Business > EXAM > CSIS 330 Quiz 6 Liberty University answers complete solutions; Already Graded A. (All)
CSIS 330 Quiz 6 Liberty University answers complete solutions; Already Graded A.
Document Content and Description Below
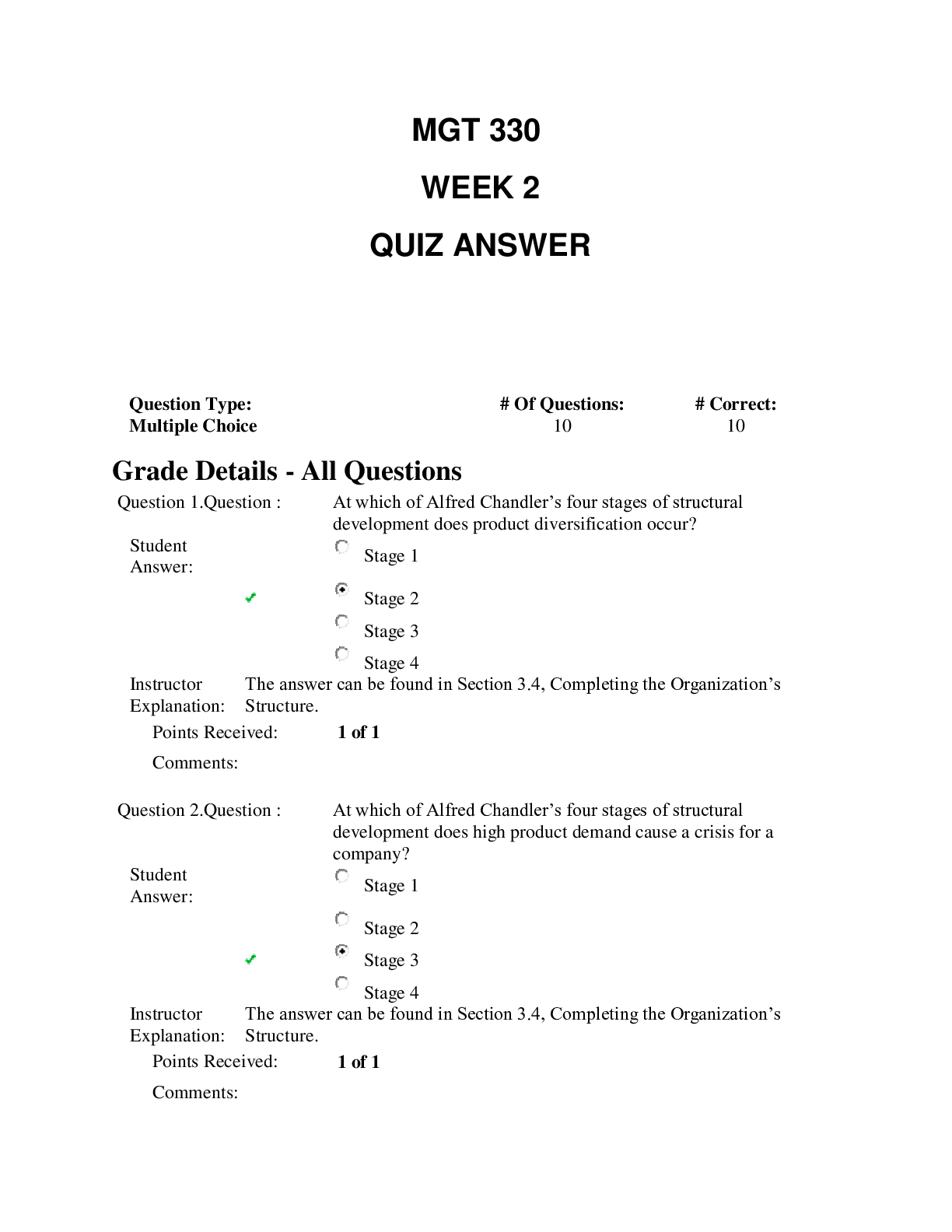
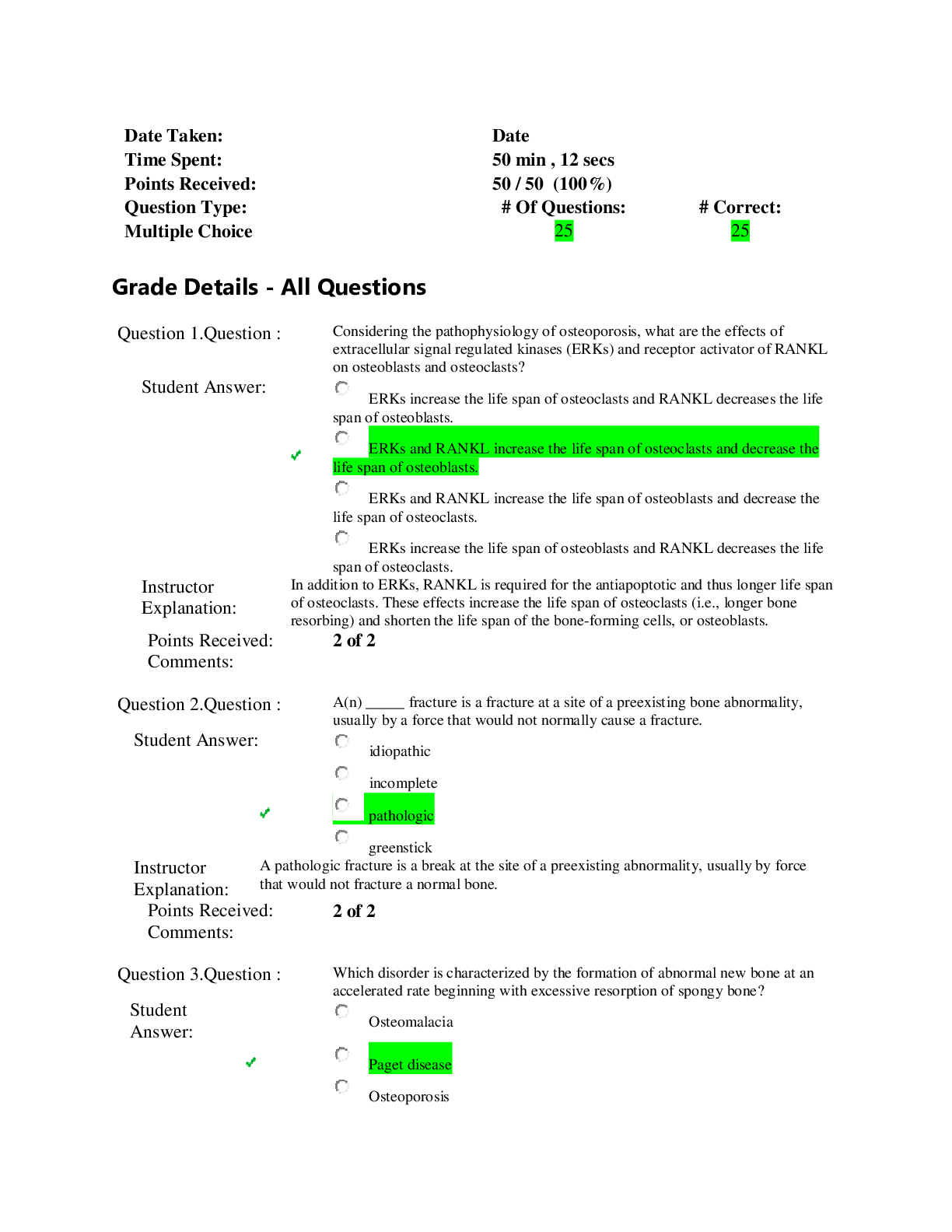
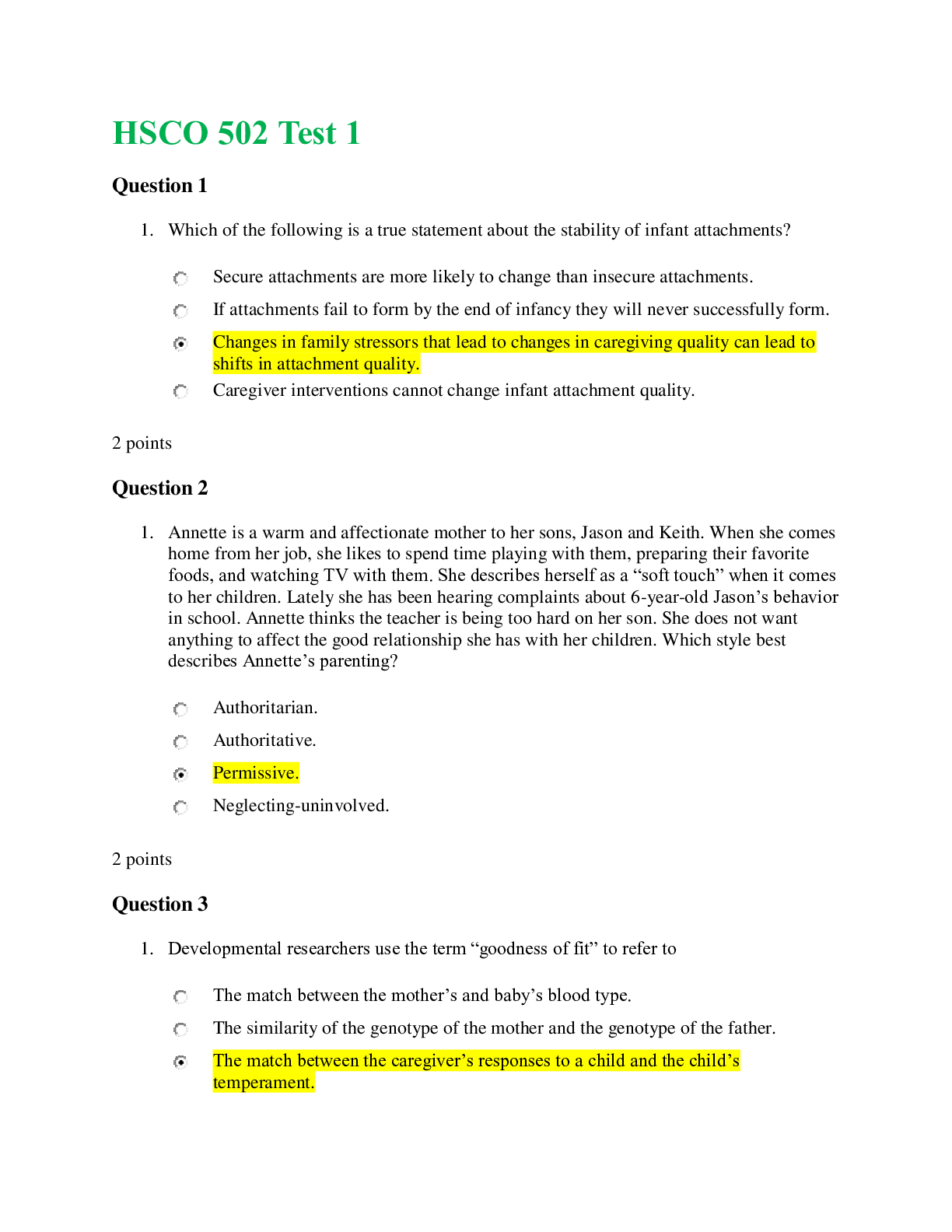
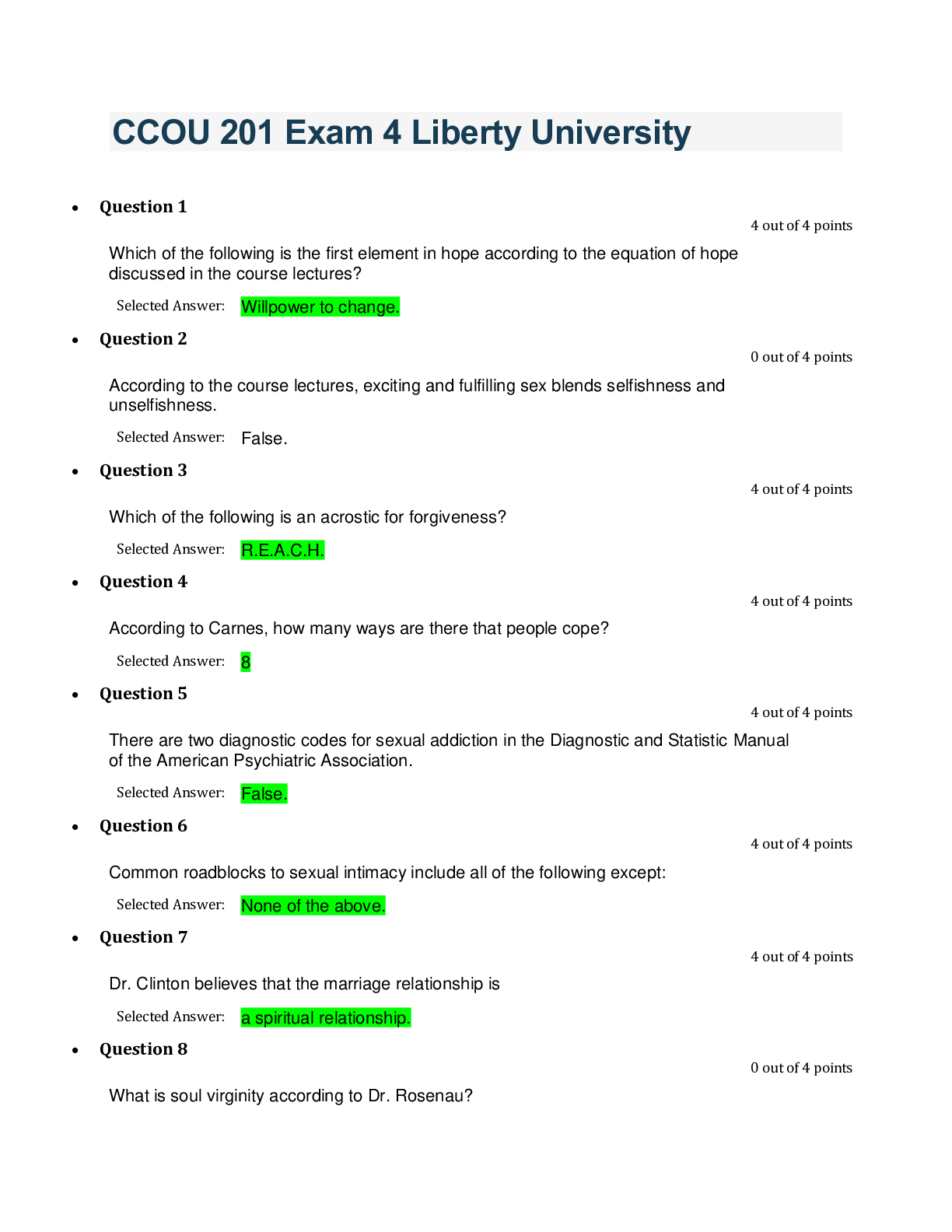
CSIS 330 Final • Question 1 Which of the following is a common leased line circuit in North America? • Question 2 According to your textbook, during the queuing proces... s, if the number of packets to be queued continues to increase, what happens? • Question 3 Which of the following is a dedicated connection from the service provider to the customer’s premises? • Question 4 __________________________ involves increased priority for services like telephony or video distribution. • Question 5 According to the textbook, the creation and interconnection of robust _____________________ has had a profound effect on communication, and has become the new platform on which modern communications occur. • Question 6 Fault tolerant networks depend on multiple paths between the source and destination of a message. If one path fails, the messages can be instantly sent over a different link. • Question 7 The simplest peer-to-peer network consists of ________ directly connected computers using a wired or wireless connection. • Question 8 Which of the following type of networks is often set up by individuals who work from a home or remote office and need to connect to a corporate network or other centralized resource? • Question 9 A ____________________________ is used to translate IP addresses to web addresses. • Question 10 By default, there is no authentication required to access the User EXEC mode from the console. • Question 11 What error message is displayed in the IOS if not enough characters were entered for the IOS to recognize the command? • Question 12 All devices within a network must have a unique IP address for communication between devices to function properly. • Question 13 Which mode is used to configure one of the physical or virtual lines? • Question 14 According to the textbook, while all devices come with a default IOS and feature set, it is possible to upgrade the IOS version or feature set to obtain additional capabilities. • Question 15 According to the textbook, the use of ______________________ is the primary means of enabling devices to locate one another and establish end-to-end communication of the Internet. • Question 16 Telnet sessions require active networking services on a device with at least one active interface configured with an Internet address. • Question 17 Which layer of the OSI model has protocols that describe the mechanical, electrical, functional, and procedural means to activate, maintain, and deactivate physical connections for bit transmissions to and from a network device? • Question 18 The seven OSI model layers are more often referred to by number rather than by name. Which layer number is the session layer in the OSI model? • Question 19 Which two addresses are contained in an IP packet? Selected Answer: None of the above • Question 20 _________________ is a protocol that governs the way that a web server and a web client interact. • Question 21 Which of the following protocols is not associated with the Transport layer of the OSI model? • Question 22 ___________ is the process used by a receiving device to remove one or more of the protocol headers. • Question 23 What is the binary equivalent of the decimal number 119? • Question 24 Is the binary number 00000011 odd or even? • Question 25 What is the binary equivalent of the hexadecimal number FE? • Question 26 What is the binary equivalent of the hexadecimal number AA? • Question 27 What is the decimal equivalent of the binary number 00101101? • Question 28 What is the decimal equivalent of the binary number 00011111? • Question 29 Which of the following is not a type of UTP cable? • Question 30 Which of the following is not one of the three main types of copper media used in networking? • Question 31 The combined use of fiber-optic and coaxial cables is known as ____________________. • Question 32 Which of the following are disadvantages of using fiber-optic cabling over copper media? • Question 33 ____________ is the simplest topology that consists of a permanent link between two endpoints. • Question 34 What are the contents of the data field in a frame? • Question 35 Two-way communication up to 10 km can be provided over a single strand of single-mode fiber by transmitting at a different wave length into the fiber from each end. • Question 36 With ____________, the signals are patterns of radio transmissions. • Question 37 LLC is implemented in hardware, and its implementation is independent of the software. • Question 38 Multiple devices can have the same MAC address. • Question 39 Indicate the appropriate order for the following ARP processes that occur when an entry is not found in a cached map of an ARP table. (1) A map is created in the ARP table (2) AN ARP request packet is sent out. (3) Layer 2 processes notify ARP that it needs a map. (4) If a device’s destination IP address matches the IP address in the request, it responds with an ARP reply. Selected Answer: (1), (3), (2), (4) • Question 40 A Switch Virtual Interface (SVI) must be enabled to provide IP host connectivity to the switch and permit remote switch administration. SVIs must also be configured to allow routing between VLANs. • Question 41 In 1998, the IEEE 802.3ac standard extended the maximum allowable frame size to be 1522 bytes in order to accommodate a technology called ____________________. • Question 42 In full-duplex communication, frames sent by the two connected end nodes cannot collide because the end nodes use two separate circuits in the network cable. • Question 43 Which files are loaded into RAM when a router is booted? • Question 44 Both routing tables of hosts and routers identify the destination network, the metric associated with the destination network, and the gateway to get to the destination network. • Question 45 Which of the following is false with respect to IPv6 extension headers (EH)? • Question 46 Which part of an IPv4 packet contains the Layer 4 segment information and the actual data? • Question 47 The ___________ is the device that routes traffic from the local network to devices on remote networks. • Question 48 What are the most common methods of accessing the CLI environment on a Cisco router? • Question 49 A router’s IOS is typically stored in flash memory and is copied into RAM for execution by the CPU during bootup. • Question 50 The IOS file for a Cisco router is stored in flash memory. • Question 51 UDP contains a sequence number in its header. • Question 52 According to the textbook, the session layer is responsible for establishing a temporary communication session between two applications and delivering data between them. • Question 53 Which of the following types of ports use numbers 0 to 1023? • Question 54 Which control flag in the TCP header is set by the TCP client to initiate a session with a destination host? • Question 55 The amount of data that a source can transmit before an acknowledgement must be received is called the _______________. • Question 56 Starting with a sequence number of 2000, if 5 segments of 1000 bytes each were received, an ACK number of ________ would be returned to the source. • Question 57 Which of the following fields indicates the number of segments that can be accepted at one time? • Question 58 A ______________ protocol is a protocol that keeps track of the state of the communication session. • Question 59 Which option contained in a Router Advertisement (RA) message indicates that the device should use the normal process of discovering and querying a DHCPv6 server to obtain all its addressing information, including an IPv6 global unicast address, a prefix length, a default gateway address, and the addresses of DNS servers. • Question 60 The address of the last usable host in a network is always 1 less than the network address. • Question 61 Which of the following is not a part of the structure of a global unicast address? • Question 62 The double colon can only be used once within an IPv6 address. • Question 63 Which part of the structure of a global unicast address is equivalent to the host portion of an IPv4 address? • Question 64 Which IPv6 addresses are equivalent to public IPv4 addresses in that they are globally unique and routable on the Internet? • Question 65 Which of the following is not a type of broadcast address? • Question 66 Which of the following is not a type of IPv6 address? • Question 67 Using an IPv4 network address of 192.168.2.0/26, what is the broadcast address in the first subnet (i.e. subnet[0])? • Question 68 Traffic cannot be forwarded between subnets without the use of a router. • Question 69 What is the maximum number of IP addresses that can be assigned to hosts on a local subnet that uses the 255.255.255.224 subnet mask? • Question 70 DHCP is generally the preferred method of assigning IP addresses to hosts on large networks because it reduces the burden on network support staff and virtually eliminates entry errors. • Question 71 You are given an IPv4 network address of 192.168.10.0/24 by your ISP. You need to subnet this network. You know that the subnet mask will be 255.255.255.252. What is the broadcast address of the first subnet (i.e. subnet[0])? • Question 72 The IP address 10.0.0.1 /24 is a network address. • Question 73 What is the network address for the host assigned to 172.16.4.35/24 ? • Question 74 The terms subnet and network are often used interchangeably. • Question 75 Which of the following is not true in a peer-to-peer network? • Question 76 Which of the following is NOT a type of message that can be sent to a web server? • Question 77 What is the IPv6 DHCP message that corresponds to the IPv4 DHCPDISCOVER message? • Question 78 With ________, mail is downloaded from the server to the client and then deleted from the server. • Question 79 The type of addressing used when the network administrator manually enters IP address information on network hosts is called _________ addressing. • Question 80 Which DHCP message is sent out to identify any available DHCPv4 servers on a network? • Question 81 Which DHCP message confirms to the client that the requested lease is finalized? • Question 82 Which protocol handles inbound mail delivery? • Question 83 A key network switch has failed because of excessive humidity. What type of physical threat caused the problem? • Question 84 According to the textbook, real-time applications require more planning and dedicated services (relative to other types of data) to ensure priority delivery of voice and video traffic. • Question 85 Which of the following protocols support delay-sensitive delivery to support streaming media? • Question 86 Authentication, authorization, and accounting (AAA) network security services provide the primary framework to set up access control on a network device. • Question 87 _________ firewalls reside on host computers and are not designed for LAN implementations. • Question 88 A _________ firewall is implemented by adding firewall functionality to an existing device, such as a router. • Question 89 What type of attack involves the disabling or corruption of networks, systems, or services? • Question 90 Which of the following firewall techniques prevents or allows access by specific application types based on port numbers? • Question 91 VoIP uses voice-enabled routers that convert analog voice from traditional telephone signals into IP packets. • Question 92 Which of the following elements are not considered when scaling a network? • Question 93 Which type of security threat involves breaking into a computer to destroy or alter data records? • Question 94 A(n) __________ firewall is a firewall that is built into a dedicated hardware device known as a security appliance. • Question 95 Which type of traffic should be given the highest priority on a network? • Question 96 Which of the following firewall techniques blocks unsolicited packets unless permitted specifically? : • Question 97 What is the order of steps recommended to mitigate a worm attack? • Question 98 Which type of security threat involves breaking into a computer to obtain confidential information? • Question 99 Which of the following are steps that should be taken to secure devices on which a new operating system has been installed? • Question 100 Which type of physical threat involves physical damage to servers, routers, switches, cabling, and workstations? [Show More]
Last updated: 1 year ago
Preview 1 out of 14 pages

Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Feb 06, 2020
Number of pages
14
Written in
Additional information
This document has been written for:
Uploaded
Feb 06, 2020
Downloads
0
Views
91

















.png)