Information Technology > QUESTIONS & ANSWERS > IT Security: Defense against the digital dark arts - Week 3 Already Passed (All)
IT Security: Defense against the digital dark arts - Week 3 Already Passed
Document Content and Description Below
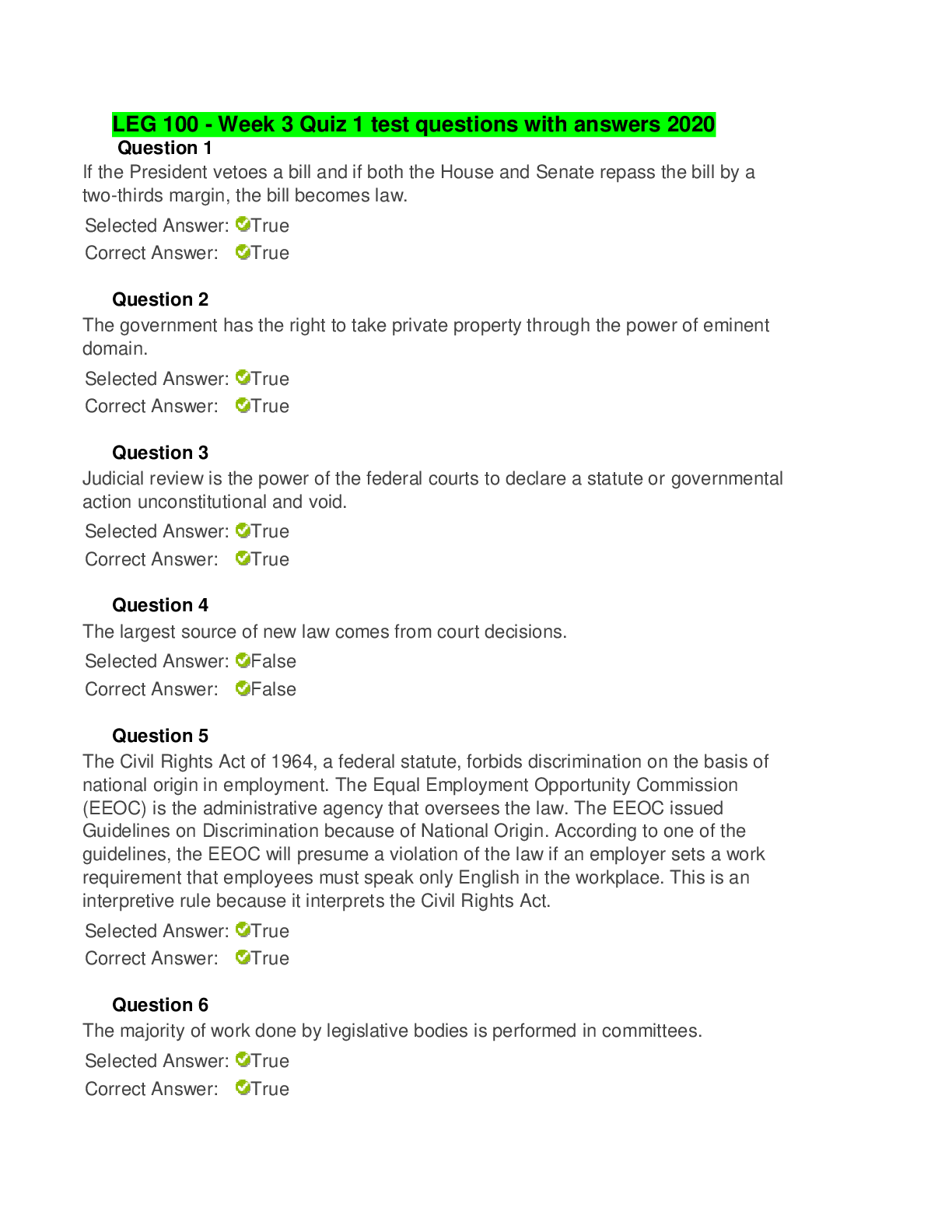
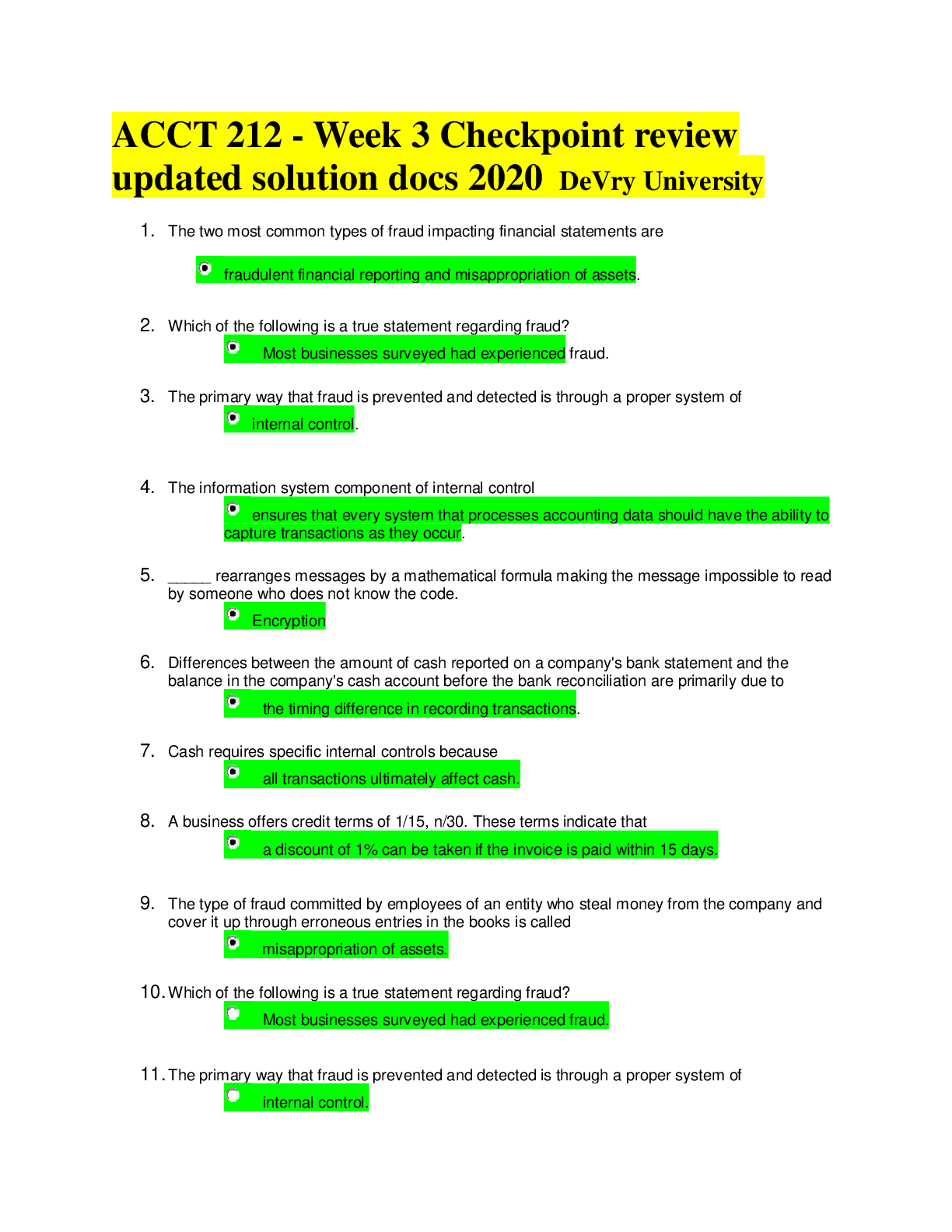
IT Security: Defense against the digital dark arts - Week 3 Already Passed How is authentication different from authorization? ✔✔Authentication is verifying an identity; Authorization is verify... ing access to a resource What are some characteristics of a strong password? Check all that apply, ✔✔At least eight characters long Includes number and special characters In a multi-factor authentication scheme, a password can be thought of as: ✔✔Something you know What are some drawbacks to using biometrics for authentication? Check all that apply. ✔✔Biometrics is impossible to change if compromised There are potential privacy concern In what way are U2F tokens more secure than OTP generators? ✔✔They're resistant to phishing attack What elements of a certificate are inspected when a certificate is verified? Check all that apply. ✔✔Trust of the signatory CA Not valid after and before date What is CRL? ✔✔Certificate Revocation List What are the names of similar entities that a Directory server organizes entities into? ✔✔Organizational Units True or false: The Network Access Server handles the actual authentication in a RADIUS scheme. ✔✔False True or false: Clients authenticate directly against the RADIUS server. ✔✔False What does a Kerberos authentication server issue to a client that successfully authenticates? ✔✔A ticket granting ticket What advantages does single sign-on offer? Check all that apply. ✔✔Reduces the time spent authenticating Reduces the total number of credentials What does OpenID provide? ✔✔Authentication delegation What role does authorization play? ✔✔It determines whether or not an entity has access to a resource What does OAuth provide? ✔✔Access Delegation How is auditing related to accounting? ✔✔Accounting is recording access and usage, while auditing is reviewing these records. Authentication is concerned with determining _______. ✔✔Identity Which of the following are valid multi-factor authentication factors? Check all that apply. ✔✔something you have and something you are, and something you know Security Keys are more ideal than OTP generators because they're resistant to _______ attacks. ✔✔Phishing In the three As of security, what is the process of proving who you claim to be? ✔✔Authentication Which of these passwords is the strongest for authenticating to a system? ✔✔P@w04d!$$L0N6 In a Certificate Authority (CA) infrastructure, why is a client certificate used? ✔✔To authenticate the server What is used to request access to services in the Kerberos process? ✔✔Ticket Granting tiket What are the benefits of using a Single Sign-On (SSO) authentication service? Check all that apply. ✔✔Reduces the time re-authenticating servers Reduces the total number of credentials all In the three As of security, which part pertains to describing what the user account does or doesn't have access to? ✔✔Authorization A(n) _____ defines permissions or authorizations for objects. ✔✔Access Control List Access control entries can be created for what types of file system objects? Check all that apply. ✔✔Files, Folders, and Programs [Show More]
Last updated: 1 year ago
Preview 1 out of 3 pages
Instant download
.png)
Instant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Oct 03, 2022
Number of pages
3
Written in
Additional information
This document has been written for:
Uploaded
Oct 03, 2022
Downloads
0
Views
47

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)

.png)

.png)
.png)









.png)
.png)
.png)
.png)