Information Technology > QUESTIONS & ANSWERS > Georgia Institute Of Technology ISYE 6501 week 2 hw solutions Introduction To Analytics Modeling - G (All)
Georgia Institute Of Technology ISYE 6501 week 2 hw solutions Introduction To Analytics Modeling - GTX ISYE 6501
Document Content and Description Below
Question 1 Using the same data set as Homework 1 Question 2 use the ksvm or kknn function to find a good classifier: (a) using cross-validation for the k-nearest-neighbors model; and (b) splitting... the data into training, validation, and test data sets. Question 2 Describe a situation or problem from your job, everyday life, current events, etc., for which a clustering model would be appropriate. List some (up to 5) predictors that you might use. Question 3 The iris data set contains 150 data points, each with four predictor variables and one categorical response. The predictors are the width and length of the sepal and petal of flowers and the response is the type of flower. The data is available from the R library datasets and can be accessed with iris once the library is loaded. It is also available at the UCI Machine Learning Repository (https://archive.ics.uci.edu/ml/datasets/Iris ). The response values are only given to see how well a specific method performed and should not be used to build the model. Use the R function kmeans to cluster the points as well as possible. Report the best combination of predictors, your suggested value of k, and how well your best clustering predicts flower type [Show More]
Last updated: 1 year ago
Preview 1 out of 7 pages

Reviews( 0 )
Recommended For You
History> QUESTIONS & ANSWERS > ISYE 6501 Midterm 2. Complete Solutions - Introduction To Analytics Modeling - GTX ISYE 6501 (All)
ISYE 6501 Midterm 2. Complete Solutions - Introduction To Analytics Modeling - GTX ISYE 6501
90 Minute Time Limit Instructions Work alone. Do not collaborate with or copy from anyone else. You may use any of the following resources: One sheet (both sides) of handwritten (not photocopied o...
By bundleHub Solution guider , Uploaded: Jul 13, 2022
$10
History> QUESTIONS & ANSWERS > Complete Solutions - Introduction To Analytics Modeling - GTX ISYE 6501 (All)

Complete Solutions - Introduction To Analytics Modeling - GTX ISYE 6501
For each of the following five questions, select the probability distribution that could best be used to model the described scenario. Each distribution might be used, zero, one, or more than one ti...
By bundleHub Solution guider , Uploaded: Jul 13, 2022
$10
Engineering> QUESTIONS & ANSWERS > ISYE6501 Week 2 HW Latest 2022 (All)

ISYE6501 Week 2 HW Latest 2022
ISYE6501 Week 2 HW Question 4.1 At my job we use clustering in an image system to understand the minerals that are coming into our processing facility. Comparing the images to known mineral images,...
By Nutmegs , Uploaded: May 20, 2022
$9
Engineering> QUESTIONS & ANSWERS > HomeWork #1 EDX GTx: ISYE6501x - Introduction to Analytics Modeling (All)

HomeWork #1 EDX GTx: ISYE6501x - Introduction to Analytics Modeling
HomeWork #1 EDX GTx: ISYE6501x - Introduction to Analytics Modeling Mónica Rojas May 17, 2020 Table of Contents Results...............................................................................
By Nutmegs , Uploaded: May 20, 2022
$9
Engineering> QUESTIONS & ANSWERS > Intro to Analytics Modeling(ISYE6501) HW2 (All)

Intro to Analytics Modeling(ISYE6501) HW2
Intro to Analytics Modeling(ISYE6501) HW2 Question 4.1 Describe a situation or problem from your job, everyday life, current events, etc., for which a clustering model would be appropriate. List so...
By Nutmegs , Uploaded: May 20, 2022
$7.5
Engineering> QUESTIONS & ANSWERS > ISYE 6501: Introduction to Analytics Modeling Homework 2 (All)

ISYE 6501: Introduction to Analytics Modeling Homework 2
Question 4.1 – Clustering Models Describe a situation or problem from your job, everyday life, current events, etc., for which a clustering model would be appropriate. List some (up to 5) predictors...
By Nutmegs , Uploaded: May 20, 2022
$7
Engineering> QUESTIONS & ANSWERS > ISYE 6501: Introduction to Analytics Modeling Homework 3 (All)

ISYE 6501: Introduction to Analytics Modeling Homework 3
Overview This week’s lesson involves data preparation, including outlier identification, handling outliers, and an introduction to change detection. Data preparation involves inspecting data visual...
By Nutmegs , Uploaded: May 20, 2022
$8.5
Engineering> QUESTIONS & ANSWERS > KSM GTx: ISYE6501x Introduction to Analytics Modeling Week 13: Homework 12 (All)
KSM GTx: ISYE6501x Introduction to Analytics Modeling Week 13: Homework 12
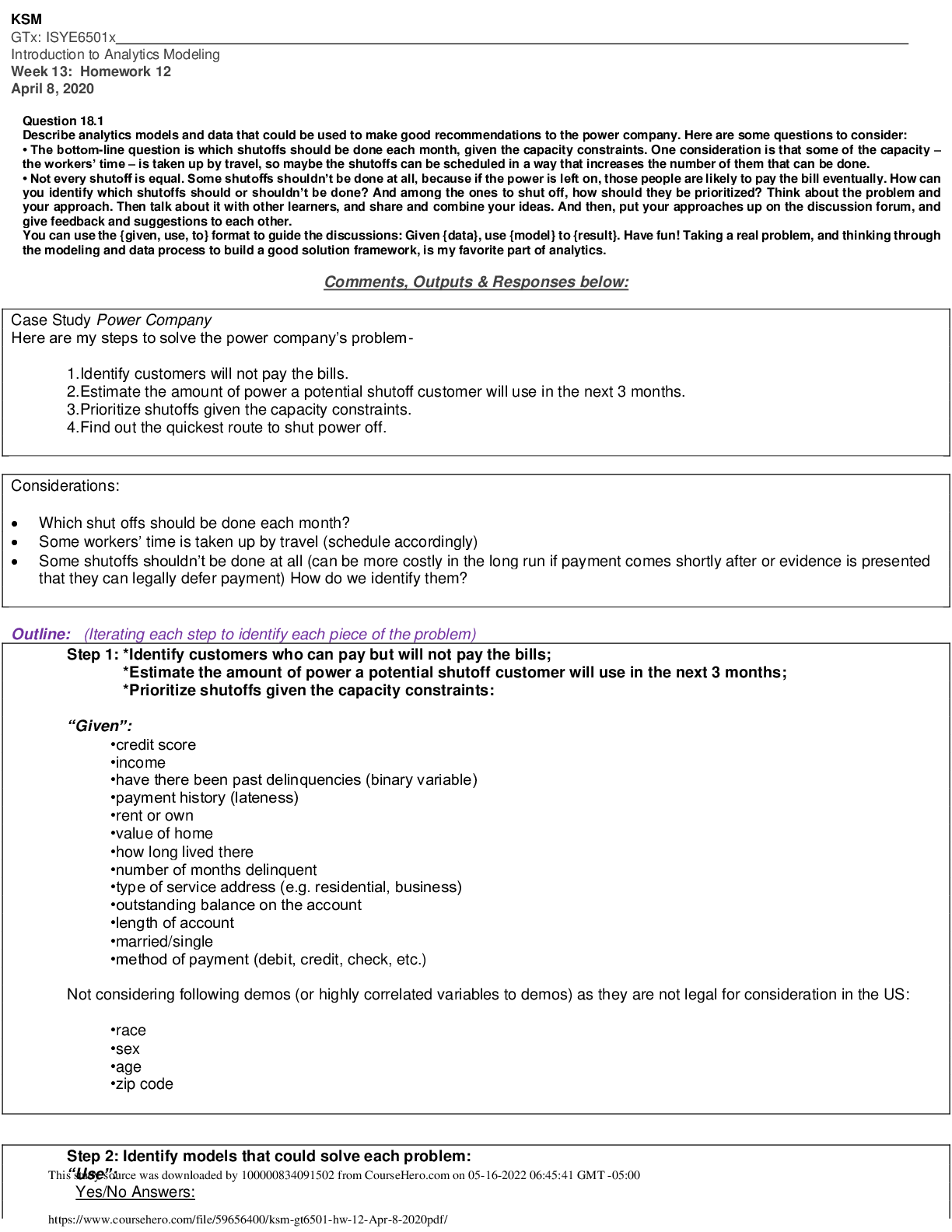
KSM GTx: ISYE6501x Introduction to Analytics Modeling Week 13: Homework 12 April 8, 2020 Question 18.1 Describe analytics models and data that could be used to make good recommendations to the p...
By Nutmegs , Uploaded: May 19, 2022
$7.5
Information Technology> QUESTIONS & ANSWERS > Georgia Institute Of Technology ISYE 6501 Homework 7 Complete Solutions - Introduction To Analytics Modeling - GTX ISYE 6501 (All)
Georgia Institute Of Technology ISYE 6501 Homework 7 Complete Solutions - Introduction To Analytics Modeling - GTX ISYE 6501
Georgia Institute Of Technology ISYE 6501 Homework 7 Complete Solutions - Introduction To Analytics Modeling - GTX ISYE 6501
By Tessa , Uploaded: May 13, 2022
$10
Information Technology> QUESTIONS & ANSWERS > Georgia Institute Of Technology ISYE 6501 Week 1 Homework Complete Solution (All)

Georgia Institute Of Technology ISYE 6501 Week 1 Homework Complete Solution
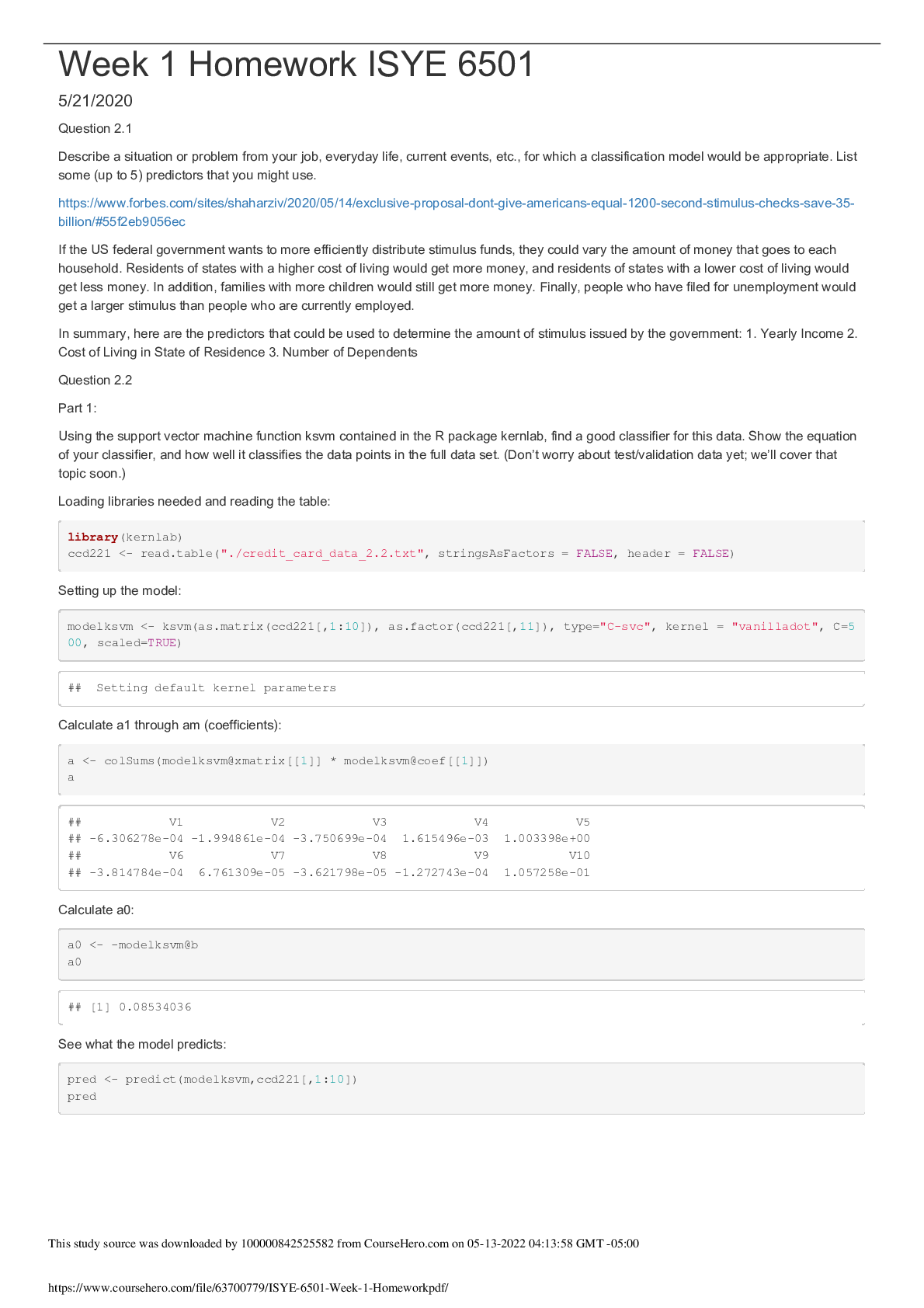
In my current job, I am responsible for understanding my company’s customer experience feedback when processing an insurance claim on their mobile device. This feedback is typically in the form of a...
By Tessa , Uploaded: May 13, 2022
$10
Document information
Connected school, study & course
About the document
Uploaded On
May 13, 2022
Number of pages
7
Written in
Additional information
This document has been written for:
Uploaded
May 13, 2022
Downloads
0
Views
86