey security requirements and classification guidance, and provide handling procedures for classified materials received and/or generated under a classified contract List the three categories of Special Access Programs - ANSWER 1. Acquisition 2. Intelligence 3. Operations and support Identify the five Cognizant Security Agencies (CSAs) and describe their role in the National Industrial Security Program (NISP) - ANSWER 1. Department of Defense 2. Director of National Intelligence 3. Department of Energy 4. Nuclear Regulatory Commission 5. Department of Homeland Security. Role: implement and oversee an Industrial Security Program to safeguard classified information with cleared industry under the respective CSA's jurisdiction. What are the five steps in the DoD risk management model - ANSWER 1. Assess Assets 2. Assess Threats 3. Assess Vulnerabilities 4. Assess Risks 5. Determine Countermeasures What are 3 core components of the risk assessment process? - ANSWER 1. Asset criticality 2. Threat assessment 3. Vulnerability assessment What do SAPs aim to achieve? - ANSWER 1. Protect technological breakthroughs 2. Cover exploitation of adversary vulnerabilities 3. Protect sensitive operational plans 4. Reduce intelligence on U.S. capabilities What are the SAP Lifecycle - ANSWER 1. Establishment (is extra protection warranted?) 2. Management and Administration (continued need? processed followed?) 3. Apportionment (proper measures in place? approval received) 4. Disestablishment (program no longer needed?) What is the five-step OPSEC process? - ANSWER 1. Identify critical information 2. Analyze threats 3. Analyze vulnerabilities 4. Assess risks 5. Apply OPSEC countermeasures What are the 5 steps to RMF? - ANSWER 1. Identify the critical assets that require protection 2. Identify undesirable events and expected impacts 3. Value and prioritize assets based on the consequence of loss 4. Assess the risks and 5. Determine countermeasures What the 5 categories of assets? - ANSWER 1. People 2. Information 3. Equipment 4. Facilities and 5. Activities and Operations Define the four levels of asset impact loss - ANSWER 1. Critical indicates that compromise to the assets targeted would have grave consequences leading to loss of life, serious injury, or mission failure. The rating scale is from 50-100 2. A High value indicates that a compromise to assets would have serious consequences resulting in the loss of classified or highly sensitive data that could impair operations affecting national interests for a limited period of time. The rating scale is from 13-50 3. An asset value of Medium indicates that a compromise to the assets would have moderate consequences resulting in the loss of confidential, sensitive data or costly equipment/property that would impair operations affecting national interests for a limited period of time. The rating scale is from 3-13 4. A Low value indicates that there is little or no impact on human life or the continuation of operations affecting national security or national interests. The rating scale is from 1-3 [Show More]
Last updated: 1 year ago
Preview 1 out of 10 pages

Reviews( 0 )
Recommended For You
*NURSING> EXAM > NR 507 / NR507 Advanced Pathophysiology Study Guide with Practice Questions |Rated A Guide| Latest 2020 / 2021 | Chamberlain College (All)

NR 507 / NR507 Advanced Pathophysiology Study Guide with Practice Questions |Rated A Guide| Latest 2020 / 2021 | Chamberlain College
NR 507 / NR507 Advanced Pathophysiology Study Guide with Practice Questions |Rated A Guide| Latest 2020 / 2021 | Chamberlain College 1. Types of anemia reduction of the total number of erythrocytes...
By nurse_steph , Uploaded: Dec 20, 2020
$13
Business Administration> EXAM > ARF Title 22 Study Guide with 100% Solutions (All)

ARF Title 22 Study Guide with 100% Solutions
ARF Title 22 Study Guide 1 Disaster Drills to be conducted - At least every 6 months Licensing will conduct a follow-up inspection of a facility for which a license was issued within ____ days...
By MARIA J , Uploaded: Aug 03, 2023
$1
Health Care> EXAM > NUR 155 STUDY GUIDE EXAM 2 2023 Full and Revised Study Guide with Complete solutions (All)
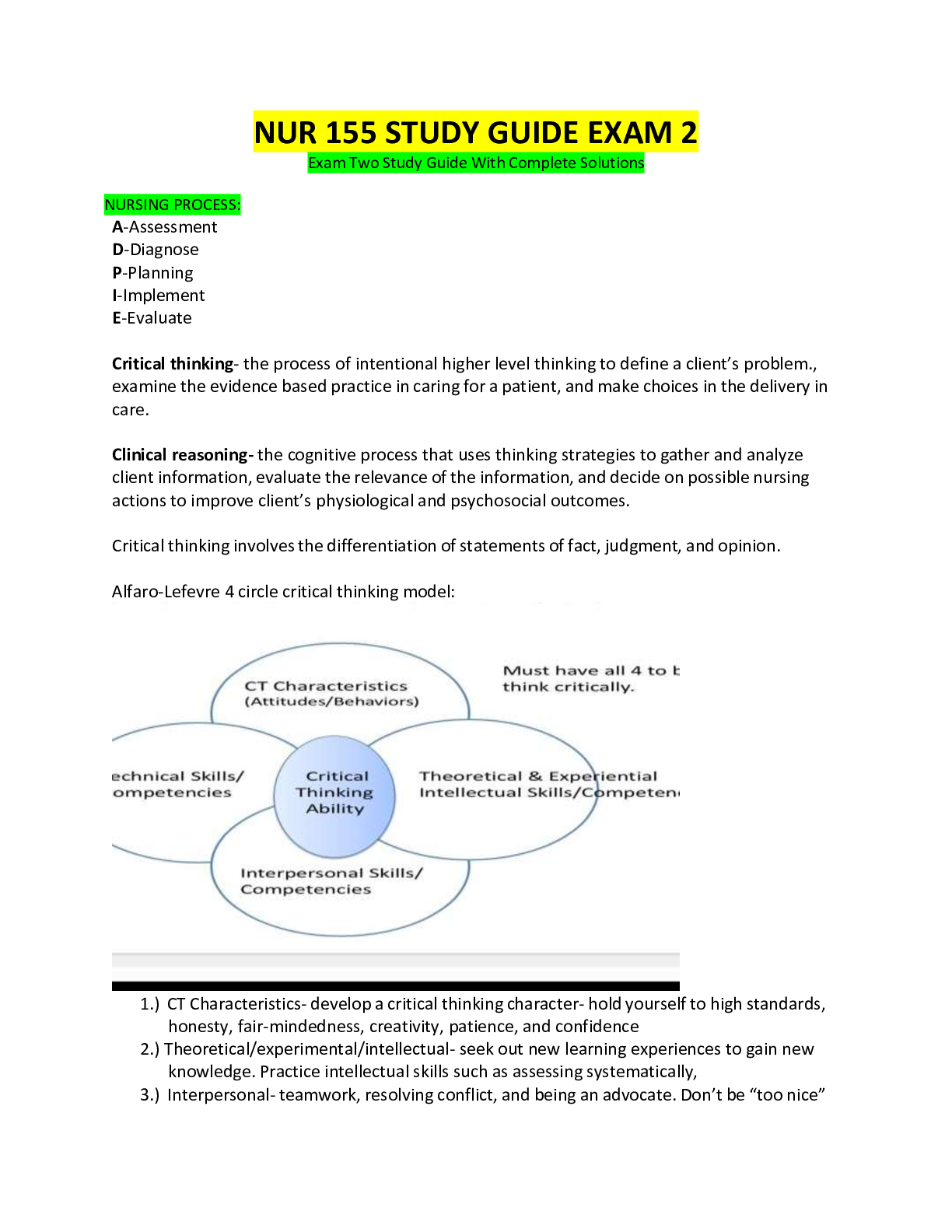
NUR 155 STUDY GUIDE EXAM 2 2023 Full and Revised Study Guide with Complete solutions
NUR 155 STUDY GUIDE EXAM 2 Exam One Study Guide With Complete Solutions NURSING PROCESS: A-Assessment D-Diagnose P-Planning I-Implement E-Evaluate Critical thinking- the process of intentio...
By Tutorsammy , Uploaded: Apr 24, 2023
$6
Health Care> EXAM > NUR 155 Exam 2 2023 Full and Revised Study Guide with Complete solutions (All)
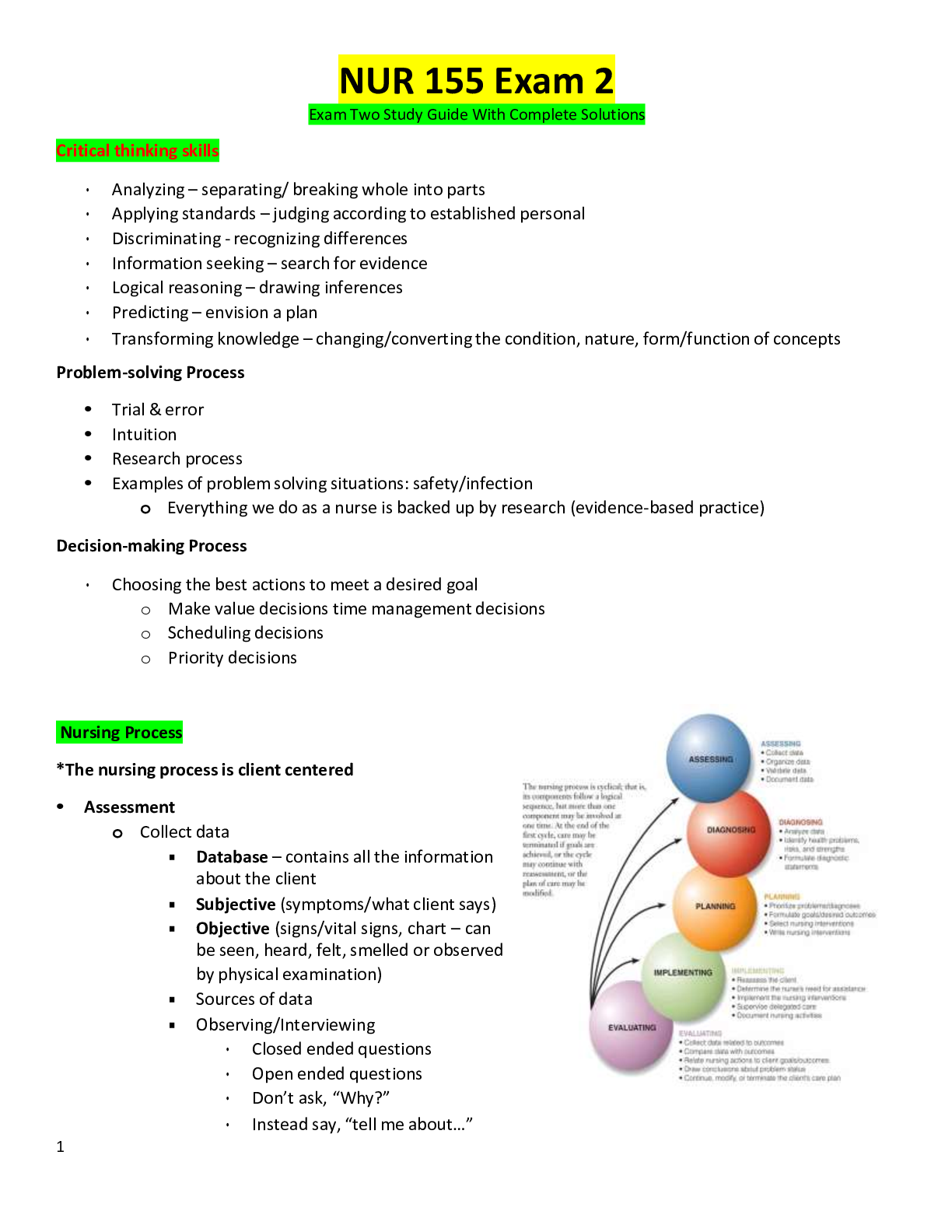
NUR 155 Exam 2 2023 Full and Revised Study Guide with Complete solutions
NUR 155 Exam 2 Exam One Study Guide With Complete Solutions Critical thinking skills • Analyzing – separating/ breaking whole into parts • Applying standards – judging according to established per...
By Tutorsammy , Uploaded: Apr 24, 2023
$6
*NURSING> EXAM > MATERNITY NURSING STUDY GUIDE WITH OVER 100+ QUESTIONS AND ANSWERS PREVAILLING 2022/2023 (All)

MATERNITY NURSING STUDY GUIDE WITH OVER 100+ QUESTIONS AND ANSWERS PREVAILLING 2022/2023
1. The nurse auscultates crackles throughout all lung fields and measures a heart rate of 132 bpm, a respiratory rate of 30, and blood pressure of 102/54 mm Hg in a client recovering from an esophagec...
By simon , Uploaded: Mar 29, 2023
$9
*NURSING> EXAM > NR 511 Week 3 Study Guide with Answers GradeAplus (All)

NR 511 Week 3 Study Guide with Answers GradeAplus
Discuss that the majority of dyspnea complaints are due to cardiac or pulmonary decompensation. Explain the differences between intra-thorax and extra-thorax flow disorders. Identify at least three...
By GradeAplus , Uploaded: Apr 28, 2020
$15
Medicine> EXAM > AORN Periop 101 Final Exam Study Guide with complete solution 2022/2023 (All)

AORN Periop 101 Final Exam Study Guide with complete solution 2022/2023
1.This type of needle point is what you would expect to be needed for suturing friable tissue such as the liver. - ANSWER What is a Blunt needle point? 2.These particular wound closing items are av...
By Nancylect , Uploaded: Jul 27, 2022
$9
Medicine> EXAM > AORN Periop 101 Final Exam Study Guide with complete solution 2022/2023 (All)

AORN Periop 101 Final Exam Study Guide with complete solution 2022/2023
1.This type of needle point is what you would expect to be needed for suturing friable tissue such as the liver. - ANSWER What is a Blunt needle point? 2.These particular wound closing items are av...
By MARKALLAN , Uploaded: Jul 27, 2022
$9
*NURSING> EXAM > ATI Pharmacology Study Guide with Answers 2nd Set (All)
.png)
ATI Pharmacology Study Guide with Answers 2nd Set
ATI Pharmacology Study Guide with Answers 2nd Set
By kate academia , Uploaded: Jul 22, 2022
$19.5
BioChemistry> EXAM > WGU C787 STUDY GUIDE WITH COMPLETE SOLUTION (All)

WGU C787 STUDY GUIDE WITH COMPLETE SOLUTION
WGU C787 STUDY GUIDE WITH COMPLETE SOLUTION DEFINE MACRONUTRIENTS Ans- NUTRIENTS REQUIRED IN LARGER AMOUNTS EX. CARBS, FATS, PROTEINS DEFINE MICRONUTRIENTS Ans- NUTRIENTS REQUIRED IN SMALLER AMOUN...
By Prof.Pierro , Uploaded: Jul 08, 2022
$7
Document information
Connected school, study & course
About the document
Uploaded On
Nov 23, 2022
Number of pages
10
Written in
Additional information
This document has been written for:
Uploaded
Nov 23, 2022
Downloads
0
Views
58






