Medicine > QUESTIONS & ANSWERS > WGU Master's Course C726 - Cybersecurity Architecture and Engineering with complete solution (All)
WGU Master's Course C726 - Cybersecurity Architecture and Engineering with complete solution
Document Content and Description Below
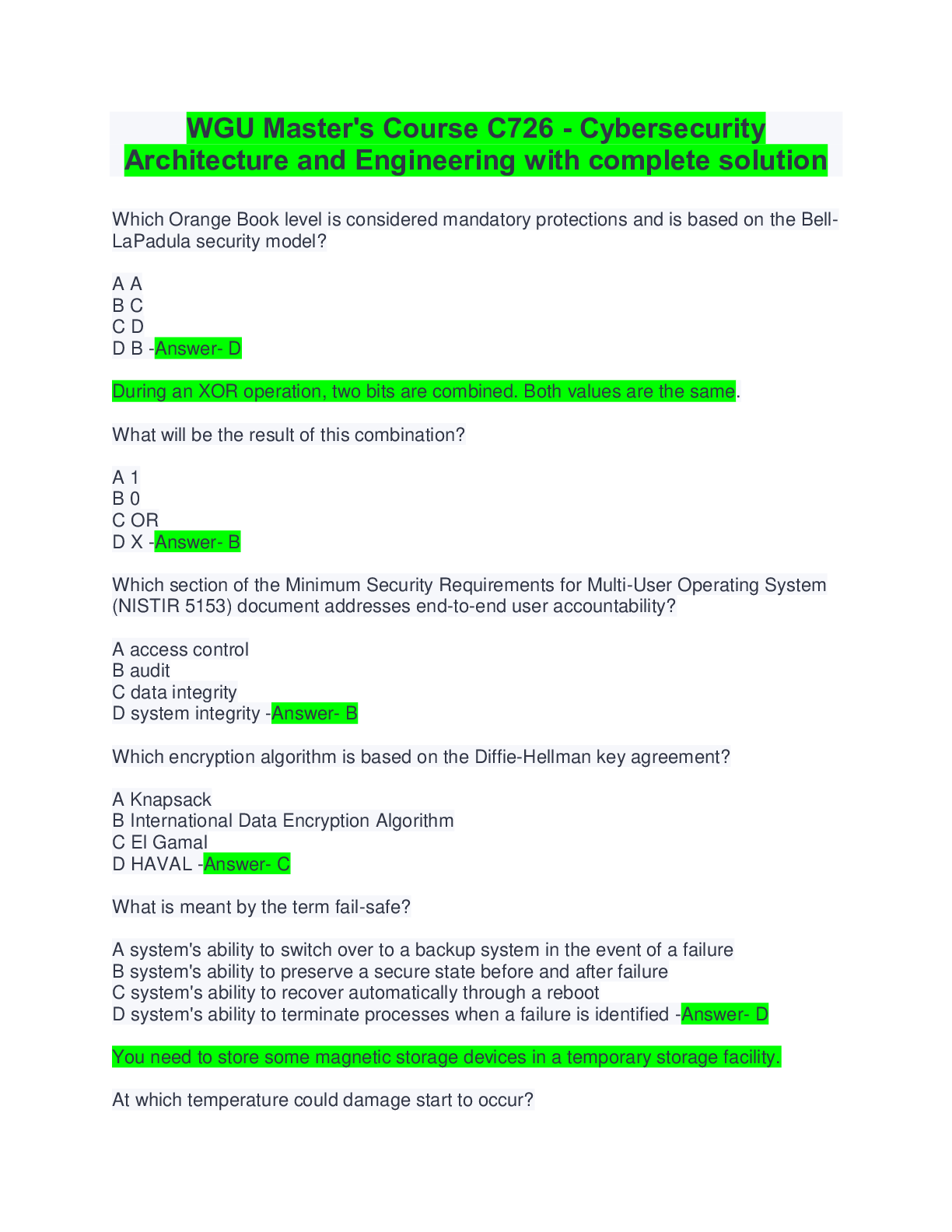
WGU Master's Course C726 - Cybersecurity Architecture and Engineering with complete solution Which Orange Book level is considered mandatory protections and is based on the Bell-LaPadula security m... odel? A A B C C D D B -Answer- D During an XOR operation, two bits are combined. Both values are the same. What will be the result of this combination? A 1 B 0 C OR D X -Answer- B Which section of the Minimum Security Requirements for Multi-User Operating System (NISTIR 5153) document addresses end-to-end user accountability? A access control B audit C data integrity D system integrity -Answer- B Which encryption algorithm is based on the Diffie-Hellman key agreement? A Knapsack B International Data Encryption Algorithm C El Gamal D HAVAL -Answer- C What is meant by the term fail-safe? A system's ability to switch over to a backup system in the event of a failure B system's ability to preserve a secure state before and after failure C system's ability to recover automatically through a reboot D system's ability to terminate processes when a failure is identified -Answer- D You need to store some magnetic storage devices in a temporary storage facility. At which temperature could damage start to occur? A 350 degrees Fahrenheit B 100 degrees Fahrenheit C 90 degrees Fahrenheit D 175 degrees Fahrenheit -Answer- B You need to decrypt a file that is encrypted using asymmetric encryption. What should be used to decrypt the file? A public key B plaintext C message digest D private key -Answer- D Which statement is true of the Rijndael algorithm? A Rijndael uses variable block lengths and variable key lengths. B Rijndael uses fixed block lengths and fixed key lengths. C Rijndael uses variable block lengths and fixed key lengths. D Rijndael uses fixed block lengths and variable key lengths. -Answer- A You are responsible for managing the virtual computers on your network. Which guideline is important when managing virtual computers? A Update the operating system and applications only on the host computer. B Implement a firewall only on the host computer. C Install and update the antivirus program only on the host computer. D Isolate the host computer and each virtual computer from each other. -Answer- D Given two messages, M1 and M2, what is the LEAST likely outcome when using the same one-way hash function, H, to encrypt the messages? A H(M1) = H(M2) B H(M1) is not equal to H(M2) C H(M1) > H(M2) D H(M1) < H(M2) -Answer- A Your organization has decided to implement the Diffie-Hellman asymmetric algorithm. Which statement is true of this algorithm's key exchange? A Authorized users exchange public keys over a secure medium. B Unauthorized users exchange public keys over a nonsecure medium. C Authorized users exchange secret keys over a nonsecure medium. D Authorized users need not exchange secret keys. -Answer- C Which processes control the flow of information in the lattice-based access control (LBAC) model? A access triple rule B least upper and greatest lower bound operators C simple security, star property, and strong star property rules D star (*) integrity and simple integrity axioms -Answer- B Management at your organization has recently become aware that the Internet of Things (IoT) movement has resulted in many security issues. They have asked that you identify some of the vulnerabilities presented by IoT from the following list: A insecure management Web interface B insufficient or lack of authentication C lack of transport encryption D insecure software/firmware E insufficient or lack of physical security F All of the above Which would apply? -Answer- F What is the best description of an execution domain? A memory space insulated from other running processes in a multiprocessing system B a communication channel between an application and the kernel in the TCB C components that fall outside the security perimeter of the TCB D an isolated area that is used by trusted processes when they are run in privileged state -Answer- D Which characteristics of a system are evaluated by the Trusted Computer System Evaluation Criteria (TCSEC)? (Choose TWO): A assurance B authenticity C functionality D response-time -Answer- AC Why should device driver files be digitally signed? A to record the installation timestamp B to ensure that they are not changed after installation C to ensure that they are from a trusted publisher D to ensure that they are installed by a trusted user -Answer- C Recently, your organization had a new heating and air conditioning system installed for your facility. Now, when the heat or air turns on, the lights in the facility dim for a small amount of time. What is occurring when the lights dim? A power brown-out B power black-out C power sag D power surge -Answer- C Which processes define the supervisor mode? A processes in the outer protection ring that have more privileges B processes that are executed in the inner protection rings C processes with no protection mechanism D processes that are executed in the outer protection rings -Answer- B To what does ISO 15408 refer? A TCSEC B ITSEC C Common Criteria D security policy -Answer- C Which type of password attack is often referred to as an exhaustive attack? A brute force attack B dictionary attack C spoofing attack D phishing attack -Answer- A Which type of water sprinkler system is NOT appropriate for a data processing environment? A deluge water sprinkler system B dry pipe water sprinkler system C wet pipe water sprinkler system D pre-action water sprinkler system -Answer- A Recently, management has become concerned that RFI is causing issues in your organization's facility. What can cause this type of interference? A electric motors B lightning C fluorescent lighting D electric wiring -Answer- C During a recent security audit, an outside security contractor has suggested that you trim back the landscaping around entrances. In addition, it has been suggested that you install CCTV at all entrances. Which facet of the Crime Prevention Through Environmental Design (CPTED) approach is being addressed? A territorial reinforcement B target hardening C natural surveillance D natural access control -Answer- C What is contained within an X.509 CRL? A serial numbers B digital certificates C private keys D public keys -Answer- A Which cipher type replaces the original text in a message with a different text? A stream cipher B transposition cipher C substitution cipher D block cipher -Answer- C Gaining unauthorized access to the data center by using another user's credentials when following them into the building is an example of which option? A intrusion B piggybacking C mantrap D turnstile -Answer- B Which of the following is NOT based on the Feistel cipher? A Skipjack B Diffie-Hellman C CAST-128 D Blowfish -Answer- B Your organization has implemented a public key infrastructure (PKI) for issuing certificates. Recently, your organization issued several certificates to a partner organization. You revoked the certificates today. However, management is concerned that the revocation request grace period will prevent the certificates from being revoked in a timely manner. Which statement is true of this period? A It relates to the maximum response time taken by the CA for a revocation. B It refers to the validity of a digital signature. C It refers to the time taken by a registration authority (RA) to register a user. D It refers to the grace period for a backup CA server to update itself. -Answer- A What should you implement on the client computers to best manage the encryption keys, passwords, drive encryption, and digital rights for users? A VM B DNS C PKI D TPM -Answer- D Which component is NOT a part of the protection profile information used by the Common Criteria to evaluate products? A product test results B EAL rating C assurance requirements D functionality requirements -Answer- A Which description applies to a surge? A momentary low voltage B prolonged power outage C momentary power outage D prolonged power supply below normal voltage E prolonged high voltage above the normal level -Answer- E Which location would be MOST appropriate for the data center of a company's information processing facility? A the facility's top floor B the facility's ground floor C the facility's basement D the facility's core -Answer- D [Show More]
Last updated: 1 year ago
Preview 1 out of 17 pages
Reviews( 0 )
Recommended For You
Information Technology> QUESTIONS & ANSWERS > WGU Master's Course C726 - Cybersecurity Architecture and Engineering (All)

WGU Master's Course C726 - Cybersecurity Architecture and Engineering
WGU Master's Course C726 - Cybersecurity Architecture and Engineering Which Orange Book level is considered mandatory protections and is based on the BellLaPadula security model? A A B C C D D...
By Nutmegs , Uploaded: Aug 19, 2022
$10
Business> QUESTIONS & ANSWERS > CLM 031 EXAM (All)

CLM 031 EXAM
CLM 031 = 100% Question 1: 5b Select the statement that is correct concerning performance work statement (PWS) requirements: - All answers are correct. - PWS should describe requirements necessary...
By Book Worm, Certified , Uploaded: Nov 03, 2022
$5
*NURSING> QUESTIONS & ANSWERS > PHIL 347 Week 6 Checkpoint Quiz. Score 100/100 (All)
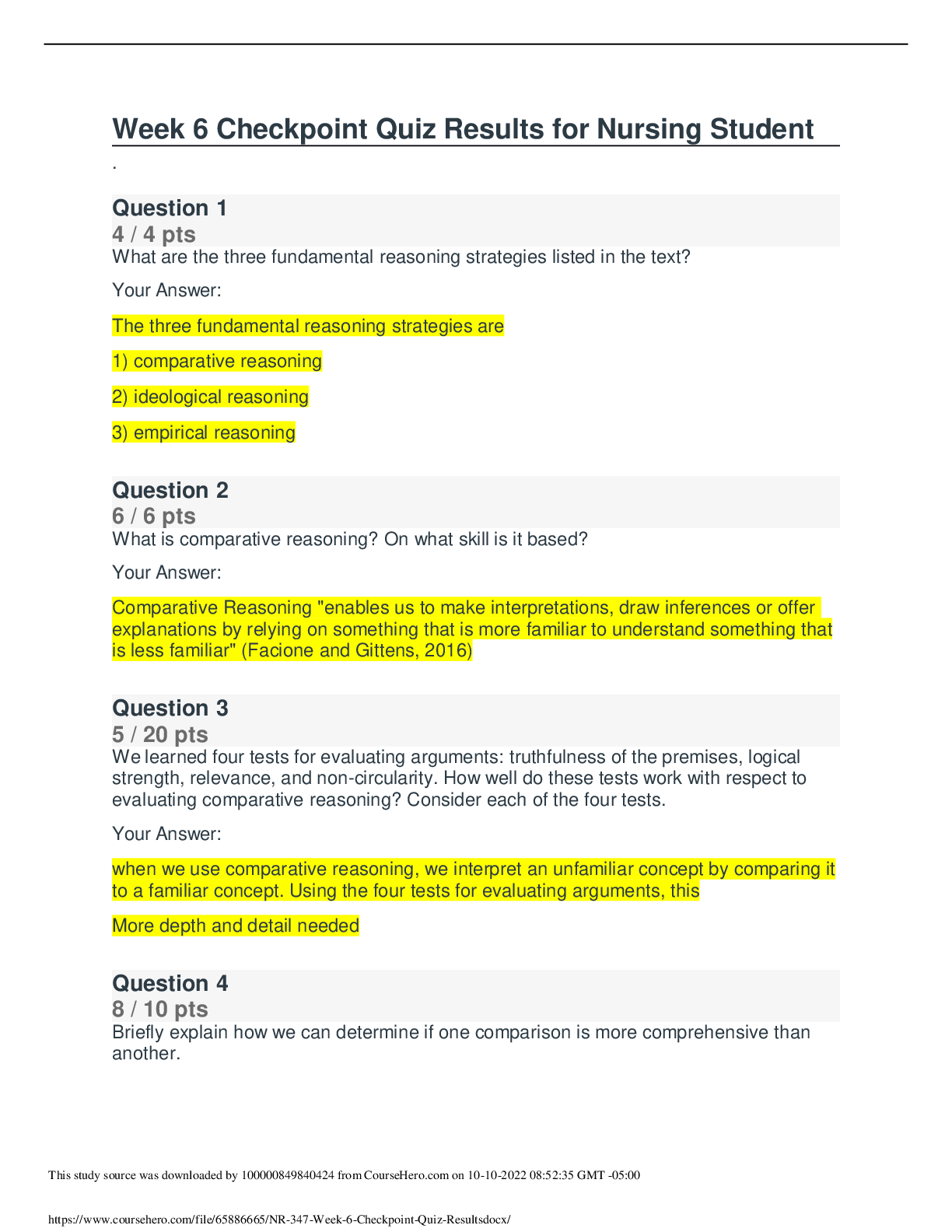
PHIL 347 Week 6 Checkpoint Quiz. Score 100/100
Question: What are the three fundamental reasoning strategies listed in the text? Question: What is comparative reasoning? On what skill is it based? Question: We learned four tests for evaluating...
By Amanda Rosales , Uploaded: Mar 24, 2021
$7
Business> QUESTIONS & ANSWERS > BUSINESS 1007 (All)
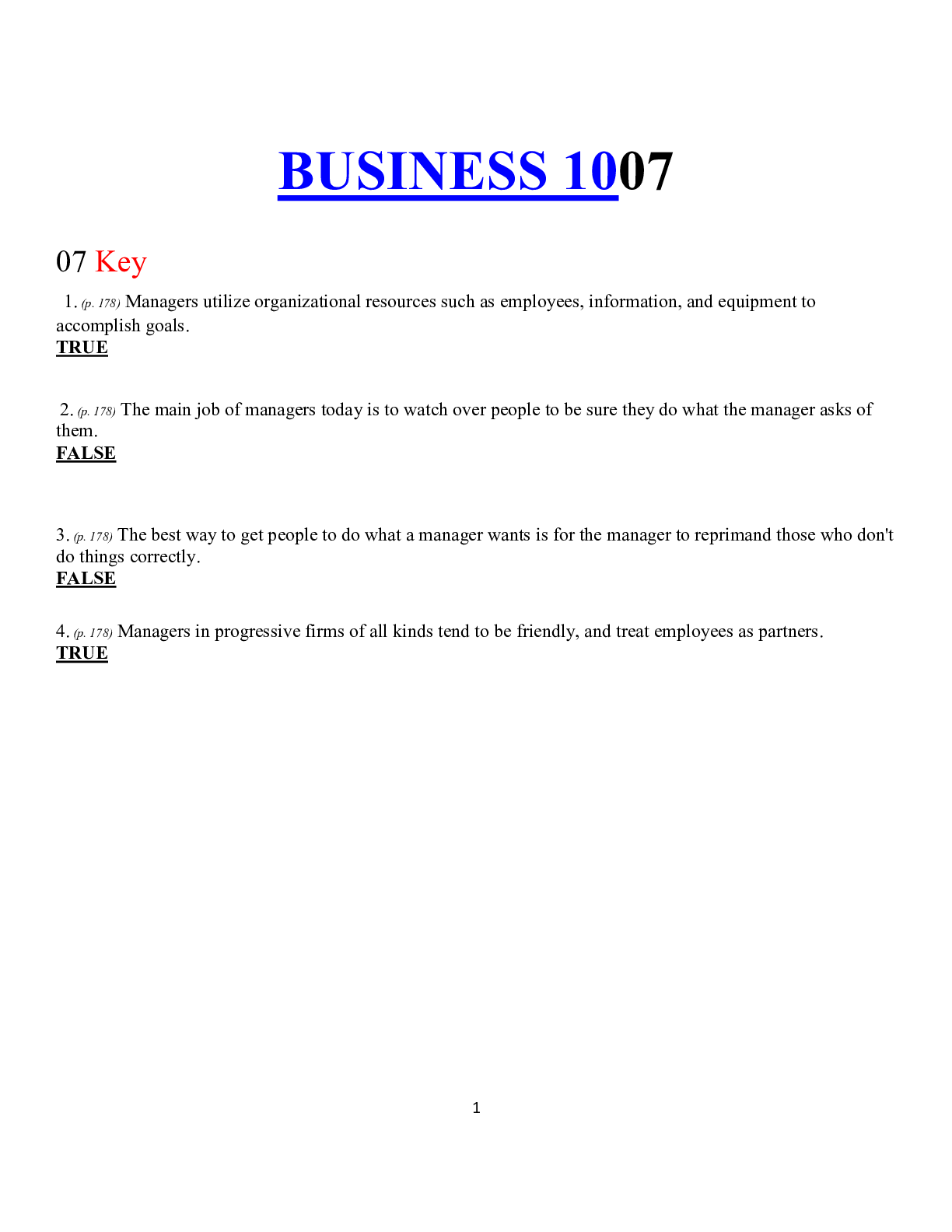
BUSINESS 1007
BUSINESS 1007 07 Key 1. (p. 178) Managers utilize organizational resources such as employees, information, and equipment to accomplish goals. 2. (p. 178) The main job of managers today is to w...
By Kirsch , Uploaded: Oct 19, 2019
$6
Anthropology> QUESTIONS & ANSWERS > KOR 352 FA19 101 week 8 Quiz. Already Graded A (All)

KOR 352 FA19 101 week 8 Quiz. Already Graded A
KOR 352 FA19 101: Week 8 Quiz Question 1 (0.25 points) Which of the following is not true of Kim and Finch’s observations during their field research in South Korea from 1997 to 2000? Question 1 o...
By Kirsch , Uploaded: Oct 17, 2019
$9
E-Commerce> QUESTIONS & ANSWERS > ESOC 316 Digital Commerce - University Of Arizona. Midterm Quiz. 20 Q&A. 100% Score (All)
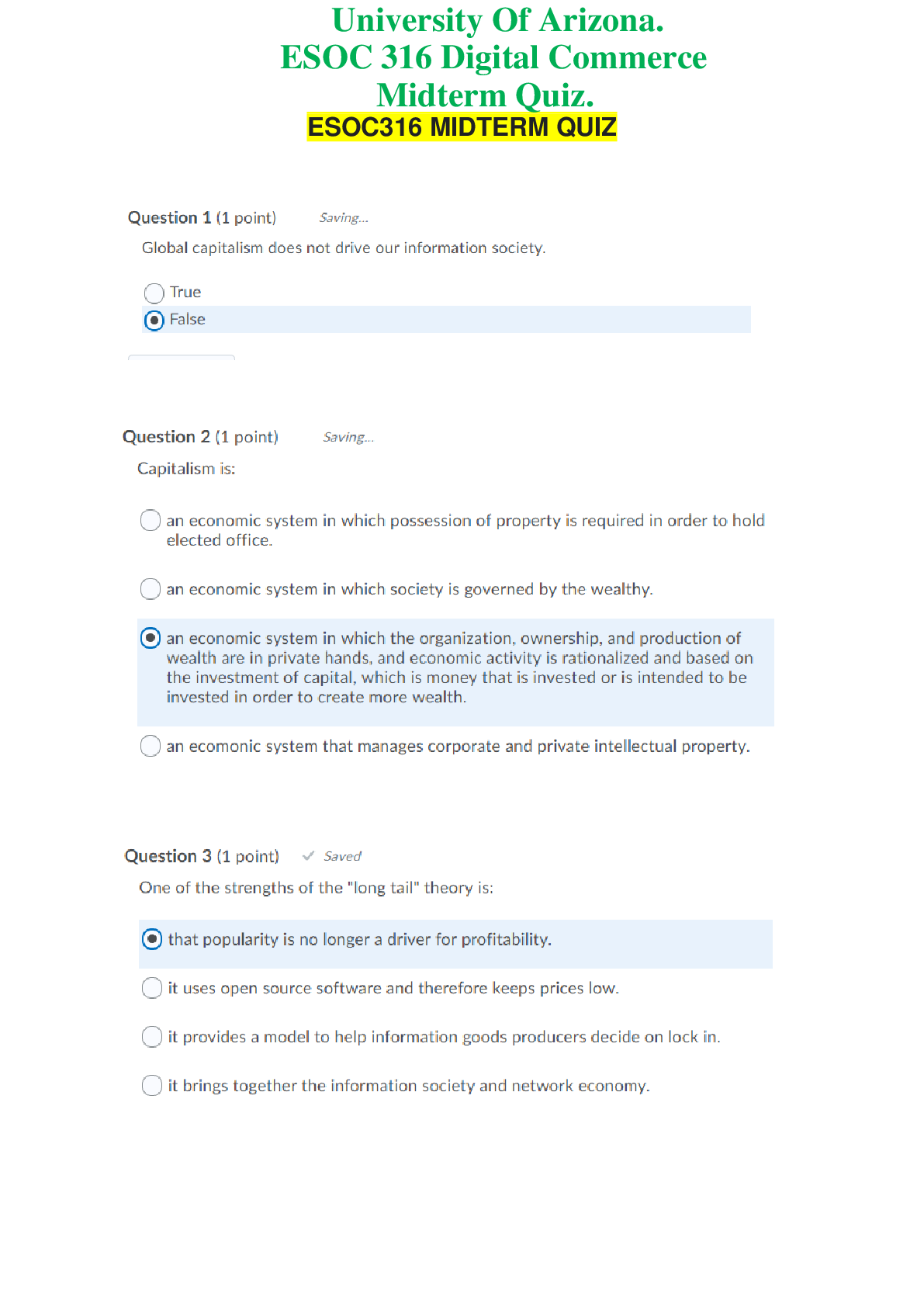
ESOC 316 Digital Commerce - University Of Arizona. Midterm Quiz. 20 Q&A. 100% Score
ESOC 316 Digital Commerce - University Of Arizona. Midterm Quiz. 20 Q&A. 100% Score ESOC316 MIDTERM QUIZQuestion 6 (1 point) Saved Information has several properties that make information goods...
By Kirsch , Uploaded: Oct 15, 2019
$9.5
Marketing> QUESTIONS & ANSWERS > Marketing Management Chapter 2 to Chapter 10 Q&A (All)

Marketing Management Chapter 2 to Chapter 10 Q&A
Chapter 2 to Chapter 10 Chapter 2: Developing Marketing Strategies and Plans GENERAL CONCEPT QUESTIONS Multiple Choice 66 Chapter 1: Marketing: Managing Profitable Customer Relationships...
By Kirsch , Uploaded: Oct 14, 2019
$10
Marketing> QUESTIONS & ANSWERS > MKT 530 Customer Relationship Management. 155 Questions and Answers (All)

MKT 530 Customer Relationship Management. 155 Questions and Answers
MKT 530 All Questions and Answers MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question. 1) As the manager of an organization that is att...
By Kirsch , Uploaded: Oct 14, 2019
$10
Art> QUESTIONS & ANSWERS > MAS 337 Exam 1. Graded A (All)

MAS 337 Exam 1. Graded A
MAS 337 Exam 1 Match the son with its corresponding region. 1.Oaxaca 2.Veracruz 3.Michoacan 4.Jalisco 5.Hidalgo 1. Son istemeno 2. Son Jarocho 3. Son Abajeno 4. Son Jalisciense 5. Son Huast...
By Kirsch , Uploaded: Oct 14, 2019
$6
Art> QUESTIONS & ANSWERS > MUS 337 Final Exam Graded 100%. (All)

MUS 337 Final Exam Graded 100%.
MUS 337 Final Daisy Moreno-Cota Fri Dec 11 12:59:42 PST 2015 Tone or aural color Volume and articulation of sounds Frequency of the tone Phonic structure or relationships between the sounds Dura...
By Kirsch , Uploaded: Oct 12, 2019
$9
Document information
Connected school, study & course
About the document
Uploaded On
Sep 22, 2022
Number of pages
17
Written in
Additional information
This document has been written for:
Uploaded
Sep 22, 2022
Downloads
0
Views
64






